Issue
Unwanted ARP entries are appearing in the ARP table of a Palo Alto Networks device. The ARP table is filled with entries of addresses from the Internet and is nearing the ARP table limitation.
Details
When the Palo Alto Networks firewall is deployed in L3 mode, there will be ARP entries for the hosts and devices that are part of the same network/subnet configured on the firewall interfaces. If there are ARP entries for addresses that aren't part of any subnet of any Palo Alto Networks firewall interface, it implies that the firewall is performing proxy-ARP on the interface.
If there is a static route configured without a Next Hop IP, all the hosts responding from the destination network of the static route back to the firewall will have an ARP entry on the firewall. Here's an example configuration:
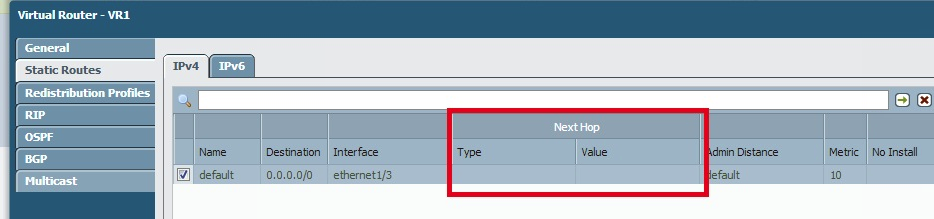
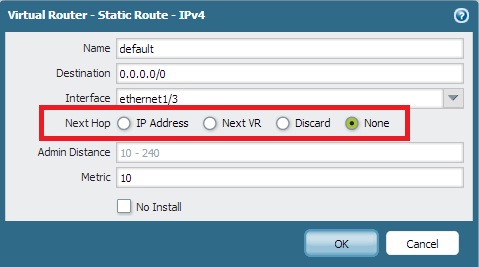
The examples show a default static route configured with an outgoing interface selected and the Next Hop value set to None. In this case, the Palo Alto Networks firewall is going to ARP for all hosts in the 0.0.0.0/0 network and creating ARP entries for hosts responding back.
Resolution
If ARPing is not intentionally implemented on an interface for a subnet not owned by the firewall, make sure to specify a Next Hop value, as shown:
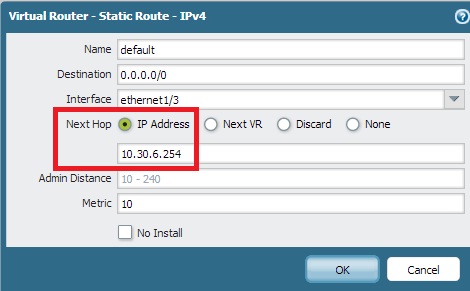
The example screenshot shows the Next Hop value is specified in the form of an IP address. This configuration will prevent the PA firewall from ARPing for all hosts matching the route 0.0.0.0/0.
owner: mvenkatesan