Starting with PAN-OS 7.0, it is now possible to configure user and group-based policy using the information from the X-Forwarded-For header. If the value is an IP address, we fetch user information from the user-id, and if it is not an IP address, this value is the username for group mapping. If a corresponding user cannot be found for an IP address, it falls back to an 'unknown' or 'any' user rule, which is usual behavior with User-ID.
This is useful in deployments in which we have proxy between the firewall and the end-user.
Configuration from the Web GUI:
- Go To Device > Setup > Content ID > X-Forwarded-For headers.
- Click on settings, check ‘Use X-Forwarded-For Header in User-ID’ to use the value from XFF Header as IP address/Username.
- If needed, check ‘Strip X-Forwarded-For Header’ with the first option, If this is also enabled, the XFF Header will be stripped off after we use the XFF value for user identification.
- Commit the changes.
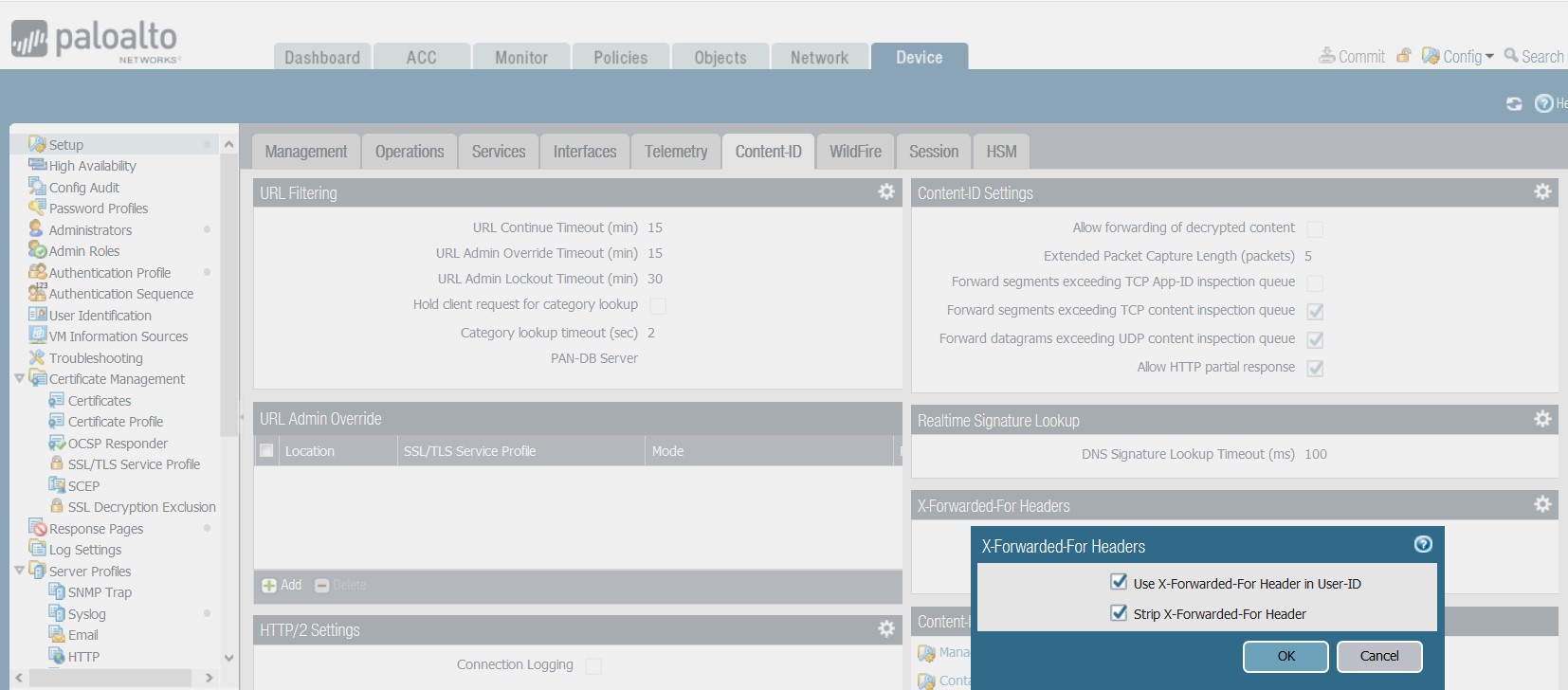
Configuration from the CLI:
This operational mode command is transient and doesn't survive a reboot. Parse x-forwarded-for is set to yes.
> set system setting ctd x-forwarded-for yes
Configuration mode command is persistent and survives reboot.
# set deviceconfig setting ctd x-forwarded-for yes
# commit
Default Setting:
The setting is disabled by default unless the setting was enabled on earlier versions using the same CLI command as above or using the GUI setting to parse X-forwarded-for header ( Device > Setup > Content ID->X-Forwarded-For Headers> )
Current Setting:
Current configuration can be verified using the CLI command show system setting ctd state
PA-FW> show system setting ctd state | match x-
Parse x-forwarded-for : no
Strip x-fwd-for : no
When this is enabled, it changes to yes.
PA-FW> show system setting ctd state | match x-
Parse x-forwarded-for : yes
Strip x-fwd-for : yes
Points to Note:
- If we have multiple IP address in the X-forwarded for header, first in the list is considered to be the actual source.
- The source IP address in the security policy and logs will still be IP address of the proxy server.
- The X-Forwarded-For Header is leveraged only for User-ID.
- We can enable strip X-Forwarded-For if you do not want the private address you use to leave the corporate network.
- This setting when configured applies to all vsys with User-ID enabled in multi-vsys environment.
- Both IPv4 and IPv6 are supported.
- This can be used as match condition only in Security Policy and QoS Policy as it is mentioned, and not for any other policies.
- We can now also see the user name in threat and traffic logs in 'Victim Name' and 'Source User' correspondingly even though IP address is Proxy Server IP.