WildFire is a cloud-based service that integrates with the Palo Alto Firewall and provides detection and prevention of malware.
PAN-OS 7.0 +
Starting with PAN-OS 7.0, WildFire is configured as a WildFire Analysis Profile and can then be applied to a security policy that matches the traffic that needs to be analysed.
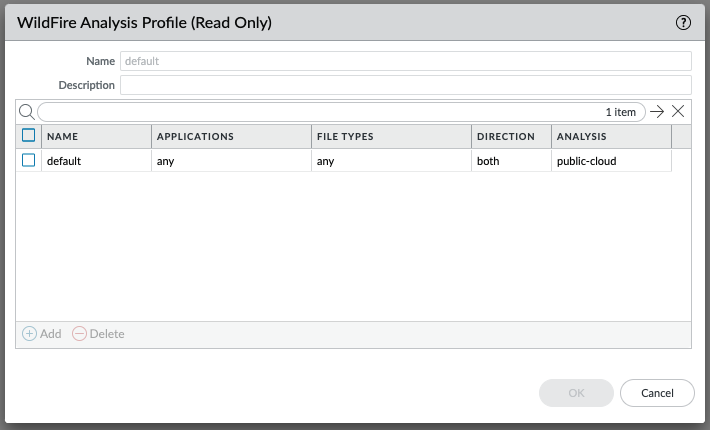
In a security policy:
Security Policy Rule with WildFire configured.
Please make sure if the security policy is more strict to verify if the application paloalto-wildfire-cloud will be allowed outbound from the management interface to the internet. The application may need to be added to the existing service policy containing paloalto-updates and such services, or an additional Service Route needs to be added to bind wildfire-cloud to the external interface

The WildFire Analysis can simply be set to send to the public-cloud, or if a WF-500 appliance is available, to the private-cloud
A file type determined in the WildFire configuration is matched by the WildFire cloud.
Palo Alto Networks firewalls compute the hash of the file and send only the computed hash to the WildFire cloud; in the cloud the hash is compared with the hash on the firewall. If the hash does not match it is uploaded and inspected and the file details can be viewed on the WildFire portal (https://wildfire.paloaltonetworks.com/). Please refer to the Administration Guide to find the URLs of the other regional clouds.
A file can also be manually uploaded to the WildFire portal for analysis.
WildFire Testing/Monitoring:
In order to ensure the management port is able to communicate with the WildFire we can use the "request wildfire registration" command in the CLI.
> request wildfire registration
WildFire registration for Public Cloud is triggered
WildFire registration for Private Cloud is triggered
The commands below can also be used to verify WildFire operation:
> show wildfire status
Connection info:
Signature verification: enable
Server selection: enable
File cache: enable
WildFire Public Cloud:
Server address: wildfire.paloaltonetworks.com
Status: Idle
Best server: eu-west-1.wildfire.paloaltonetworks.com
Device registered: yes
Through a proxy: no
Valid wildfire license: yes
Service route IP address:
File size limit info:
pe 2 MB
apk 10 MB
pdf 200 KB
ms-office 500 KB
jar 1 MB
flash 5 MB
... cut for brevity
> show wildfire statistics
Packet based counters:
Total msg rcvd: 1310
Total bytes rcvd: 1424965
Total msg read: 1310
Total bytes read: 1393525
... cut for brevity
> show wildfire cloud-info
Public Cloud channel info:
Cloud server type: wildfire cloud
Supported file types:
jar
flash
ms-office
pe
pdf
apk
email-link
The WildFire Submissions logs provide details post a WildFire action:
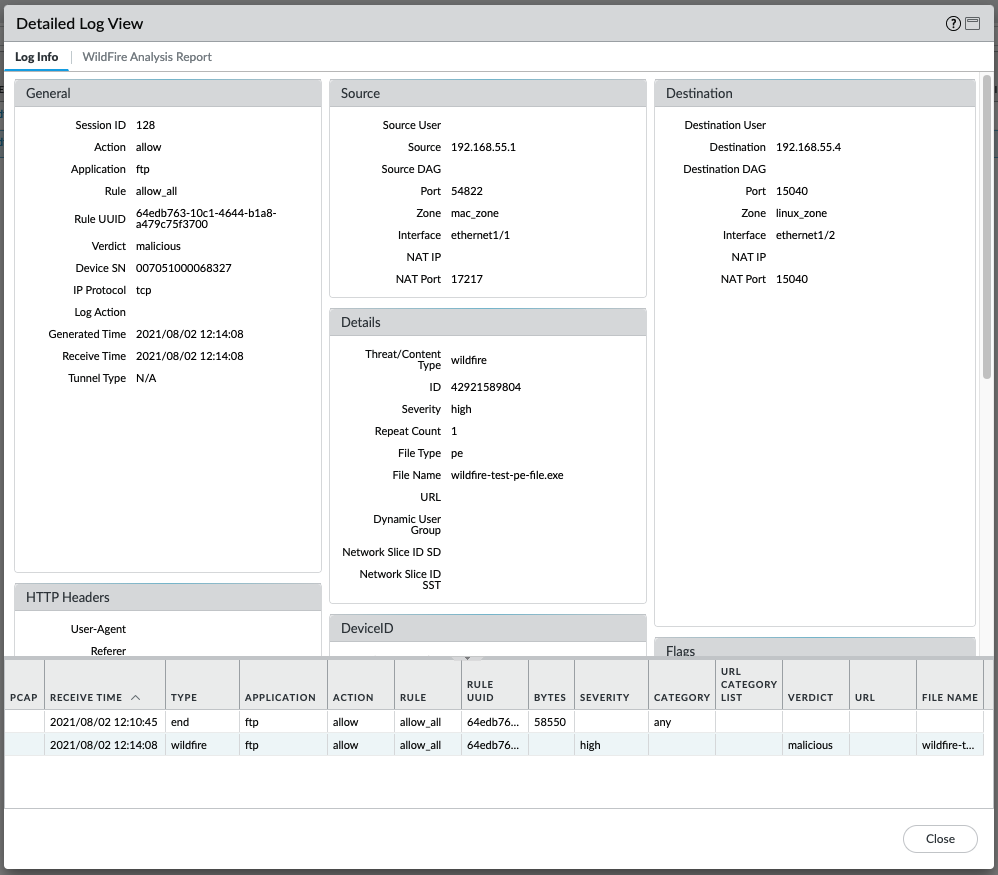
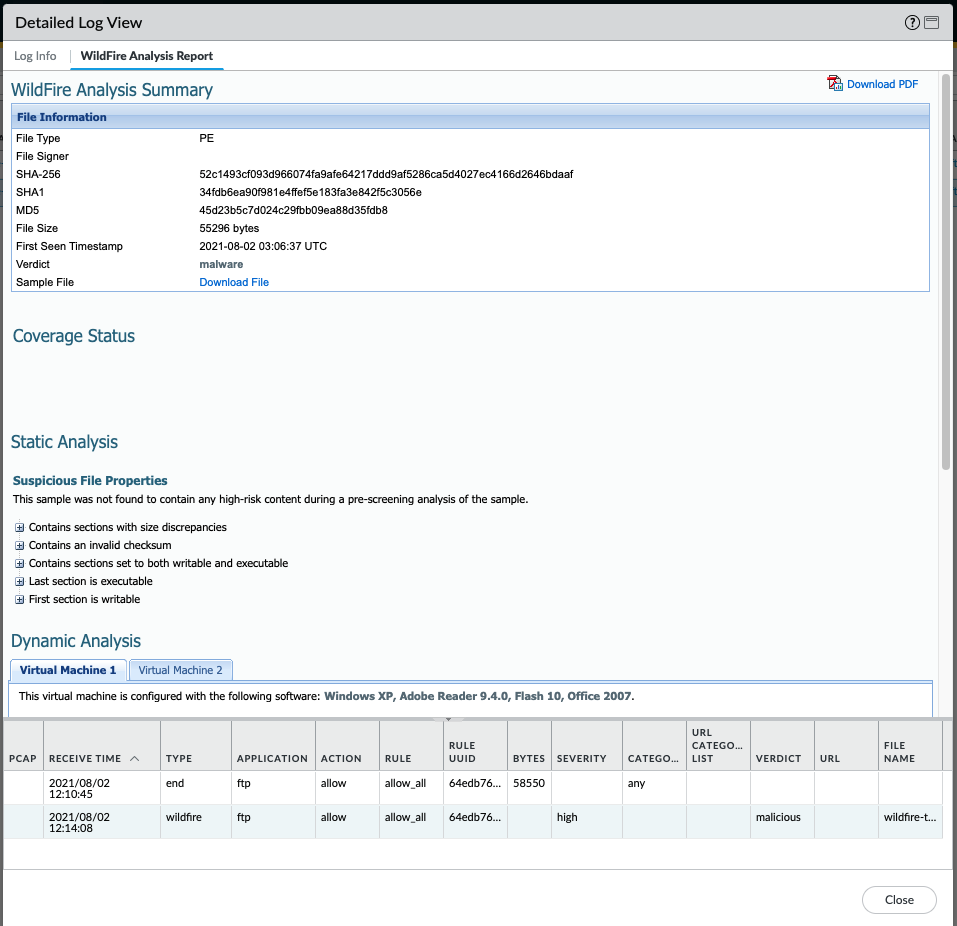
In case the file has recently been uploaded, the WildFire analysis may not have been completed yet in which case the report will not yet be available:
wildfire-upload.log shows details about the file submissions. The log can be monitored on the CLI as follows.
> grep mp-log wildfire-upload.log pattern wildfire-test-pe
2021-08-02 12:04:48 +0900: wildfire-test-pe-file.exe pe cancelled - by DP PUB 122 1 55296 0x4034 allow
2021-08-02 12:06:35 +0900: wildfire-test-pe-file.exe pe upload success PUB 125 2 55296 0x801c allow
2021-08-02 12:10:30 +0900: wildfire-test-pe-file.exe pe skipped - remote malware dup PUB 128 3 1428 0x1040 allow
> tail follow yes mp-log wildfire-upload.log
Data and Time filename file type action channel session_id transaction_id file_len flag traffic_action
2021-08-02 12:04:48 +0900: wildfire-test-pe-file.exe pe cancelled - by DP PUB 122 1 55296 0x4034 allow
2021-08-02 12:06:35 +0900: wildfire-test-pe-file.exe pe upload success PUB 125 2 55296 0x801c allow
2021-08-02 12:10:30 +0900: wildfire-test-pe-file.exe pe skipped - remote malware dup PUB 128 3 1428 0x1040 allow