How to block login attempts from specific countries or regions in Prisma Access
11252
Created On 06/10/23 02:38 AM - Last Modified 04/02/25 19:06 PM
Objective
- To block certain countries or regions attempting to login to Prisma access when configured Geo Location Rule rule is not working.
- The reason normal Geo location based rule does not work for initial login attempts for mobile user connections is due to the fact that there are pre-defined rules to allow that traffic subject to user fulfilling the authentication criteria configured by the administrator.
- The normal Geo location based rule will still work for users after the login is done (if allowed) for access to resources.
Environment
- Prisma Access for Users 3.1 or above.
- Prisma Access for Networks 3.1 or above.
- Geo Location Rules
Procedure
- Create a rule with only these pre-defined names and tags. An example is shown in the additional section.
- Block these countries using the following combination of Rule names, tags, and actions:
Rule names:
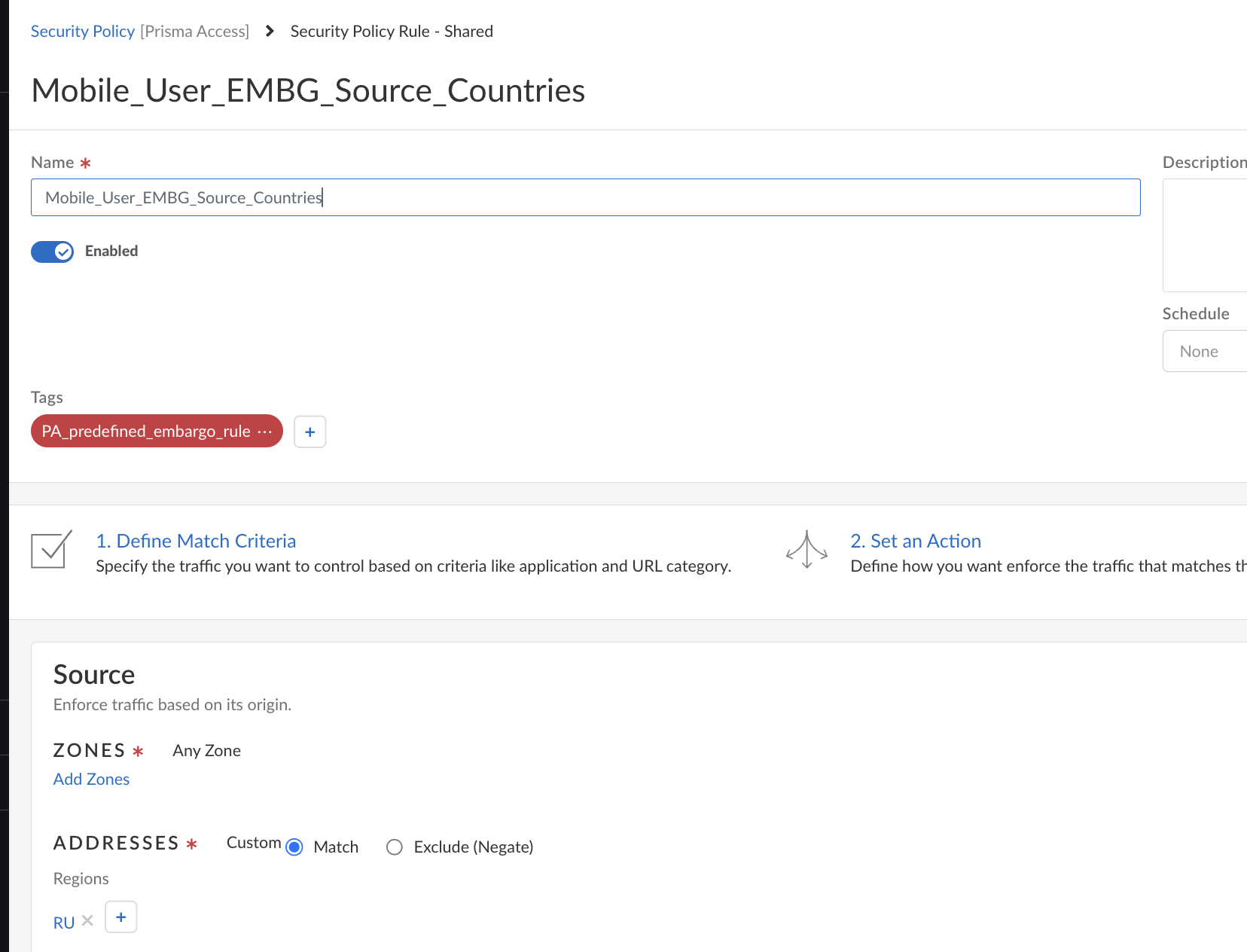
- Mobile Users—GlobalProtect deployments: "Mobile_User_EMBG_Source_Countries"
- Mobile Users—Explicit Proxy deployments: "Explicit_Proxy_EMBG_Source_Countries"
- Remote Network deployments: "Remote_Network_EMBG_Source_Countries"
Tag: "PA_predefined_embargo_rule
Action: "Drop"
- Commit the configuration.
The above information is documented at Features in Prisma Access 3.1 documentation.
Additional Information
- The rule name should be exactly as defined in the document.
- The Tag is also mandatory and the rule will not work as intended if the Tag PA_predefined_embargo_rule is not added to the rule.
- The rule doesn't have to be moved to the Top (Although it is recommended for sanity) as the Tag will cause the rule to be placed on top of rule stack in Prisma Access SPN.
- Rule examples
PANORAMA
STRATA CLOUD MANAGER