Overview
This document describes how to configure firewall to capture ARP packets on an interface on a Palo Alto Networks firewall.
Steps
From the WebGUI
- Go to Monitor > Packet Capture.
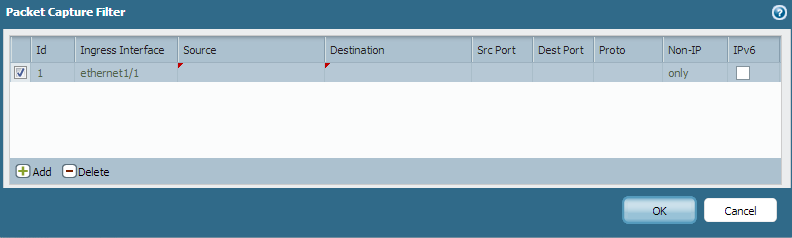
- Click Manage Filters and create a filter.
- Select an interface for Ingress Interface
- Select 'only' for the Non-IP column
- Enable Filtering (set to ON).
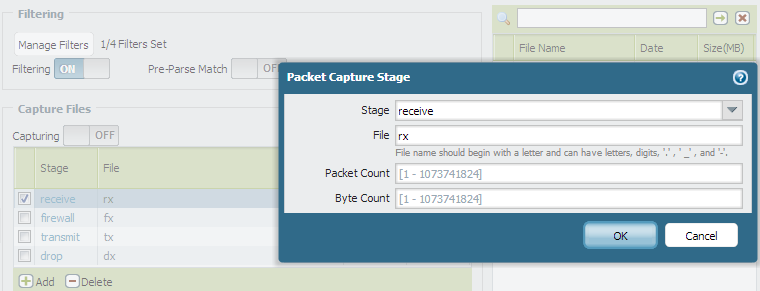
- Configure the stages for packet captures. Enter a file name for each configured stage.
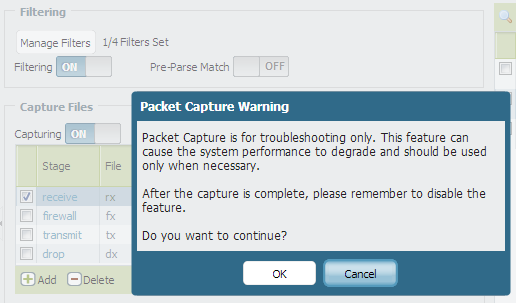
- Enable Capturing. Click OK when the Packet Capture Warning appears.
- Refresh the page and the packet capture files will appear. Download the packet capture file by clicking on the respective link.
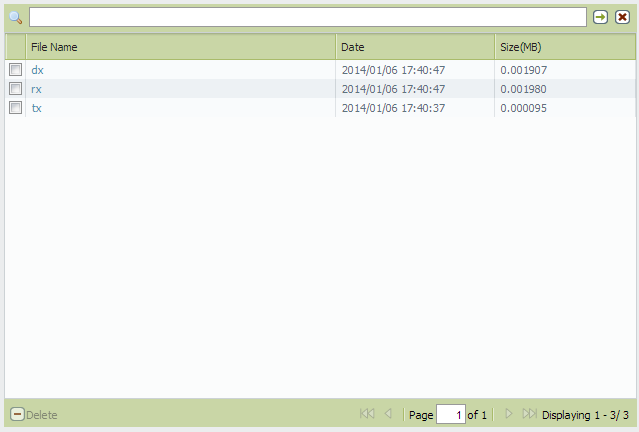
From the CLI
Run the following CLI commands to capture ARP packets.
-
-
- > debug dataplane packet-diag set filter match non-ip only ingress-interface ethernet1/1
- > debug dataplane packet-diag set filter on
- > debug dataplane packet-diag set capture stage drop file dx
- > debug dataplane packet-diag set capture stage transmit file tx
- > debug dataplane packet-diag set capture stage receive file rx
- > debug dataplane packet-diag set capture stage firewall file fx
- > debug dataplane packet-diag set capture on
The rx file contains ARP request initiated by an external host which is broadcast. The ARP reply for the ARP request sent by interface ethernet1/1 is Unicast.
The tx file contains ARP reply sent from the firewall interface.
Note: The process described above will not capture ARP requests initiated from firewall. Check on the next hop device to get information on ARP requests initiated from the Palo Alto Networks firewall.
Example
The Palo Alto Networks firewall (10.66.24.87) does not have ARP entry for 10.66.24.86
> ping source 10.66.24.87 host 10.66.24.86
PING 10.66.24.86 (10.66.24.86) from 10.66.24.87 : 56(84) bytes of data.
64 bytes from 10.66.24.86: icmp_seq=2 ttl=64 time=0.936 ms
64 bytes from 10.66.24.86: icmp_seq=3 ttl=64 time=0.875 ms
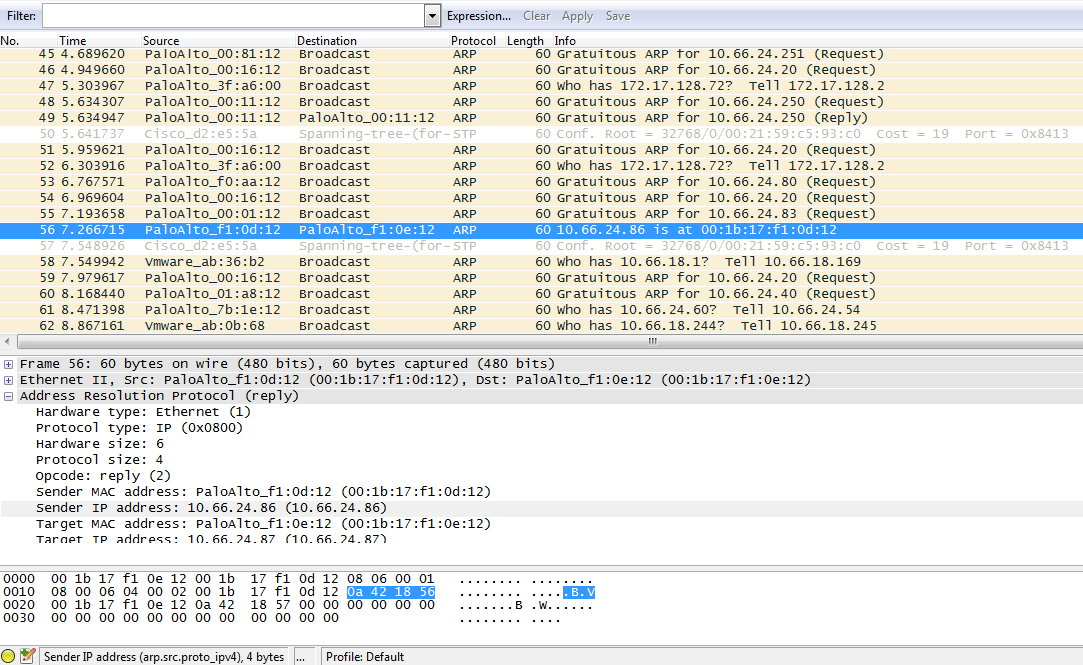
The rx file with the ARP reply for an ARP request initiated by interface:
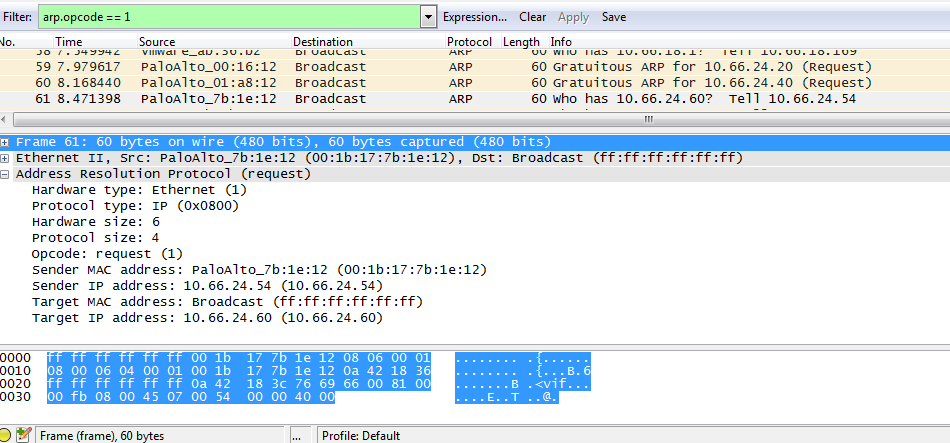
The rx file with ARP request received from other hosts:
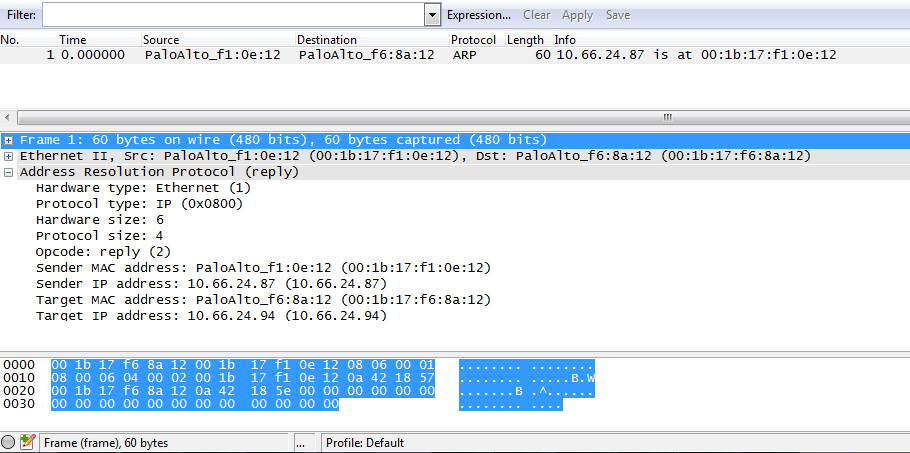
The tx file contains the ARP reply sent from the firewall interface, which is the response to the ARP request for the MAC address of the firewall interface.
Note: Along with these packets, the pcap files contain non-IP traffic like CDP, spanning-tree, and so on.
owner: hshah