Updated May 2018 kiwi
Issue
Active Directory servers configured for Agentless User-ID frequently disconnects from the firewall. Connection status for those servers, under the server Monitoring section for User Mapping, keep flapping between connected and not connected. The User-ID logs have the following error message for each configured AD server :
Error: pan_user_id_win_sess_query(pan_user_id_win.c:1241): session query for <server name> failed: [wmi/wmic.c:216:main()] ERROR: Retrieve result data.
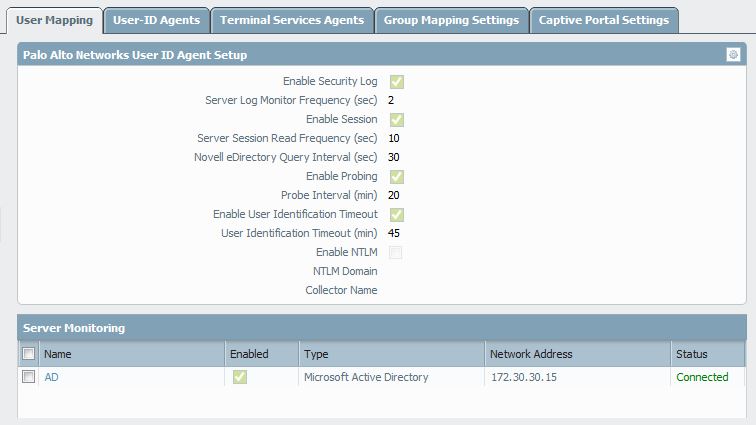
Shown in the screenshot below, see the "not connected" status in the Server Monitoring under Device > User Identification > User Mapping> Server Monitoring:
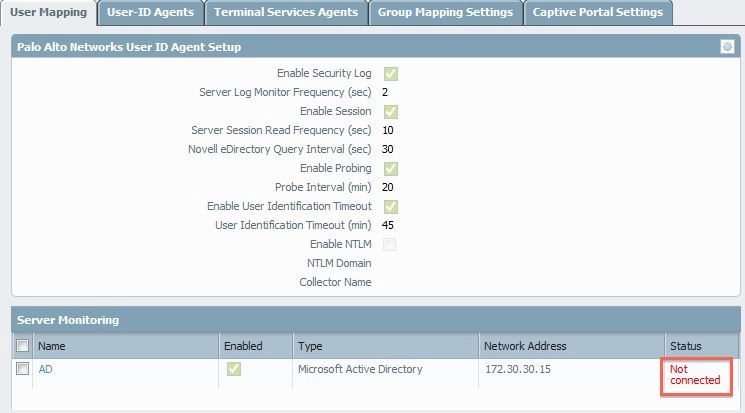
Cause
Agentless User-ID is configured to monitor user session information from the servers in the Server Monitoring list. Session query attempts from the firewall to those AD servers are failing due to permission issues. The domain account, used to access the session information, does not have privileges to read the user session information from the servers. The server operators group and Domain Admin groups will include the session query read permissions.
As shown in the example below, go to Device > User Identification > User Mapping > Palo Alto Networks User-ID Agent Setup and click on the setting to find the User Name, which is used to connect the Agentless User-ID to the AD server (172.30.30.15):
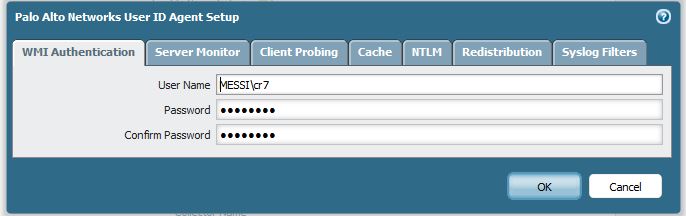
As shown in the example below, in the AD Server (172.30.30.15) see the permissions for the user cr7:
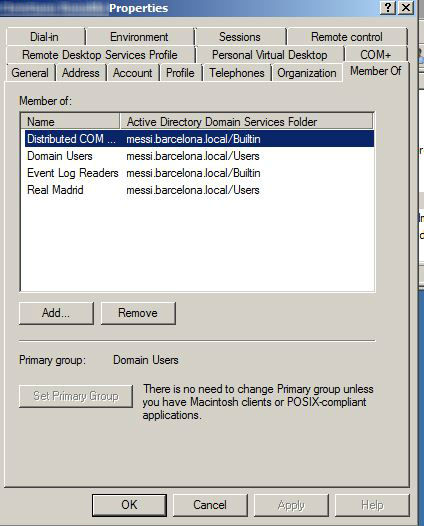
Resolution:
- Option 1: Grant server operators or domain admin privileges to the service account used under WMI Authentication. In the example below, is shows how to add the Server Operator permission to the user cr7:
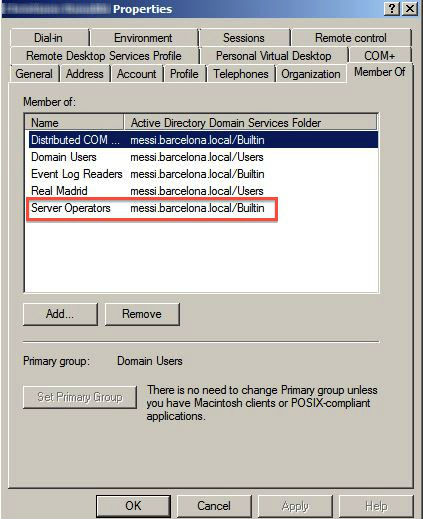
After adding the Server Operator permission to user cr7, from the example below see that the Agentless User-ID is now connected to the AD server:
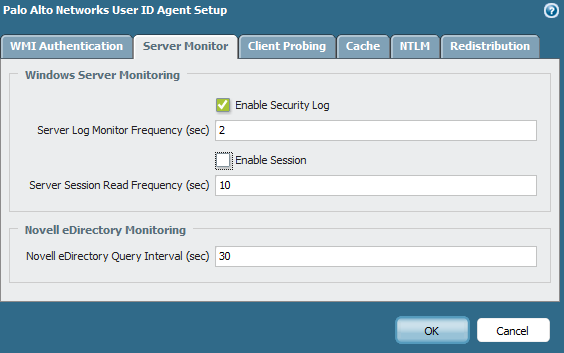
- Option 2: If it is not being used, disable the server session read option:
owner: knarra