Issue
When configuring a Policy Based Forwarding (PBF) rule to forward all the traffic sourced from one zone to internet through an ISP, the rule will take effect only for the workstation behind the Palo Alto Networks firewall and not for the traffic sourced from the firewall.
Cause
When a route is present in the routing table, along with a PBF rule, then only the PBF rule will be evaluated first in a top to down basis matching the specific entry. However, this applies only for the traffic sourced from a workstation behind the firewall. When a PBF rule is in place to forward all the traffic from a trusted zone to an un-trusted zone, the rule will come into effect only when the traffic is sourced from the workstation behind the Palo Alto Networks firewall. However, when trying to source the traffic from the firewall it will bypass the evaluation of the PBF table and instead starts to evaluate the routing table checking for a corresponding matching route to forward the traffic out of the egress interface.
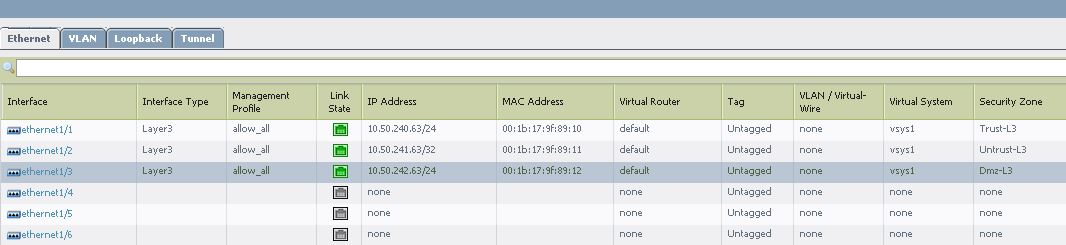
From the WebGUI go to Network > Interfaces > Ethernet, in the following scenario the interfaces are configured, as shown below:
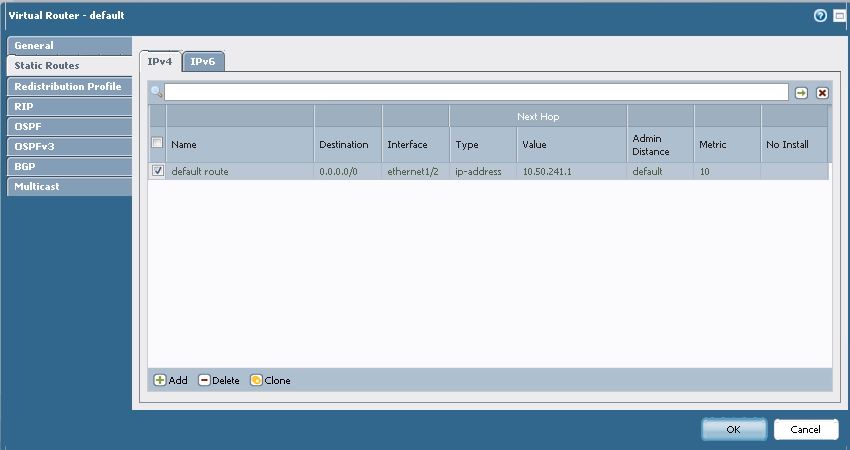
Under Network > Virtual Routers > Static Routes, there is a default route in place, as shown below:
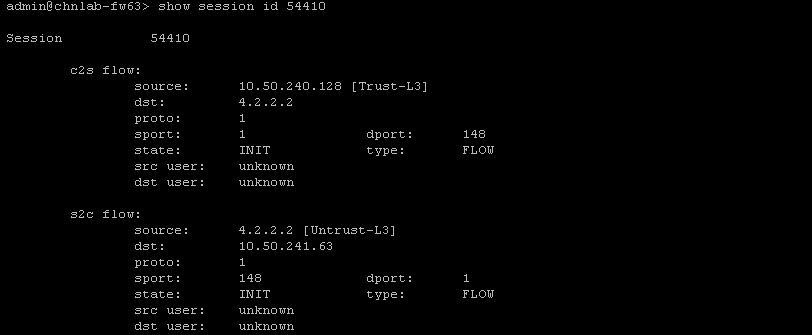
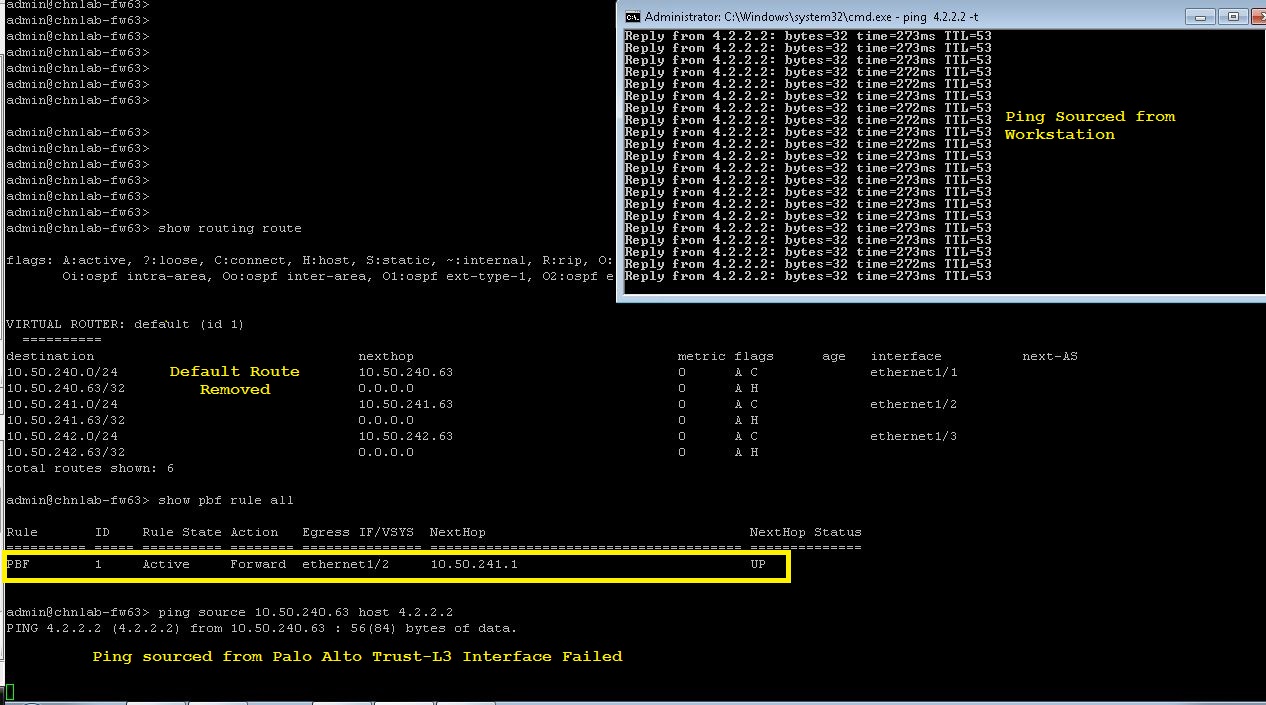
When sourcing the traffic from the workstation see the session information, as shown below:
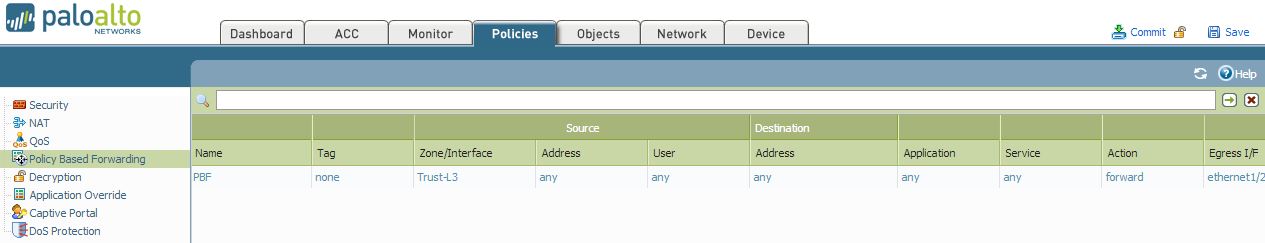
From the WebGUI, go to Device > Policy Based Forwarding and create the following PBF rule, which is the same as the default route:
When sourcing the traffic from the workstation, see the session information as shown below (in spite of the already existing default route only the PBF rule is getting evaluated first):
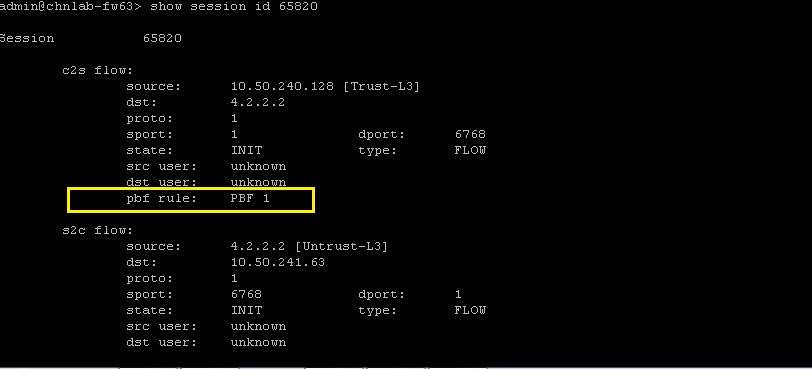
When trying to do a continuous ping from the workstation behind the firewall and firewall's trusted interface to the public ip 4.2.2.2, both the pings were successful. This is because the traffic sourced from the workstation used the PBF rule, and the traffic sourced from the firewall used the routing table:
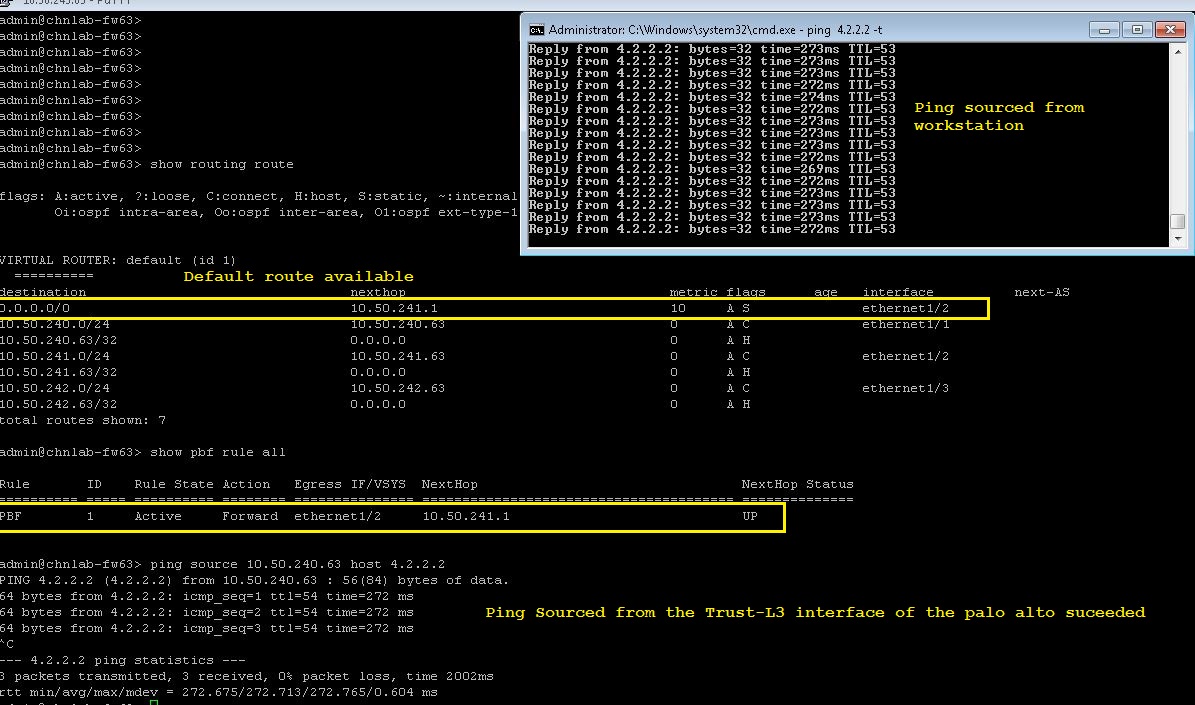
Only the default route was removed, the traffic sourced from the workstation was passing successfully using the PBF rule, however the traffic sourced from the firewall failed, shown below as the default route is removed:
The PBF will only work for the traffic sourced from a machine behind the firewall and not for the traffic sourced from the firewall.
The following are known limitations:
- PBF does not function for IPSec Tunnel traffic to the Palo Alto Networks firewall.
- PBF does not function for the Phase 1 tunnel to come up, it needs to use the routing table's default route to initiate the IKE.
- PBF does not function for GlobalProtect connection.
- When using applications for PBF rules, the application signature match for TCP traffic comes after the 3-way handshake. So the PBF rule may not match the initial 3-way handshake and thus traverse the firewall based only on route look-up.
owner: dantony