This feature allows firewall administrators to create a custom LDAP group, which is defined by a search filter based on attributes. This feature eliminates having to involve the AD administrator in creating specific user groups. These custom LDAP groups can then be utilized in the firewall security policy.
Now, by using the relevant attributes to filter out users, adding or changing user groups in AD is no longer necessary (a process frequently unavailable to firewall administrators).
The configuration is found under Device > User Identification > Group Mapping Settings, as seen in the example below :
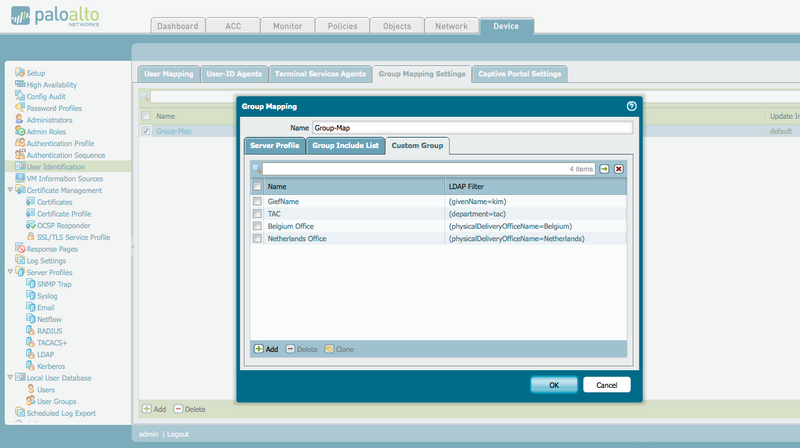
If a custom user group name conflicts with an existing AD group, then the custom group takes precedence!
After you define your groups list, you can use the following command to confirm that the new group exists. Note that the asterisk marks Custom Groups.
> show user group list
netherlands office *
belgium office *
tac *
giefname *
cn=domain admins,cn=users,dc=pantac,dc=lab
Total: 5
* : Custom Group
Use the following command to verify the membership of a group:
> show user group name giefname
source type: service
Group type:Custom
source: Group-Map
[1 ] pantac\kwens
After you have the groups defined, you can use them in a security policy, as shown in the example:
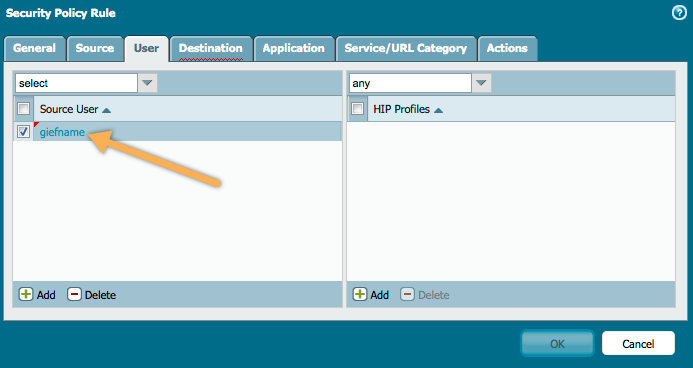
In order to make this work, make sure you know the attribute name for the field you want to filter on. If you are not sure about the name, use ADSI to view the user object attributes:
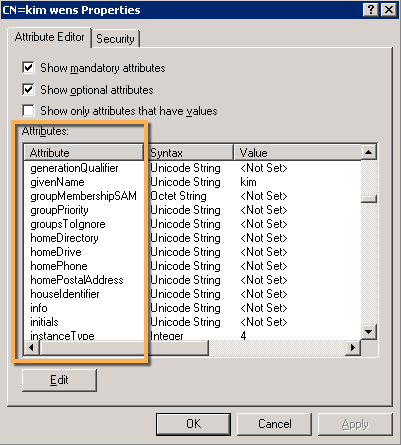
Some of the attribute names are tricky and others are self-explanatory. Below are just a few examples:
- City = l
- Office = physicalDeliveryOfficeName
- Department = department
- Last Name = sn
- First Name = givenName
Alternatively, you can check out the following site for an alphabetical list of all attributes:
Attributes for Active Directory users
If you are using a service route for group mapping traffic, then configure the LDAP service for your desired interface, as shown below :
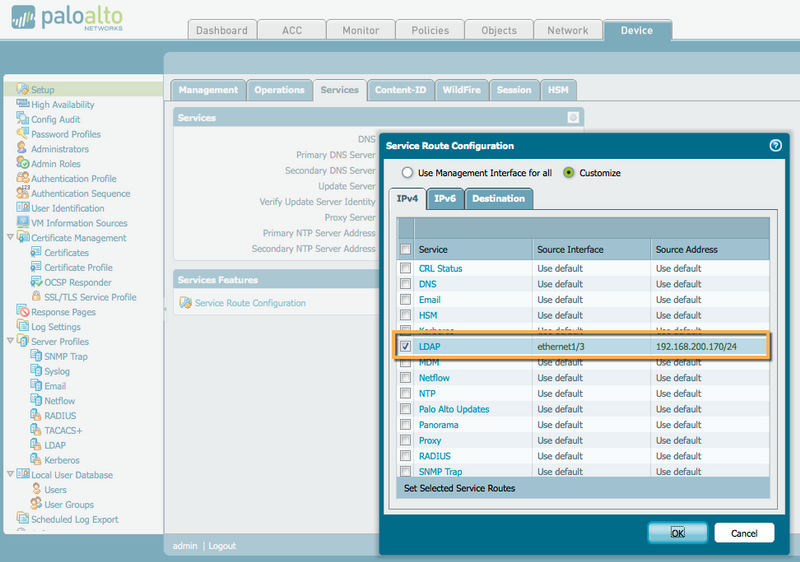
Please leave a comment or a like if you've found this information helpful.
Thanks!
-Kim