For the above-mentioned applications that can be correctly identified at a pre-determined point in the live session, the firewall will implicitly allow the enabler app. For this reason the firewall uses the “uses-apps” and “implicit-uses-apps” part of the content updates metadata for the given application.
For applications that have a list of apps in the “implicit-uses-apps”, those applications will be implicitly allowed, and no separate security rule is needed to allow them.
For applications that do not have a list of apps in the “implicit-uses-apps” and have a list of apps in the “uses-apps” part of the application definition, there is a need to explicitly allow them (the enabler applications) so that the dependent application is allowed. This can be added in a separate security rule, or in the same rule that is allowing the dependent app.
The application definition can be checked to see if there is a need to explicitly allow the enabler applications. Run with the following command from configuration mode:
> configure
Entering configuration mode
[edit]
# show predefined application <name-of-app>
Steps
As examples for this, we will use the "facebook-base" and the "office-on-demand" applications.
Facebook-base
Application definition:
# show predefined application facebook-base
facebook-base {
ottawa-name facebook;
category collaboration;
subcategory social-networking;
technology browser-based;
alg no;
appident yes;
virus-ident yes;
vulnerability-ident yes;
evasive-behavior no;
consume-big-bandwidth no;
used-by-malware yes;
able-to-transfer-file yes;
has-known-vulnerability yes;
tunnel-other-application yes;
prone-to-misuse no;
pervasive-use yes;
per-direction-regex no;
deny-action drop-reset;
run-decoder no;
cachable no;
references {
Wikipedia {
link http://en.wikipedia.org/wiki/Facebook;
}
}
default {
port tcp/80,443;
}
use-applications [ ssl web-browsing];
tunnel-applications [ facebook-apps facebook-chat facebook-code facebook-file-sharing facebook-mail facebook-posting facebook-rooms facebook-social-plugin facebook-video facebook-voice instagram-base];
implicit-use-applications [ ssl web-browsing];
applicable-decoders http;
risk 4;
application-container facebook;
}
[edit]
To allow facebook-base, only the security policy that has the application facebook-base is needed. There is no need to allow the ssl and web-browsing because they are implicitly allowed based on the following part in the definition of the application:
"use-applications [ ssl web-browsing];"
"implicit-use-applications [ ssl web-browsing];"
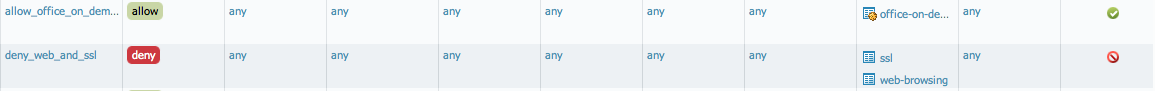
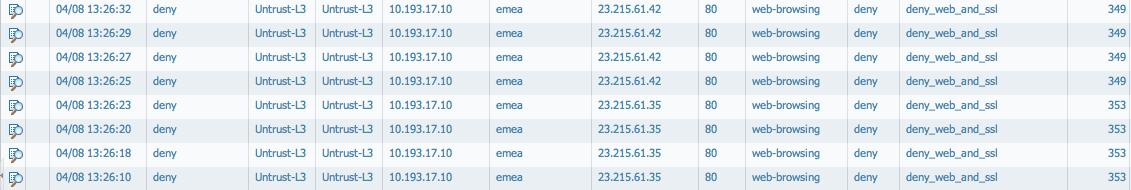
For facebook-base there is only the allow-facebook security rule that allows only facebook-base. There are no explicit rules to allow web-browsing and ssl. On the contrary, for the purpose of the test, a deny rule for web-browsing and SSL is used:

The logs show that Facebook is allowed:

Office-on-demand
Application definition:
# show predefined application office-on-demand
office-on-demand {
category business-systems;
subcategory office-programs;
technology browser-based;
alg no;
appident yes;
virus-ident yes;
spyware-ident yes;
file-type-ident yes;
vulnerability-ident yes;
evasive-behavior no;
consume-big-bandwidth yes;
used-by-malware no;
able-to-transfer-file yes;
has-known-vulnerability yes;
tunnel-other-application no;
prone-to-misuse no;
pervasive-use yes;
per-direction-regex no;
deny-action drop-reset;
run-decoder no;
cachable no;
file-forward yes;
is-saas yes;
references {
"Office on Demand" {
link http://office.microsoft.com/en-us/support/use-office-on-any-pc-with-office-on-demand-HA102840202.aspx;
}
}
default {
port tcp/80;
}
use-applications [ ms-office365-base sharepoint-online ssl web-browsing];
applicable-decoders http;
risk 3;
application-container ms-office365;
}
[edit]
For office-on-demand, the
"use-applications [ ms-office365-base sharepoint-online ssl web-browsing];"
can be seen, and there is no
implicit-use-applications
List with the same applications. This will mean that all of the applications in the list need to be explicitly allowed, so that all the features of office-on-demand will work correctly.
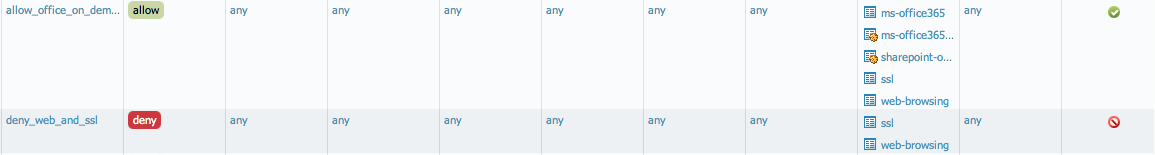
The traffic can be seen as allowed for web-browsing and for office-on-demand. The application started as web-browsing and was correctly identified by the Palo Alto Networks DFA, and thus changed to "office-on-demand".
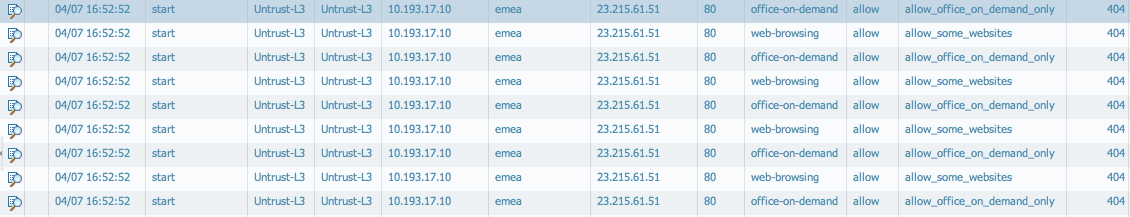
If web is denied in a security policy, the connections can be seen as not established, because the rule to allow the office-on-demand application will never be hit.