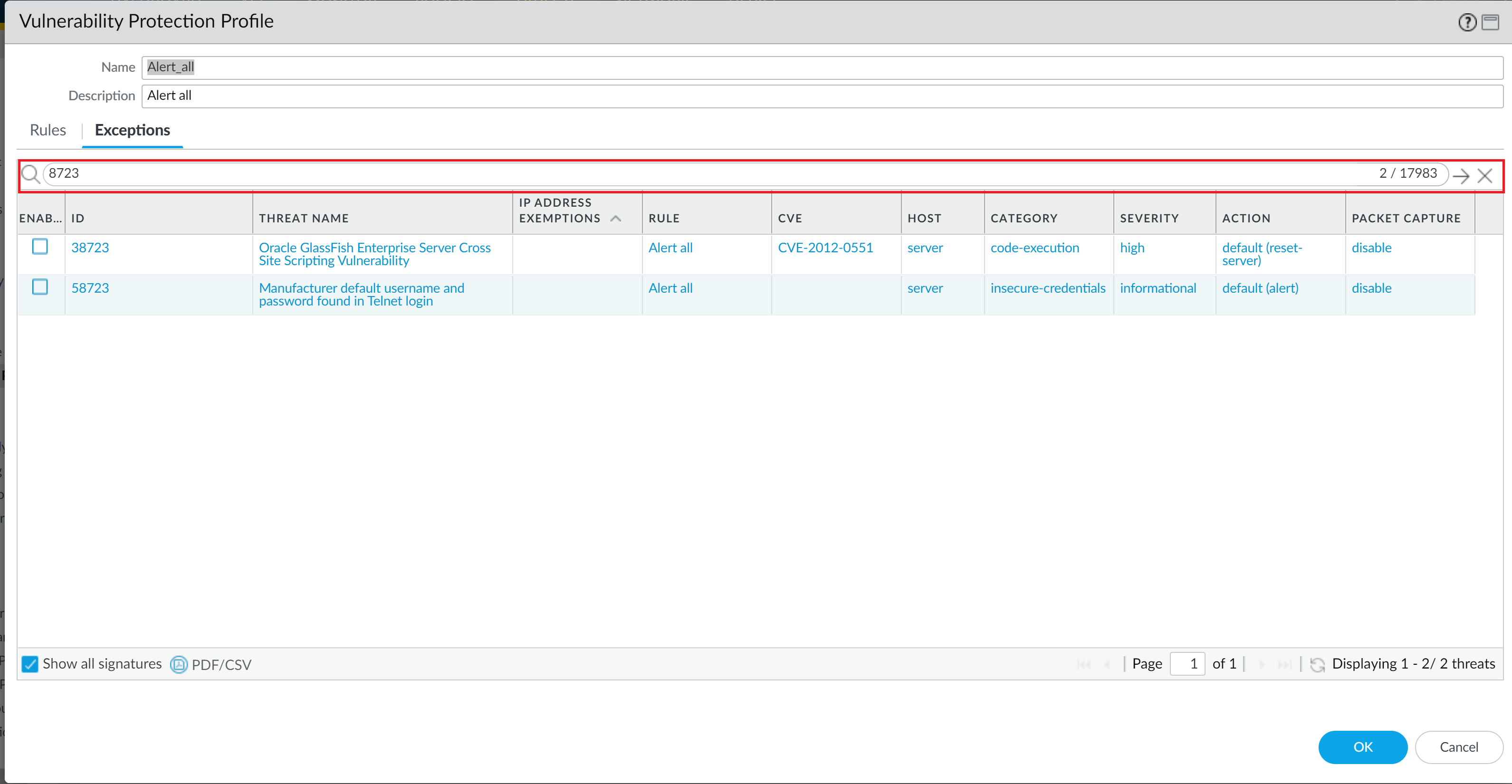
Unable to locate threat ID 8723 for a vulnerability protection exception.
13621
Created On 07/06/22 01:52 AM - Last Modified 07/06/22 03:14 AM
Symptom
- The Threat Vault (https://threatvault.paloaltonetworks.com/) classifies the signature as "Vulnerability Protection Signatures".
- Unable to locate any threat IDs listed below to create an exception in the vulnerability protection profile.
Threat-ID 8721 This event detects the source or destination address of the network packet is defined as an unspecified address or an address reserved for future definition and use as specified in RFC 3513 for IPv6.
Threat-ID 8722 This event detects TCP split handshake, where both a client and server of a TCP connection send a SYN packet to each other simultaneously.
Threat-ID 8723 This event detects a TCP SYN packet with payload, and a TCP fast open option is not present.
Threat-ID 8724 This event detects a TCP SYN-ACK packet with payload, and a TCP fast open option is not present.
Threat-ID 8725 This event detects and strips the TCP Fast Open option (and data payload, if any) from the TCP SYN or SYN-ACK packet during a TCP three-way handshake.
Threat-ID 8726 This event detects the presence of fragmented IP packets.
Threat-ID 8727 This event detects attempts at spoofing of IP address.
Threat-ID 8728 This event detects attempts to launch a ping of death DoS attack.
Threat-ID 8729 This event detects the presence of ICMP Packets that are larger than 1024 bytes.
Threat-ID 8730 This event detects the presence of ICMP fragments.
Threat-ID 8731 This event detects the presence of an error message embedded within ICMP packets.
Threat-ID 8732 This event is triggered when encountering a TCP packet which does not belong to an existing session. Any new session is expected to begin with a SYN packet and dropped if not so.
Threat-ID 8723 This event detects a TCP SYN packet with payload, and a TCP fast open option is not present.
Threat-ID 8724 This event detects a TCP SYN-ACK packet with payload, and a TCP fast open option is not present.
Threat-ID 8725 This event detects and strips the TCP Fast Open option (and data payload, if any) from the TCP SYN or SYN-ACK packet during a TCP three-way handshake.
Threat-ID 8726 This event detects the presence of fragmented IP packets.
Threat-ID 8727 This event detects attempts at spoofing of IP address.
Threat-ID 8728 This event detects attempts to launch a ping of death DoS attack.
Threat-ID 8729 This event detects the presence of ICMP Packets that are larger than 1024 bytes.
Threat-ID 8730 This event detects the presence of ICMP fragments.
Threat-ID 8731 This event detects the presence of an error message embedded within ICMP packets.
Threat-ID 8732 This event is triggered when encountering a TCP packet which does not belong to an existing session. Any new session is expected to begin with a SYN packet and dropped if not so.
Environment
- Palo Alto Networks Firewalls.
- PAN-OS 8.1.0 and later versions.
- PAN-OS 9.1.0 and later versions.
- PAN-OS 10.0.0 and later versions.
- PAN-OS 10.1.0 and later versions.
- PAN-OS 10.2.0 and later versions.
Cause
- Although these threat IDs are identified as "Vulnerability Protection Signatures", all signatures ID in the ranges between 8700-8799 are associated with Packet Based Attacks Protections available in the "Zone Protection" profiles.
Resolution
- This is the expected behavior. Exceptions for these signatures are not to be found under the "Vulnerability Protection Profile".
- There are no threat exceptions for signatures related to Packet Based Protections. Only "Source Address Exclusion" is optional for "Reconnaissance Protection".
Additional Information
- What are the Threat IDs for Packet Based Attacks associated with Zone Protection?
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u000000wkqxCAA