When configuring SSL decryption policy in order to define SSL traffic eligible for decryption, you have to make a choice between 2 different types/modes:
- SSL Forward-Proxy
- SSL Inbound Inspection
This article explains the difference between the two modes.
Forward-Proxy
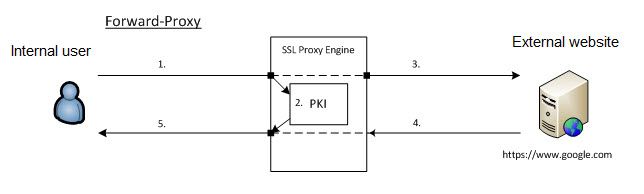 SSL Forward Proxy showing an Internal user going to an External SSL site.
SSL Forward Proxy showing an Internal user going to an External SSL site.
In Forward-Proxy mode, PAN-OS will intercept the SSL traffic which is matching the policy and will be acting as a proxy (MITM) generating a new certificate for the accessed URL. This new certificate will be presented during SSL Handshake to the client accessing website with SSL. This certificate will be signed with the self-signed CA certificate or another certificate specified as:
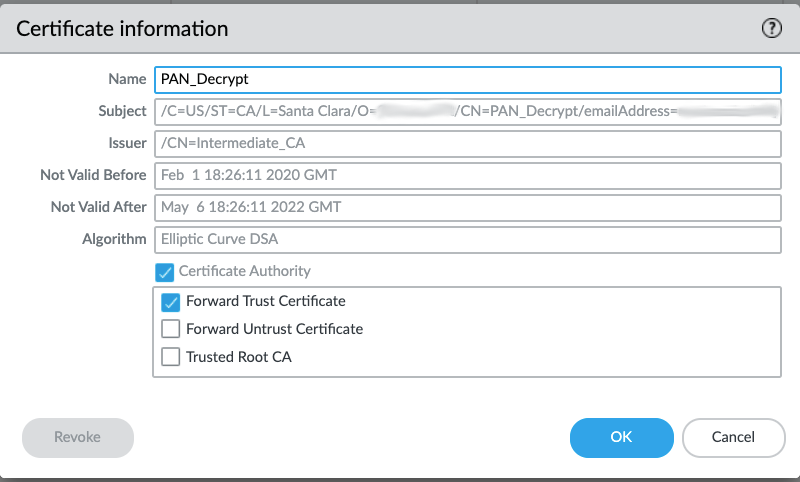
Note: If you want to use a certificate issued by third party, it needs to be a CA certificate and you will have to import public AND private key (Key Pair).
A separate certificate needs to be created to present to the Client when the Server Certificate signer is not trusted.
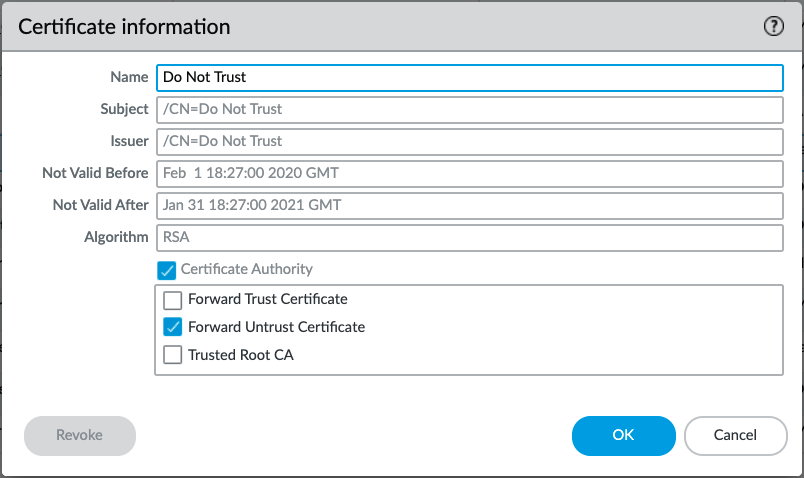
Note: If the same certificate was configured with both Forward Trust Certificate and Forward Untrust Certificate flags enabled, this would be a security risk, because clients behind the firewall would always be presented with a certificate they trust, even when the server is presented with an invalid certificate that should not be trusted.
- Internal user is trying to reach out www.google.com with https. Traffic is matching the decryption policy.
- This traffic is handled by our SSL proxy engine, and a certificate for www.google.com is generated by our internal PKI (signed by the CA certificate).
- PAN-OS is proxying the SSL traffic and setting up a new SSL connection with the Web Server.
- Web Server is starting handshake with PAN-OS device.
- PAN-OS device is completing its SSL handshake with client presenting generated certificate in Server Hello message.
Inbound Inspection
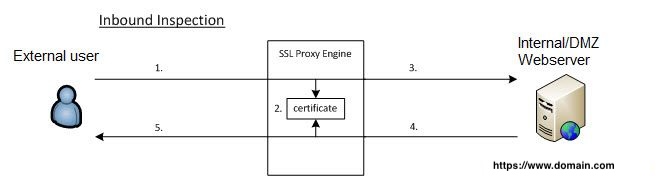
Inbound inspection showing when an external user comes into a webserver internally or in a DMZ.
In Inbound Inspection mode, PAN-OS will not act as a proxy with SSL traffic matching the policy. PAN-OS will try to decrypt this SSL traffic 'on-the-fly' by eavesdropping the SSL handshake and using associated Certificate (Key Pair) configured in decryption policy as below:
Note: Starting with PAN-OS 10.1, all inbound decrypted sessions are processed via proxy (firewall is MITM); There is no “transparent” processing for RSA key exchange. Refer to the SSL Inbound Inspection documentation.
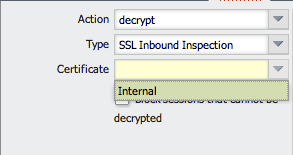
Note: This decryption mode can only work if you have control on the targeted Web Server certificate to be allow to import Key Pair on Palo Alto Networks Device. That's why this decryption mode is often use to decrypt SSL inbound traffic to Internal Web Server.
- External Client is trying to reach out an internal site www.domain.com with https. Traffic is matching the decryption policy.
- Our SSL Proxy Engine is starting to eavesdrop the SSL session with associated Key Pair.
- SSL request is sent to Web Server without being proxied.
- PAN-OS will inspect Server-Hello message during handshake to verify if both certificates (sent by the server and used in 2) are matching.
- If there is a match, decryption will be successful for the rest of the session; otherwise, decryption will be failing (dedicated global counters will be raised).
See also
SSL decryption resource list
The SSL decryption resource list has a long list of articles dealing with SSL decryption only.
owner: nbilly
