Details
A packet received by Palo Alto Networks firewall will be processed differently depending on state of the matching session. This document explains the difference between packet processed in Slow Path, Fast Path and packet Offloaded.
This document will also refer to hardware components commonly used in most of the Palo Alto Networks appliances.
MAC Physical Chip
Handles physical layer connection (SFP, Ethernet ports) and perform ethernet framing.
Flow Engine
Performs flow lookup and may forward to Dataplane based on lookup results (no flow found or flow found but layer7 enabled).
Dataplane
Multi-core processor which handles L4-L7 security processing.
Slow Path
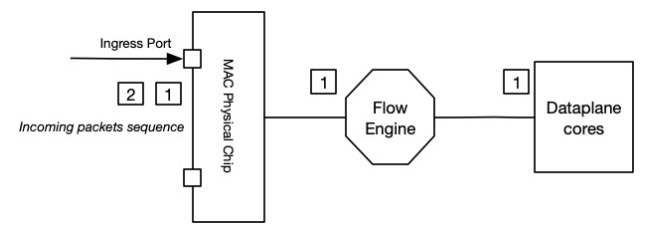
Note: The numbered squares in the diagrams for this document represent incoming packets (one square per packet) for the same session.
When the very first packet comes in, a session is not yet created.
This packet will be considered in slow path because a set of unique operations have to be done in the Dataplane:
- Forwarding lookup using FIB to get egress zone
- NAT Policy lookup + second forwarding lookup if DNAT is applied
- First security policy lookup (to match rules with service port configured with 'any' application)
- Packet is discarded or new session is created/installed in Dataplane.
Fast Path
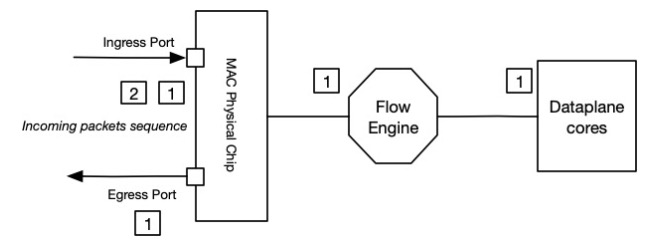
The following packets of the same session will be considered in the Fast Path.
Operations in the Slow Path do not need to be achieved anymore, except for forwarding lookup that we are doing for each packet before forwarding it to egress interface.
Forwarding lookup in Slow Path is done to get egress zone, needed for policies lookup.
Offload
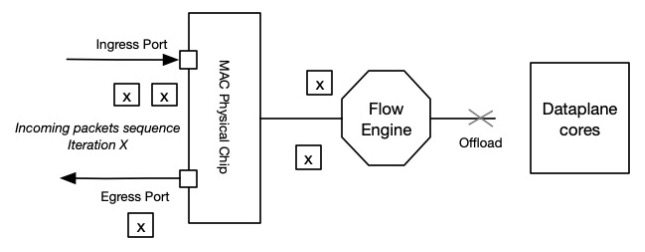
Once App-ID and Content Inspection are fully completed, the session and subsequent packets can be fully offloaded into the Flow Engine. Ingress packets will never reach the Dataplane anymore and the Flow Engine will fully manage packet forwarding. This operation will alleviate the load on the Dataplane's cores.
Note: It is important to understand that all packets will always be flowing through the Flow Engine, even if session is not offloaded. The decision algorithm for offloading a session is beyond this article's scope.
Conditions for a session for not being offloaded in hardware
An active session can be offloaded in the Flow Engine to alleviate the load on CPUs.
By default, all sessions are eligible for offload, but there are also some conditions that will prevent this.
A session where application is not recognized (APP-ID has not been completed) cannot be offloaded.
A session where content inspection is not yet finished cannot be offloaded.
This condition includes:
- Session that is being scanned for threat with a security profile applied
- Session running an application that can be changed into another, which potentially tunnels other applications
There is also a type of traffic that will only be processed by CPU and will never be offloaded.
- ARP (and all other non-IP traffic)
- IPSec
- Decrypted sessions
- VPN sessions
- non-TCP/UDP (with the exception of some protocols such as passthrough GRE/IPSEC, etc.)
- Firewall bound session
- Inter-vsys sessions
- PBF session without next hop
- NAT64
owner: nbilly