Background
- Traceroute is a powerful network diagnostic tool used in Linux to map the path packets take from the client to a destination. It helps pinpoint network delays, identify unreachable hops, and troubleshoot routing issues.
- Tracepath is a Unix/Linux-based utility similar to traceroute. However, the differences between the two are:
-
- Tracepath does not require users to have root privilege.
- Tracepath uses (and only uses) UDP with random high port. traceroute (on Unix/Linux) by default also uses UDP with range destination port 33434-33534, but has an option to switch to ICMP (Windows traceroute always use ICMP).
Note: This is applicable for PAN-OS 5.0 or later.
Detail
- If a security rule only allows application "traceroute" and service "application-default" and there is no other subsequent rule to permit tracepath traffic then its UDP packet will get dropped.
| Security Policy | Traffic Log |
|---|
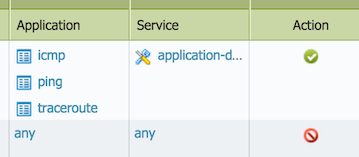 | 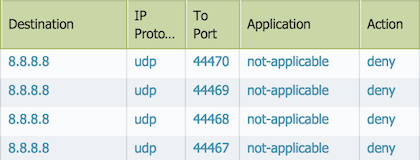 |
Explanation: This is because tracepath uses UDP with random high port. If a service is set to "application-default", tracepath could get denied because in App-ID signature the standard port range for traceroute only includes icmp/any and udp/33434-33534.
#### **Key Consideration: UDP Blocking by Network Devices**
- Some next-hop network devices, including firewalls or routers, may **block UDP traceroute packets**, preventing the tool from functioning correctly.
- When traceroute encounters a blocked UDP port, users might see `* * *` timeouts or incomplete paths in the output.
- Since Windows uses ICMP by default (`tracert` command), Linux users may need to **manually switch to ICMP** if encountering blocks.
Solution
- There are two possible solutions:
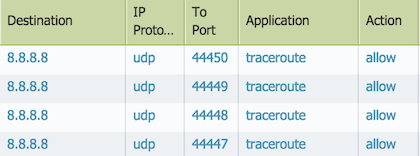
1) Configure the security rule to allow application "traceroute" and service "any". You will also need to allow application "icmp" and "ping" as well because these two are application dependency for traceroute.
| Security Policy | Traffic Log |
|---|
 |  |
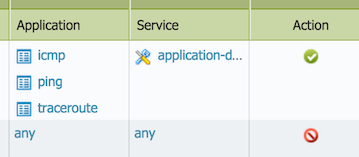
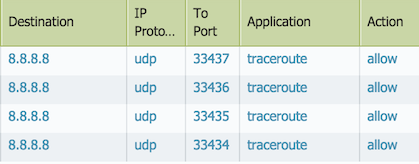
2) Instruct users to run tracepath with a specific "starting" destination port 33434. Note in the traffic log, the destination port increments from 33434 for each hop. Again, allowing application icmp & ping is still needed due to the traceroute application dependency.
| Security Policy | Traffic Log |
|---|
 |  |
See also
Can a Policy be Configured to Allow Traceroute?