What is Application Dependency?
Application Dependency or "Depends on Applications" (how it is listed inside of the Application details inside of Objects > Applications > application detail window) is a list of other applications that are required for this application to properly work.
Why is it important to you?
If you do not allow the application and its dependency through the Palo Alto Networks firewall, then the application will not work.
Note: There is also a "Implicitly Use Applications" field that you need to recognize.
The "Implicitly Use Applications" is a subset of "Depends on Applications", whereby the dependent applications are implicitly allowed. The application still does depend on these applications, however they do not need to be explicitly permitted in security policy. Dependent applications can be allowed implicitly, when the firewall is able to determine the correct application by a specific point in the session.
For more information on checking Application Dependency, please see this doc:
How to Check if an Application Needs to have Explicitly Allowed Dependency Apps
Lets take two applications as examples; 'facebook-base' and 'facebook-posting'.
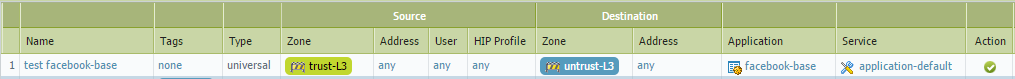
'facebook-base'

When we look at the application detail window for 'facebook-base', you can see 2 things listed.
- Depends on Applications is blank. This means that it does not need any other applications to be allowed in the same rule for this to work.
- Implicitly Use Applications has SSL and web-browsing listed. This means that if you allow facebook-base, that it will also be allowing SSL and Web-Browsing applications implicitly.
So, if you allow 'facebook-base' in a rule no other applications are needed.
'facebook-posting'
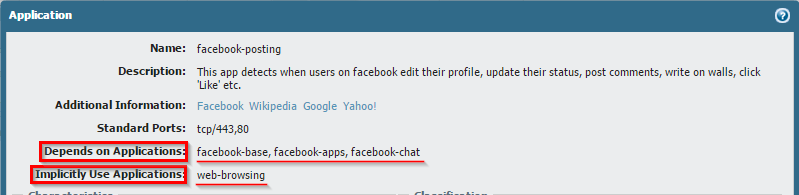
When we look at the application detail window for 'facebook-posting', you can see 2 things listed.
- Depends on Applications has the following applications listed: facebook-base, facebook-apps and facebook-chat. This means that in order for this to work, one or more of the above applications need to be allowed in the same rule for this to work.
- Implicitly Use Applications has web-browsing listed. This means that if you allow facebook-posting, that it will also be allowing the Web-Browsing application implicitly.
So, in order to allow facebook-posting application, you need to have one of the following apps need to be allowed in the same rule to allow facebook-posting through at that security rule depending on what is to be allowed:
- facebook-apps
- facebook-chat
- facebook-posting
As well as facebook-base.
I was able to test this with the following rule, which allowed me to post on facebook.
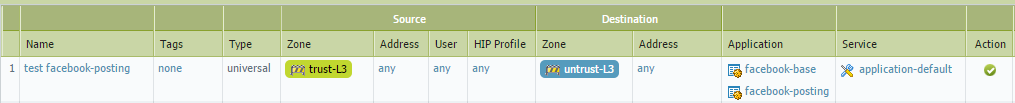
If you wanted to chat, then facebook-base and facebook-chat would need to be allowed in the same rule.