How to use authentication sequence for GlobalProtect to work with local accounts and LDAP accounts
44062
Created On 10/16/20 20:42 PM - Last Modified 07/11/24 18:45 PM
Objective
This article is designed to help customers to configure GlobalProtect to work with local accounts and LDAP accounts with an authentication sequence
Environment
- Palo Alto Networks Firewall
- PAN-OS 8.1 and above
- GlobalProtect Configured.
- LDAP and local user database authentication profiles
Procedure
- Configure the Authentication Sequence and add the Authentication Profiles by navigating to GUI:Device > Authentication Sequence > Select "Add"
Note: Palo Alto Networks firewall does not support SAML Authentication on the Authentication Sequence
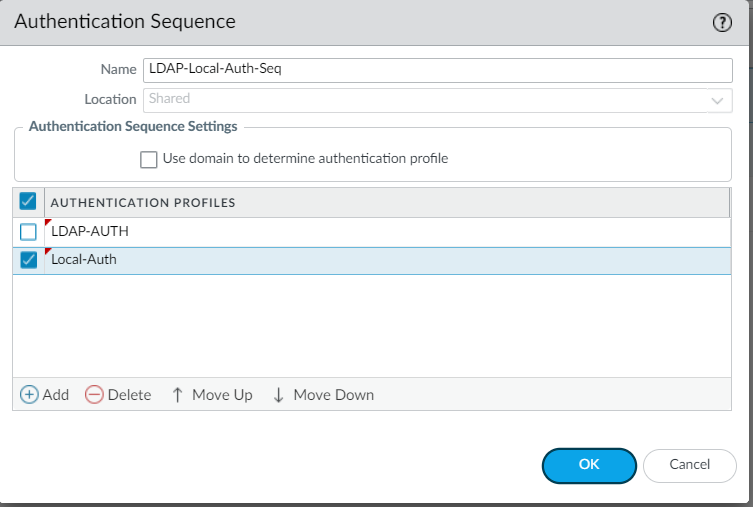
- Under GUI: Network > GlobalProtect > Portals > Select Portal > Authentication > Client Authentication tab, modify an existing or add a Client Authentication and select the Authentication Sequence created on step-1 under Authentication Profile and select OK
- Repeat the same for GlobalProtect Gateway Configuration (Client Authentication tab)
- Commit the changes on the Firewall.
- Try connecting the GlobalProtect App using the Authentication Sequence created on step-1 under Authentication Profile.
Additional Information
- An authentication sequence is a set of authentication profiles that the firewall tries to use for authenticating users when they log in.
- The firewall tries the profiles sequentially from the top of the list to the bottom-applying the authentication for each-until one profile successfully authenticates the user.
- The firewall only denies access if all profiles in the sequence fail to authenticate.
- For Example:
- If user “ldapuser” is present in the LDAP Server user group then it will get authenticated against the LDAP auth profile.
- If user “localuser” is part of Local DB then it will first try to authenticate against LDAP auth profile (user doesn’t exists) and then it will fall back to the Local authentication profile and gets authenticated.
- If User “ldapuser” exists in both LDAP user group and Local DB then it will authenticate against the LDAP authentication profile. It will only fallback to Local DB authentication profile if LDAP server is not responding or down.
- Authentication logs while using LDAP credentials.
debug: authd_sysd_profile_domain_callback(pan_auth_sysd.c:1018): get domain for vsys1/LDAP-Local-Auth-Seq <<<<<<<<<<<<<Auth sequence debug: pan_auth_cache_get_authprof_info(pan_auth_cache_authprof_n_authseqprof.c:176): prof "LDAP-Auth", vsys "vsys1" (method: LDAP (active directory)) has sso hash table id: 0 (0 means no or invalid keytab) <<<<<<<<< LDAP-Authentication on top of the list debug: pan_auth_cache_get_authprof_info(pan_auth_cache_authprof_n_authseqprof.c:176): prof "Local-Auth", vsys "vsys1" (method: local) has sso hash table id: 0 (0 means no or invalid keytab) <<<<<<<<<<<< Local Authentication second in the list debug: _authenticate_initial(pan_auth_state_engine.c:2387): Trying to authenticate (init auth): <profile: "LDAP-Local-Auth-Seq", vsys: "vsys1", policy: "", username "ldapuser"> ; timeout setting: 115 secs ; authd id: 6880508432479158348 debug: _get_auth_prof_detail(pan_auth_util.c:1089): non-admin user thru Global Protect "ldapuser" ; auth profile "LDAP-Local-Auth-Seq" ; vsys "vsys1" debug: _get_authseq_profile(pan_auth_util.c:876): Auth profile/vsys (LDAP-Local-Auth-Seq/vsys1) is auth sequence debug: pan_auth_cache_user_is_allowed(pan_auth_cache_allowlist_n_grp.c:628): This is a single vsys platform, group check for allow list is performed on "vsys1" debug: _authenticate_by_localdb_or_remote_server(pan_auth_state_engine.c:1833): Authenticating user "ldapuser" with <profile: "LDAP-Auth" , vsys: "vsys1">, which is Auth Profile 1 of 2 in <sequence "LDAP-Local-Auth-Seq", vsys "vsys1"> debug: pan_auth_response_process(pan_auth_state_engine.c:4315): auth status: auth success debug: pan_auth_response_process(pan_auth_state_engine.c:4336): Authentication success: <profile: "LDAP-Auth", vsys: "vsys1", username "ldapuser"> authenticated for user 'ldapuser'. auth profile 'LDAP-Local-Auth-Seq', vsys 'vsys1', server profile 'DC1.DOMAIN.COM', server address '172.16.3.10', From: 172.16.0.11. <<<<<<<<<< user “ldapuser” is authenticated against the LDAP-Auth profile
- Authentication logs while using Local DB credentials.
debug: authd_sysd_profile_domain_callback(pan_auth_sysd.c:1018): get domain for vsys1/LDAP-Local-Auth-Seq
debug: pan_auth_cache_get_authprof_info(pan_auth_cache_authprof_n_authseqprof.c:176): prof "LDAP-Auth", vsys
"vsys1" (method: LDAP (active directory)) has sso hash table id: 0 (0 means no or invalid keytab)
debug: pan_auth_cache_get_authprof_info(pan_auth_cache_authprof_n_authseqprof.c:176): prof "Local-Auth", vsys
"vsys1" (method: local) has sso hash table id: 0 (0 means no or invalid keytab)
debug: _authenticate_initial(pan_auth_state_engine.c:2387): Trying to authenticate (init auth): <profile:
"LDAP-Local-Auth-Seq", vsys: "vsys1", policy: "", username "localuser"> ; timeout setting: 115 secs ;
authd id: 6880508432479158353
debug: _get_auth_prof_detail(pan_auth_util.c:1089): non-admin user thru Global Protect "localuser" ; auth
profile "LDAP-Local-Auth-Seq" ; vsys "vsys1"
debug: _get_authseq_profile(pan_auth_util.c:876): Auth profile/vsys (LDAP-Local-Auth-Seq/vsys1) is auth sequence
debug: _authenticate_by_localdb_or_remote_server(pan_auth_state_engine.c:1833): Authenticating user "localuser"
with <profile: "LDAP-Auth", vsys: "vsys1">, which is Auth Profile 1 of 2 in <sequence "LDAP-Local-Auth-Seq",
vsys "vsys1">
Error: _parse_ldap_bind_result(pan_authd_shared_ldap.c:282): bind failed (extracted from parsed bind result)
(code: 49) (string: Invalid credentials) (additional info: 80090308: LdapErr: DSID-0C09041C, comment:
AcceptSecurityContext error, data 57, v4563)
Error: _parse_ldap_bind_result(pan_authd_shared_ldap.c:286): wrong password was provided
Error: pan_authd_ldap_authenticate(pan_authd_shared_ldap.c:1243): User "localuser" is REJECTED (msgid = 25,
LDAPp=0x555557cea870)
debug: pan_authd_ldap_authenticate(pan_authd_shared_ldap.c:1326): binding back to binddn: CN=PaloAlto Service Account
,CN=Managed Service Accounts,DC=DOMAIN,DC=COM (Try 1)
debug: pan_authd_ldap_bind(pan_authd_shared_ldap.c:634): binding with binddn CN=PaloAlto Service Account,CN=Managed
Service Accounts,DC=DOMAIN,DC=COM
debug: pan_auth_response_process(pan_auth_state_engine.c:4315): auth status: auth failed
<<<<<<<<<<<<<<<< Failed for LDAP-Auth since user trying to authenticate is not part of LDAP user group
debug: pan_auth_response_process(pan_auth_state_engine.c:4465): Auth sequence, start to try next auth profile:
<profile: "Local-Auth", vsys: "vsys1"> for user "localuser"
debug: pan_auth_request_process(pan_auth_state_engine.c:3375): Receive request: msg type PAN_AUTH_REQ_REMOTE_INIT_AUTH
, conv id 76, body length 2448
debug: _authenticate_initial(pan_auth_state_engine.c:2387): Trying to authenticate (init auth): <profile:
"LDAP-Local-Auth-Seq", vsys: "vsys1", policy: "", username "localuser"> ; timeout setting: 115 secs ;
authd id: 6880508432479158353
debug: _authenticate_initial(pan_auth_state_engine.c:2491): Using auth sequence, copying original username localuser
into request
debug: _get_auth_prof_detail(pan_auth_util.c:1089): non-admin user thru Global Protect "localuser" ; auth sequence
profile "LDAP-Local-Auth-Seq" ; vsys "vsys1"
debug: _authenticate_by_localdb_or_remote_server(pan_auth_state_engine.c:1833): Authenticating user "localuser" with
<profile: "Local-Auth", vsys: "vsys1">, which is Auth Profile 2 of 2 in <sequence "LDAP-Local-Auth-Seq",
vsys "vsys1">
debug: pan_auth_response_process(pan_auth_state_engine.c:4315): auth status: auth success
debug: pan_auth_response_process(pan_auth_state_engine.c:4336): Authentication success: <profile: "Local-Auth",
vsys: "vsys1", username "localuser">
authenticated for user 'localuser'. auth profile 'LDAP-Local-Auth-Seq', vsys 'vsys1', From: 172.16.0.11.
<<<<<<<<< user name "localuser" got authenticated with Local-Auth which is second in the list on Auth Sequence.
- You can read more about the authentication profiles and sequence at the links below: