How to configure GlobalProtect with Certificate Only Authentication in PAN-OS 9.0?
25809
Created On 04/02/20 06:16 AM - Last Modified 07/28/25 10:05 AM
Objective
This document discusses the steps necessary to configure GlobalProtect for certificate only client authentication for PAN-OS 9.0
Environment
- Palo Alto Networks Firewall.
- PAN-OS 9.0.
Procedure
1. Confirm that all required certificates have been generated and/or imported onto the firewall (ie: root, client, machine certificates.)
2. Create the Certificate Profile and add the appropriate CA certificates under Device > Certificate Management > Certificate Profile.
- Add the necessary root CA(s) that will be used to authenticate clients to the profile.
3. Configure the Global Protect Gateway to use the Certificate Profile by navigating to Network > GlobalProtect > Gateways.
- Select the appropriate gateway from the list, choose the "Authentication" tab, and select the correct profile from the dropdown list. Leave the client Authentication Profile blank.
4. Configure the Global Protect Portal to use the Certificate Profile by navigating to Network > GlobalProtect > Portals.
- Select the appropriate portal from the list, choose the "Authentication" tab, and select the correct profile from the dropdown list. Leave the client Authentication Profile blank.
Note: Having the firewall generate a client certificate assumes that the Certificate infrastructure is set up on the network to support that client certificate. Alternatively, a client cert may not be necessary and may also not be advisable in a multi-user environment. It may be better to use a certificate profile with the CA which will be used to sign each user's certificate, so that each user can and will receive a unique certificate from the CA.
5. Disable SSO within the Global Protect Portal by navigating to Network > GlobalProtect > Portals.
- Select the appropriate portal from the list, choose the "Agent" tab, and select the client config. Then choose the "App" tab and modify the "Use Single Sign On" settings.
- Commit all changes
6. Export and install the root and client certificates into the local store of the client's endpoint.
Note: When exporting the client machine certificate from the Palo Alto Networks device, it needs to be in PKCS12 format.
7. Install the client certificate into the user's local store.
8. When connecting to the GlobalProtect Gateway, the user will not be required to provide a username and password.
- You can view information regarding the clients connection via either the GlobalProtect Agent settings or the specific Gateway's "Remote Users" information section in the firewall's GUI.
Agent View:
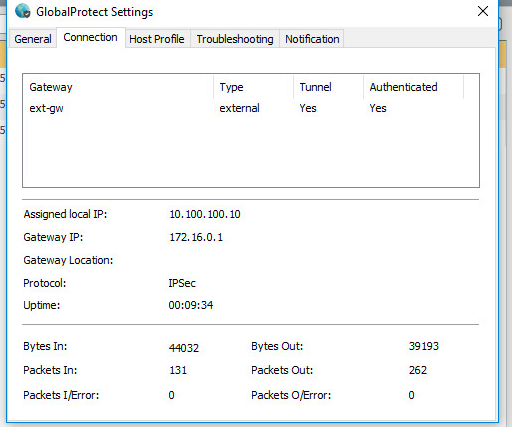
GUI View:
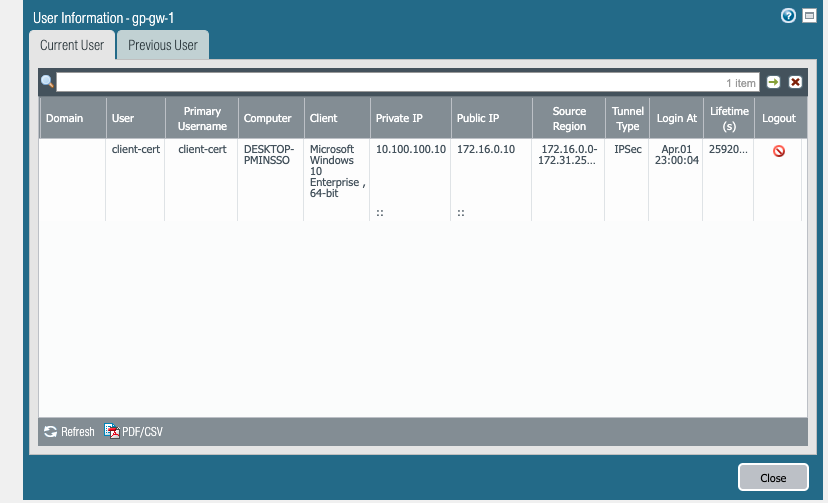
GUI View:
Additional Information
Please note that this document only refers to the components within GlobalProtect that involves client certificate authentication.