Sanctioned Access For Office365 Enterprise Using HTTP Header Insertion
86636
Created On 01/21/20 15:16 PM - Last Modified 01/21/20 16:08 PM
Objective
Previously, there was a provision to allow only sanctioned instances of Office365 enterprise accounts and blocking unsanctioned enterprise and consumer accounts. This was done by creating a custom application based on the domain used to log in to Office365 enterprise accounts. However, this is no longer possible due to some changes done on the Microsoft end, which means that any traffic corresponding to custom application corresponding to sanctioned domains will be identified as the pre-defined application office-365-base.
Environment
HTTP Header Insertion Feature in Palo Alto Networks devices.
Procedure
The workaround is to utilize the HTTP Header Insertion Feature.
- The first step is to create a custom URL category for the Microsoft domains.
Next, we must ensure this traffic is decrypted.
- Create a Decryption Policy Rule, and, in the Service/URL Category tab, add the URL Category that was created in the previous step.
- In the Options tab, make sure the action is set to Decrypt and that the Type is set to SSL Forward Proxy.
Now, we have to edit or create a URL Filtering Profile.
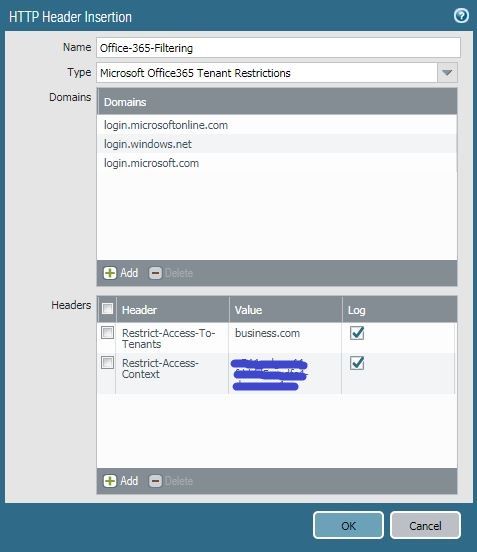
- Select HTTP Header Insertion in the URL Filtering Profile Dialog.
- Add an entry.
You provide Restrict-Access-To-Tenants with a list of tenants you want to allow your users to access.
- You can use any domain that is registered with a tenant to identify the tenant in this list.
You provide Restrict-Access-Context with the directory ID that is setting the tenant restriction.
- You can find your directory ID in the Azure portal. Sign in as an administrator, select Azure Active Directory, then select Properties.
docs.microsoft.com/en-us/azure/active-directory/active-directory-tenant-restrictions
The idea is that you modify the HTTP Header with a tenant target for Office365. The rule will allow the traffic out, but since you are defining what Office365 instance you are trying to auth against, if they tried to login with an Office365 account that isn't part of that tenant of your domain, Microsoft will block it.
Also, remember to set the action of the custom URL category that was created to allow in the URL Filtering Profile. When you attempt to access the unsanctioned domain, you should see the response page from Microsoft as below.