How to Embed App-Embedded Defender into AWS Fargate tasks in Prisma Cloud Compute?
19912
Created On 12/08/21 07:32 AM - Last Modified 06/11/25 20:27 PM
Objective
How to Embed App-Embedded Defender into Fargate tasks in Prisma Cloud Compute?
Environment
- Prisma Cloud Compute
- AWS
Procedure
Prior going through the configuration steps, Refer to the "additional Information" to confirm the prerequisites

Creating a task definition in AWS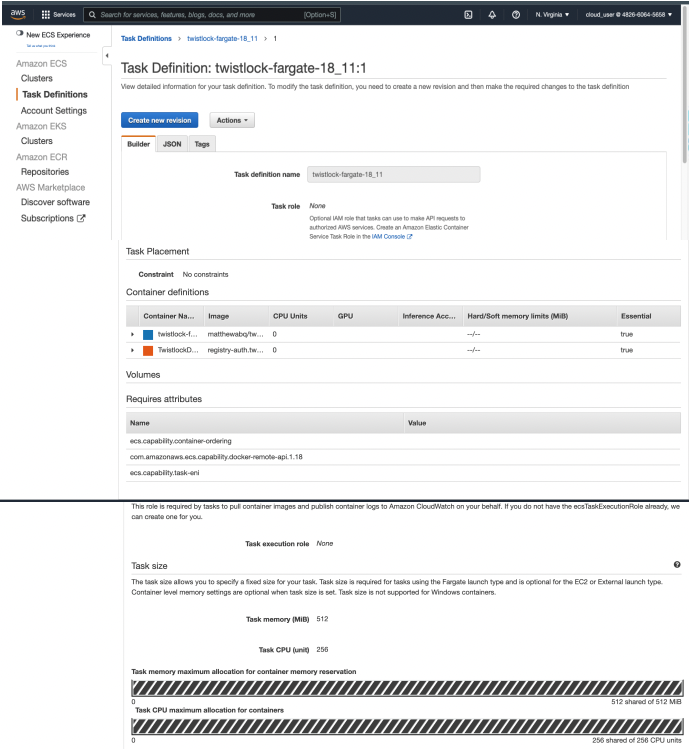
Testing the Task
4.5 Click Next step
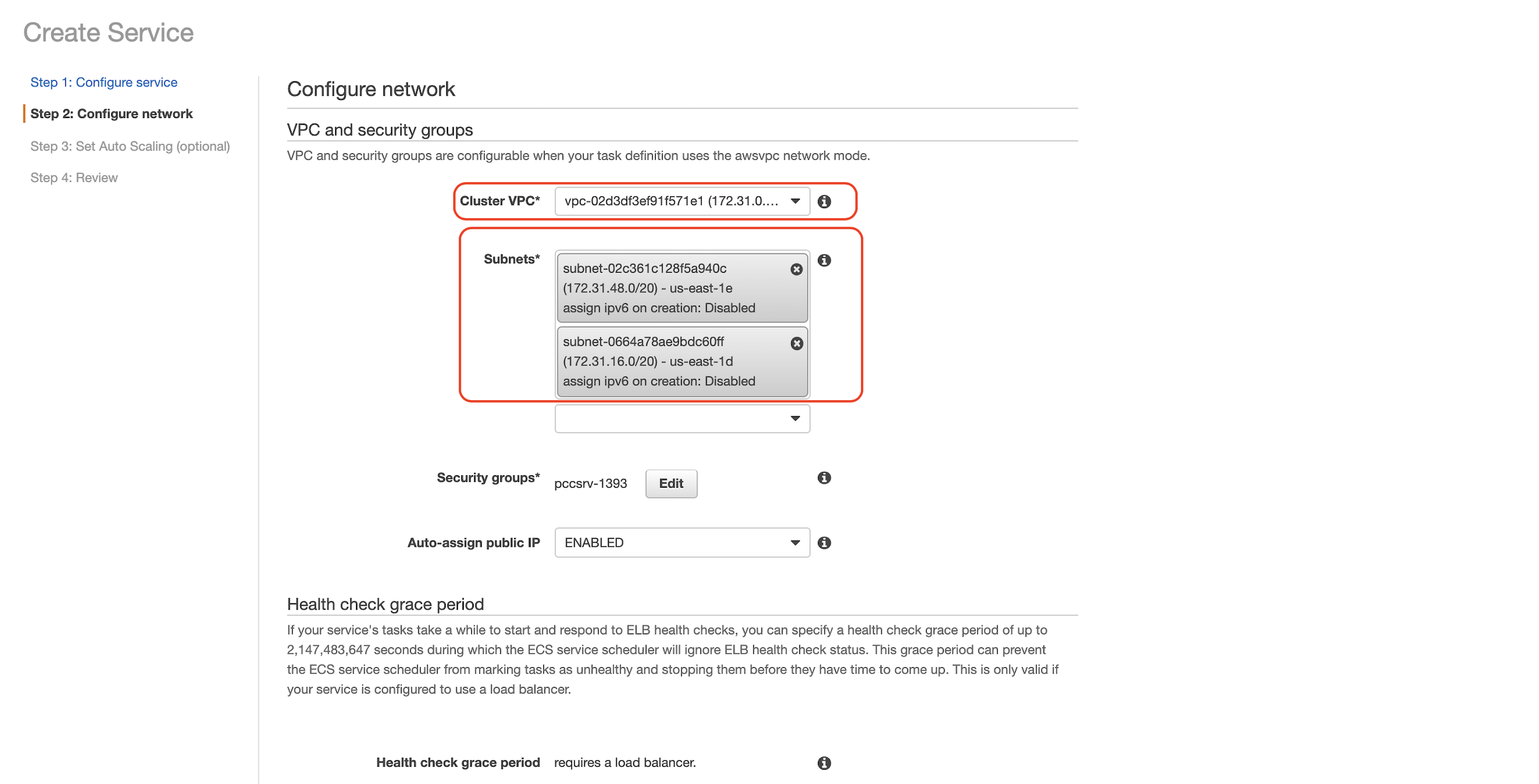
4.6 Select a Cluster VPC and Subnets then click Next step
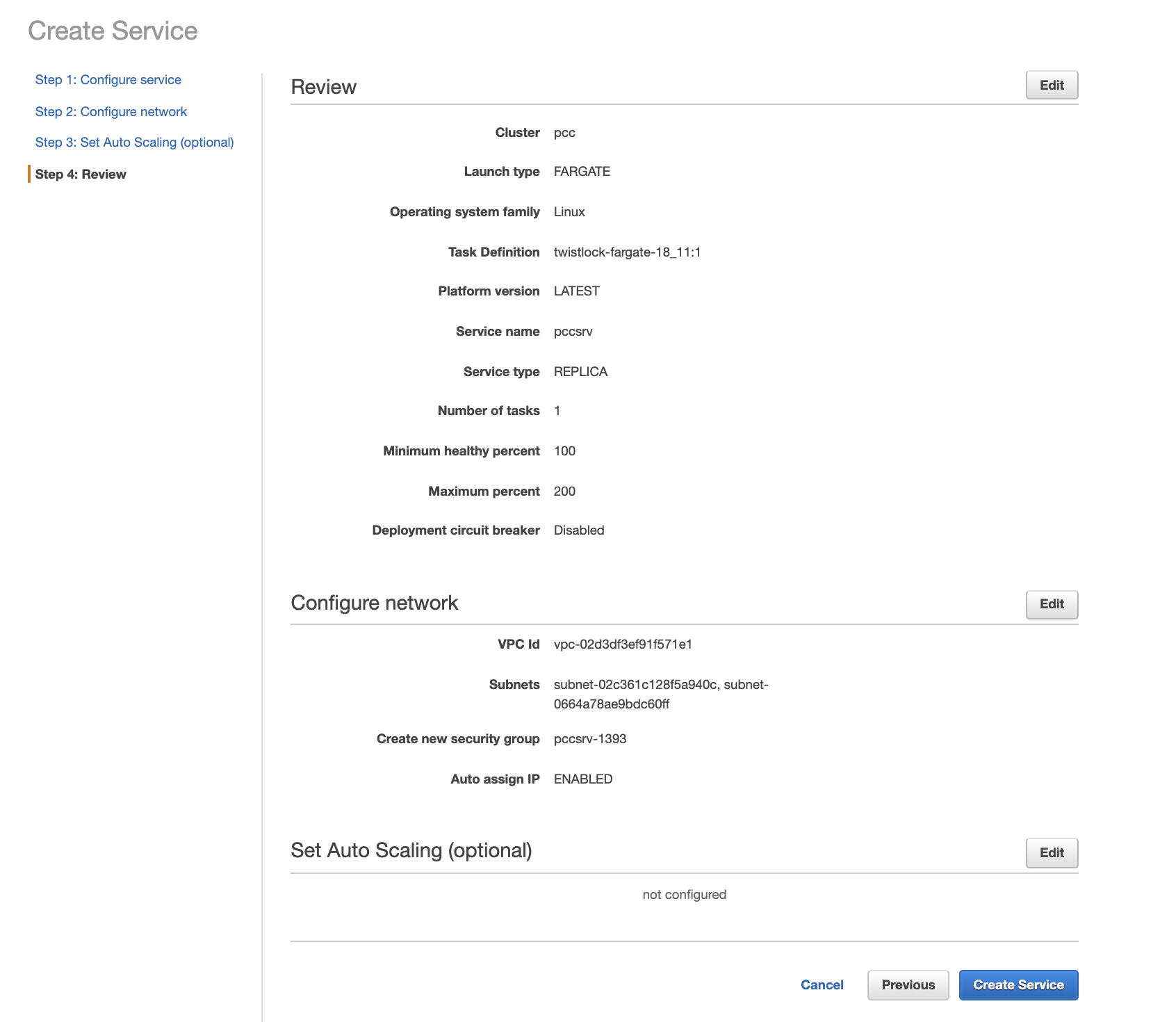
5. Review your settings, then click Create Service
6. View the defender in the Prisma Cloud Console: Go to Manage > Defenders > Manage Defenders and search the fargate task by adding the filters Fargate and Status: Connected

Configuration Steps :
- Log into Prisma Cloud Console.
- Go to Manage > Defenders > Deploy > Defenders.
- Select Single defender
- In the Defender Type drop-down list, choose App-Embedded
- Set the Deploy App-Embedded Defender to Fargate Task
- Embed the Fargate Defender into your task definition.
6a. Copy and paste your task definition into the left-hand box.
6b. Click Generate Protected Task
6c. Copy the updated task definition from the right-hand box.
Creating a task definition in AWS
- Create a new task definition in AWS with the output from the previous section.
- If you already have an existing task definition, create a new revision.
- Log into the AWS Management Console.
- Go to Services > ECS
- Click Task Definitions then click Create new Task Definition
3.1 Select Fargate then click Next step
3.2 Scroll to the bottom of the page, and click Configure via JSON
3.3 Delete the prepopulated JSON, then paste the JSON generated for task from the previous section.
3.4 Click Save
4. Validate task content.
3.2 Scroll to the bottom of the page, and click Configure via JSON
3.3 Delete the prepopulated JSON, then paste the JSON generated for task from the previous section.
3.4 Click Save
4.1 Task name should be as described in the JSON.
4.2 Select the Task Role
4.3 The task should include the TwistlockDefender container.
4.4 Click Create
4.5 Click View task definition
4.2 Select the Task Role
4.3 The task should include the TwistlockDefender container.
4.4 Click Create
4.5 Click View task definition
Testing the Task
- Log into the AWS Management Console.
- Go to Services > ECS
- Click Clusters then select one of your Fargate cluster.
- Click the Services tab, then click Create
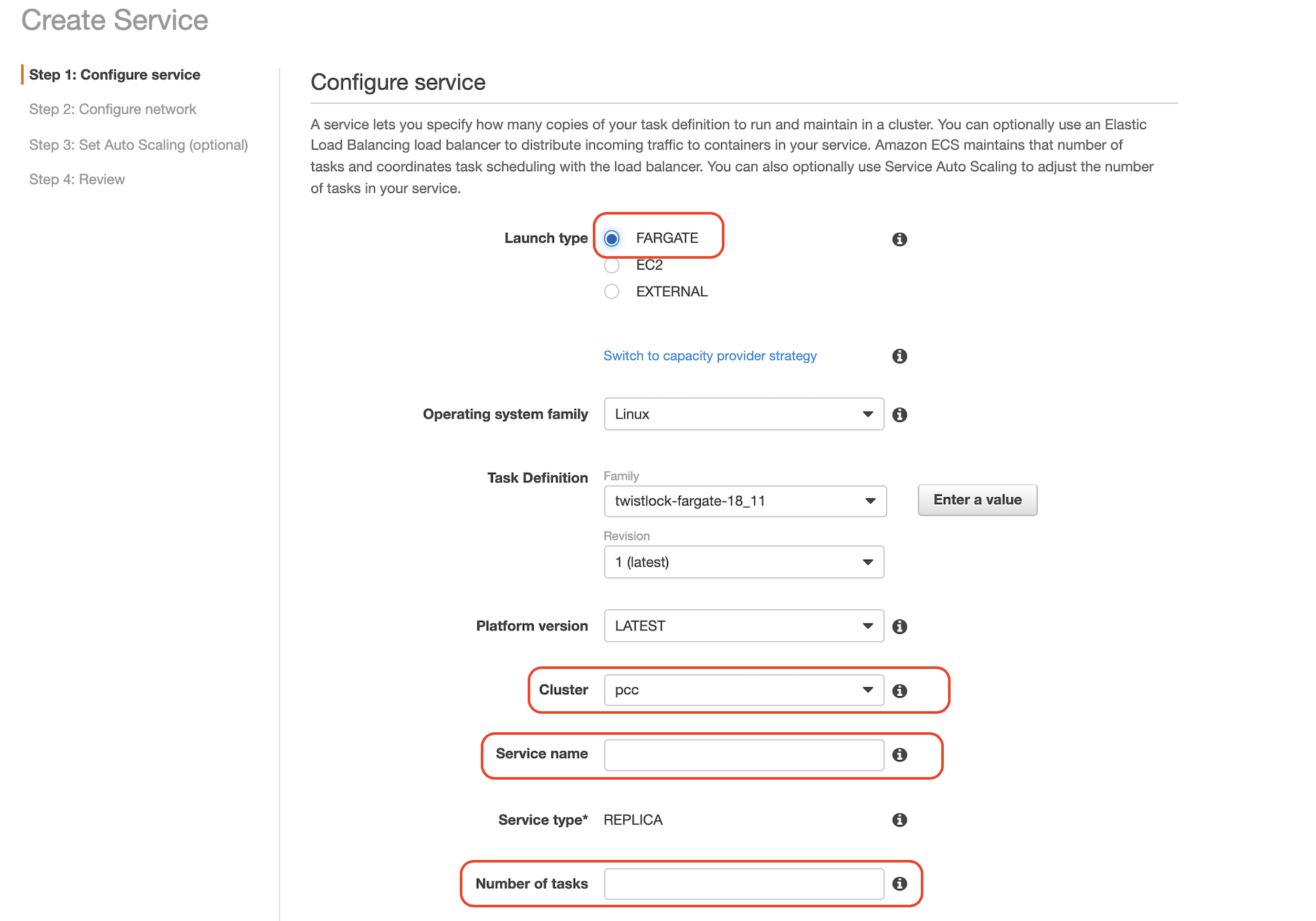
4.1 For Launch type select Fargate
4.2 For Task Definition select your pre-defined task.
4.3 Enter a Service name
4.4 For Number of tasks enter 1
4.2 For Task Definition select your pre-defined task.
4.3 Enter a Service name
4.4 For Number of tasks enter 1
4.5 Click Next step
4.6 Select a Cluster VPC and Subnets then click Next step
4.7 For Service Auto Scaling, select then click Next step
- Do not adjust the service’s desired count
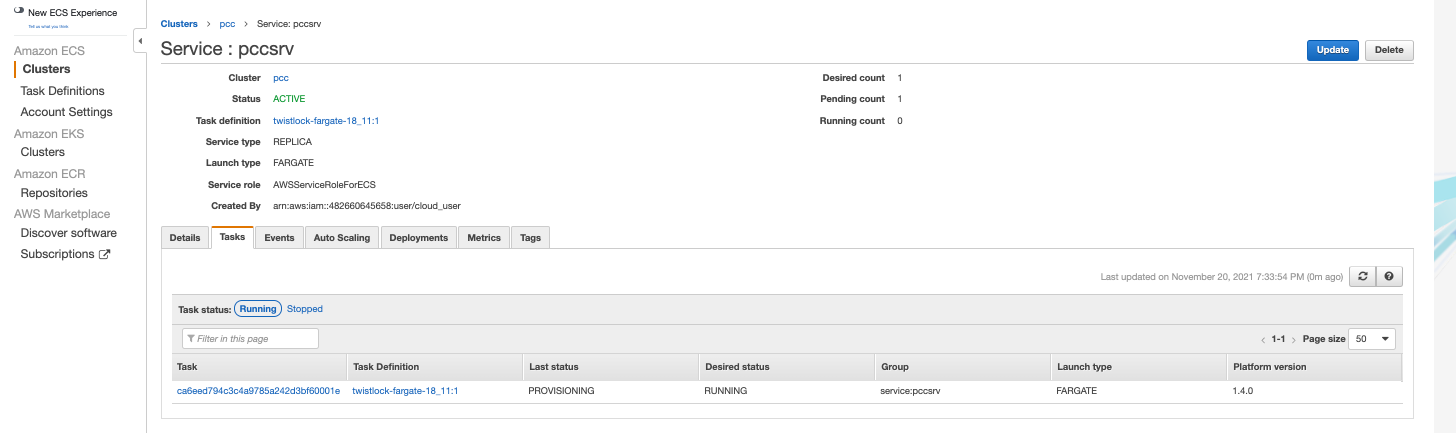
5. Review your settings, then click Create Service
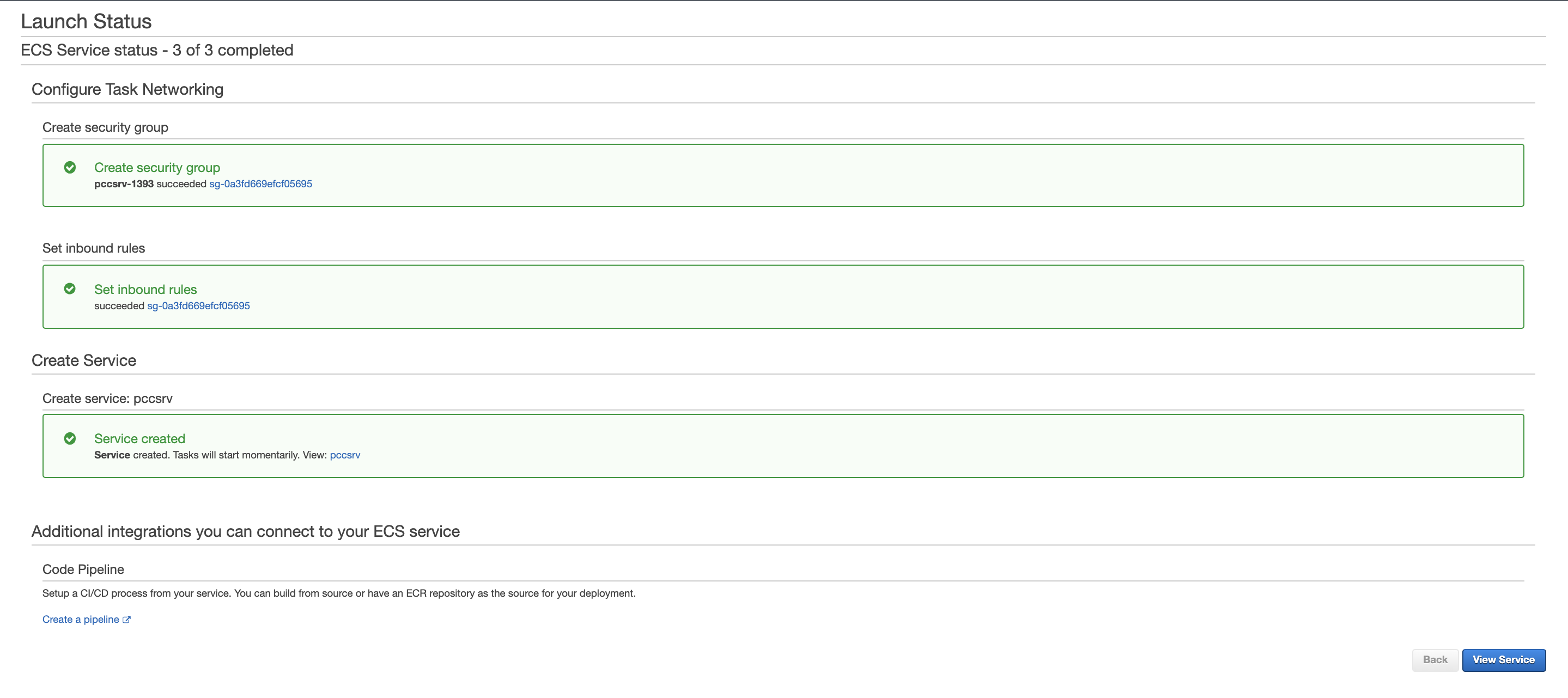
5.1 Validate the results.
5.2 Click View Service
5.2 Click View Service
- When Last status is Running, your Fargate task is running.
- The containers are running.
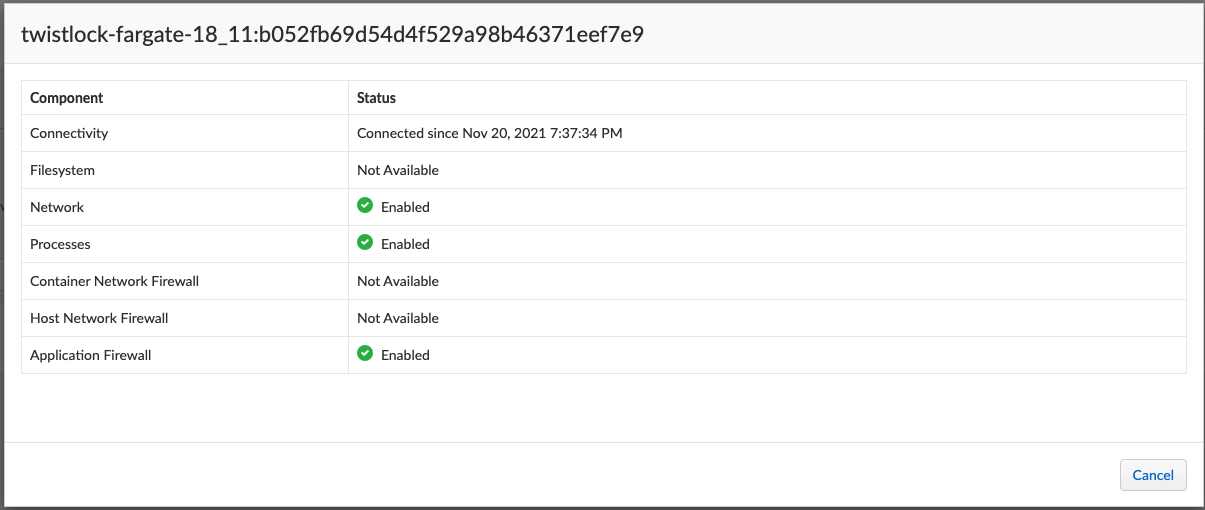
6. View the defender in the Prisma Cloud Console: Go to Manage > Defenders > Manage Defenders and search the fargate task by adding the filters Fargate and Status: Connected
Additional Information
- Prisma Cloud cleanly separates the code developers produce from the Fargate containers we protect.
- Developers don’t need to change their code to accommodate Prisma Cloud.
- Developers also don’t need to load any special libraries, add any files, or change any manifests.
- When a container is ready to be deployed to test or production, run the task definition through a transform tool to automatically embed the Fargate Defender before loading the new task definition into AWS.
- This method for embedding the Fargate Defender was designed to seamlessly integrate into the CI/CD pipeline.
- Developers can call the Prisma Cloud API to embed the Fargate Defender into your task definition.
Prerequisites:
- The task where you’re embedding the App-Embedded Defender can reach Console’s port 8084 over the network.
- A valid task task definition.
- Already created an ECS cluster.
- Cluster VPC and subnets.
- Task role.
NOTE:
- The task definition must include matching entrypoint and cmd parameters from Dokerfile(s) of the image(s) in the task.
- Because Prisma Cloud does not see the actual images as part of embedding flow, it depends on having these parameters present to reliably insert the App-Embedded Defender into the task startup flow.
- If Dokerfile does not include an entrypoint parameter, a default one such as /bin/sh must be used in the task definition.
- However, because the cmd parameter is optional, if Dokerfile does not include a cmd parameter, one is not required in the task definition.