Details on how to configure Azure MFA RADIUS with GlobalProtect. Please note the key configuration required on Palo Alto Networks GlobalProtect is forcing the use of PAP as Azure supports only PAP and MSCHAPv2.
Azure MFA Settings with On-Premise MFA Server RADIUS (recommended by Microsoft)
Note: Assumes that the MFA Server is installed already and syncing users with AD already.
- Enable Radius Authentication.
- On the client's tab, change the Authentication port(s) and Accounting port(s) if the Azure Multi-Factor Authentication RADIUS service should bind to non-standard ports to listen for RADIUS requests from the clients that will be configured. This is the same as configured on Palo Alto Networks.
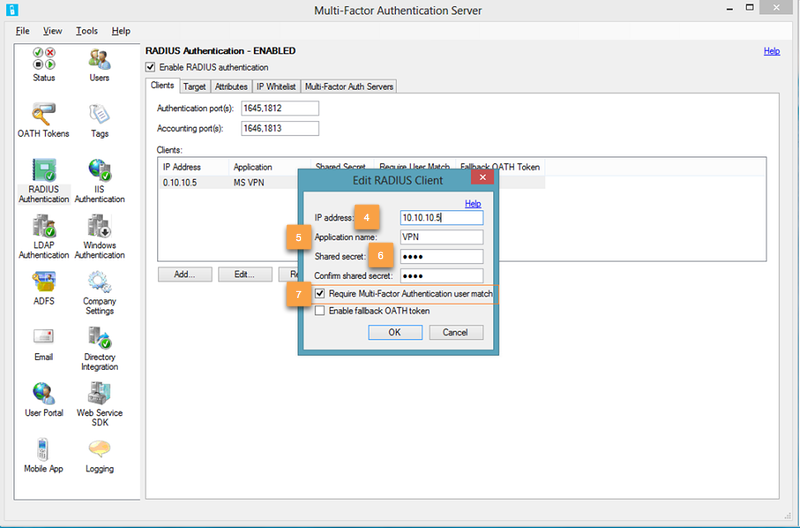
- Under the client tab, click Add.
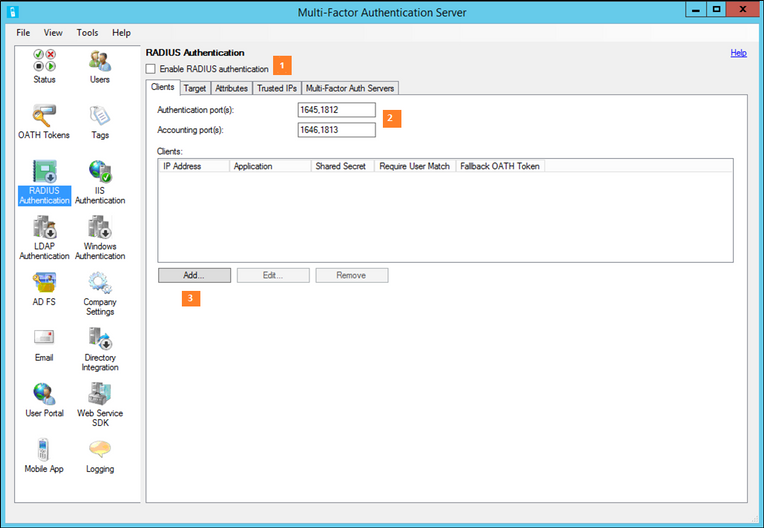
- Enter the Management IP of the Palo Alto Networks firewall as IP address which will authenticate to the Azure Multi-Factor Authentication Server.
- Give it a name. (Optional)
- Enter a shared secret.
- Select 'Require Multi-Factor Authentication user match. '
Check the Enable fallback OATH token box if users will use the Azure Multi-Factor Authentication mobile app authentication and you want to use OATH passcodes as a fallback authentication to the out- of-band phone call, SMS, or push notification.
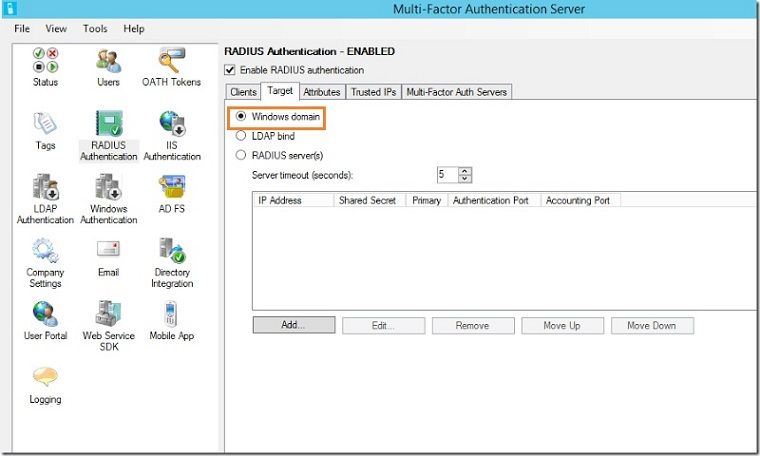
8. Under the target tab, use ‘Windows domain’ if the machine is joined to the domain, if not, use the LDAP bind.
GlobalProtect Configuration
Note: Azure MFA Sever supports only PAP and MSCHAPv2. You will need to force the GlobalProtect to use PAP only. It is set to auto by default. If a different authentication is selected, then the error message in the authd.log will only indicate invalid username/password.
There's no option to manually disable RADIUS CHAP mode on the Palo Alto Networks firewall running PAN-OS 7.0.3 or earlier, either from the command line or webGUI.
In PAN-OS 7.0.4 or above, you can use '> set authentication radius-auth-type <auto|chap|pap>' to manually set the RADIUS authentication type.
- Log into the Palo Alto Networks firewall.
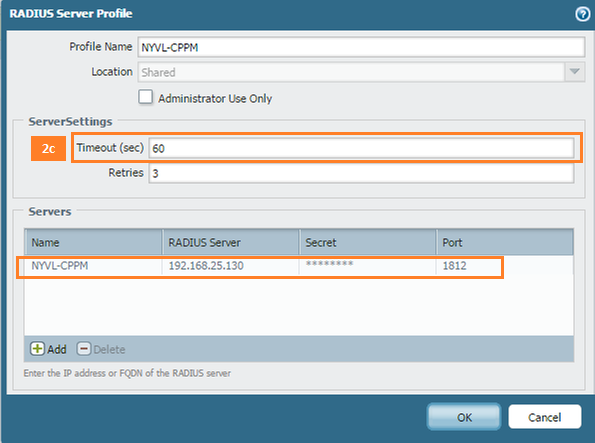
- Under Device> Server Profiles > Radius create the following profile:
a. Name Profile - name of the MFA server
b. Location - Shared
c. Timeout - 30 to 60 seconds to allow time to validate user credentials, perform multi-factor authentication, receive response, then respond to the RADIUS access request (see screenshot below).
d. Retries - 3.
e. Click Add and specify the RADIUS server as the FQDN or IP address of the Windows Azure Multi-Factor Authentication server and same shared secret that was configured above.
f. Port default - 1812.
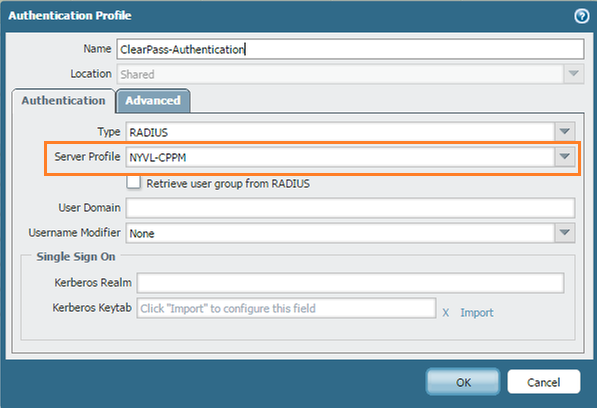
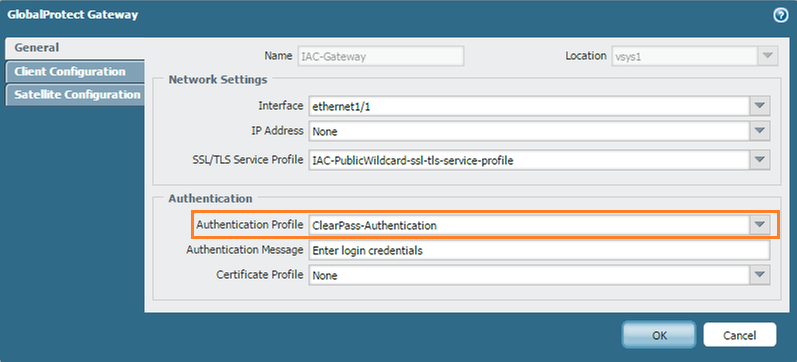
- Under Network > Gateways (assuming the gateway is already configured)
- Under General > Authentication Profile, select the profile you created in step 2.