When choosing the action to take with threat signatures at the rule level, pre PAN-OS 7.0 versions provided only allow/alert/block options. Some customers would like more granular control over the session handling when a threat is encountered. For example, some users may prefer silent drops, whereas others may prefer client-side resets. In pre PAN-OS 7.0 versions, the only way to get this control is at the signature exception level. As a result, customers need to create threat exceptions for every signature in order to get this level of control over the action. This solution isn't scalable.
Starting from PAN-OS 7.0, we've added more actions, allowing more control over the firewall responses to threat events.
Reset Server
For a TCP packet, it is self-explanatory because it will reset the server.
For UDP, this action does a 'Drop'.
For the SMTP decoder, this action maps to SMTP 541 response with a server reset.
Reset Client
For a TCP packet, it is self-explanatory because it will reset the client.
For UDP, this action does a 'Drop'.
For the SMTP decoder, this action maps to SMTP 541 response with a client reset.
Reset Both
For a TCP packet, it is self-explanatory because it will reset both client AND server.
For UDP, this action does a 'Drop'.
For the SMTP decoder ,this action maps to SMTP 541 response with a server and client reset.
The screenshots below illustrate the difference between pre PAN-OS 7.0 and PAN-OS 7.0 onwards.
Under Objects tab > Security Profiles > Antivirus Profile > Antivirus > Decoder Actions
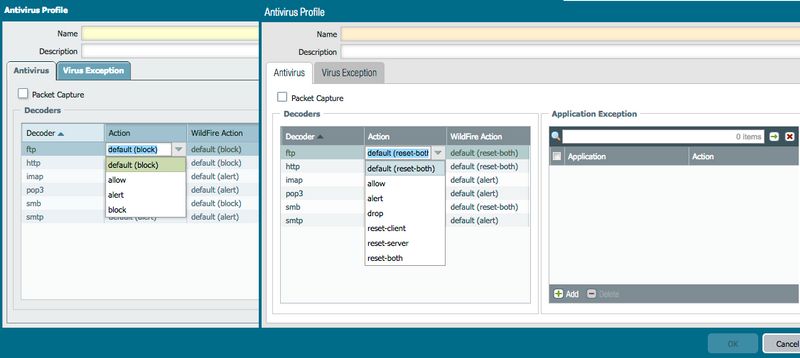 Added Actions from PAN-OS 7.0 Onwards
Added Actions from PAN-OS 7.0 Onwards
Under Objects tab > Security Profiles > Antivirus Profile > Wildfire Actions
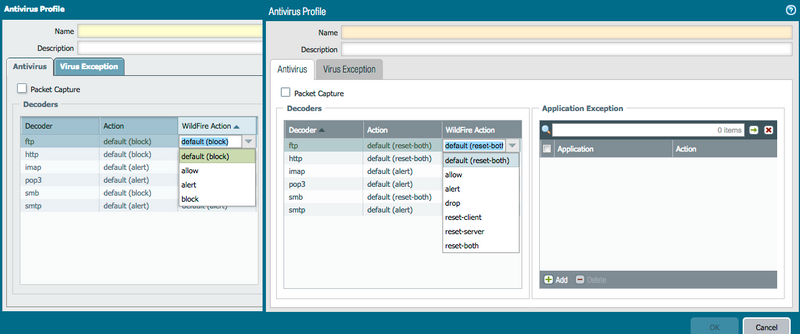 Added Action from PAN-OS 7.0 Onwards
Added Action from PAN-OS 7.0 Onwards
Under Objects tab > Security Profiles > Antivirus Profile > Application Exceptions
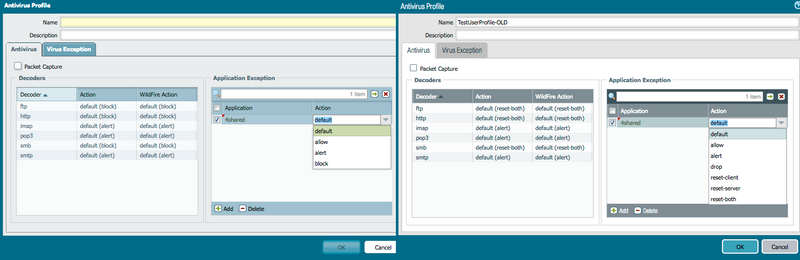 Added Action for PAN-OS 7.0 Onwards
Added Action for PAN-OS 7.0 Onwards
We are doing the same for Anti-Spyware Profiles.
Under Objects tab > Security Profiles > Anti-Spyware
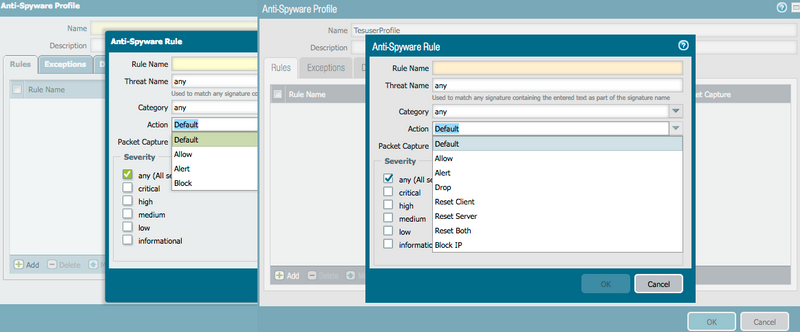 Added Action from PAN-OS 7.0 Onwards
Added Action from PAN-OS 7.0 Onwards
We are doing the same thing for Vulnerability Protection.
Under Object tab > Security Profiles > Vulnerability Protection
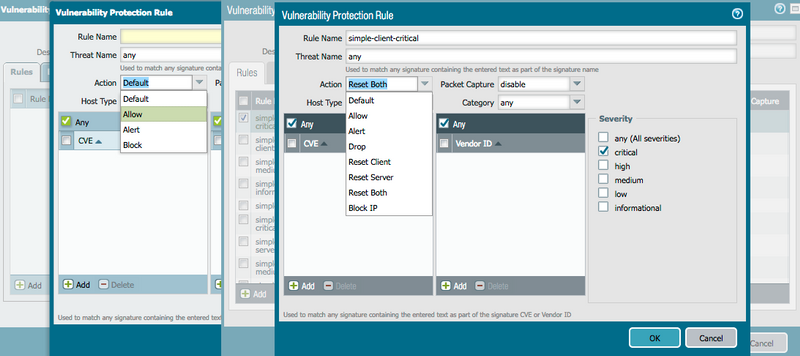 Added Actions from PAN-OS 7.0 OnwardsNote that for Custom Vulnerability signatures, we already had the Reset Both, Reset Client, Reset Server options. We added an Allow action from PAN-OS 7.0 onwards. Below screenshots illustrate the change from pre PAN-OS 7.0 to PAN-OS 7.0 onwards.
Added Actions from PAN-OS 7.0 OnwardsNote that for Custom Vulnerability signatures, we already had the Reset Both, Reset Client, Reset Server options. We added an Allow action from PAN-OS 7.0 onwards. Below screenshots illustrate the change from pre PAN-OS 7.0 to PAN-OS 7.0 onwards.
Objects tab > Custom Objects > Vulnerability
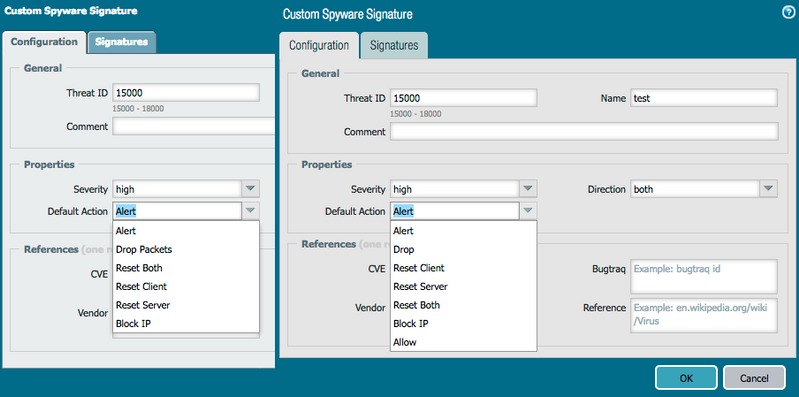
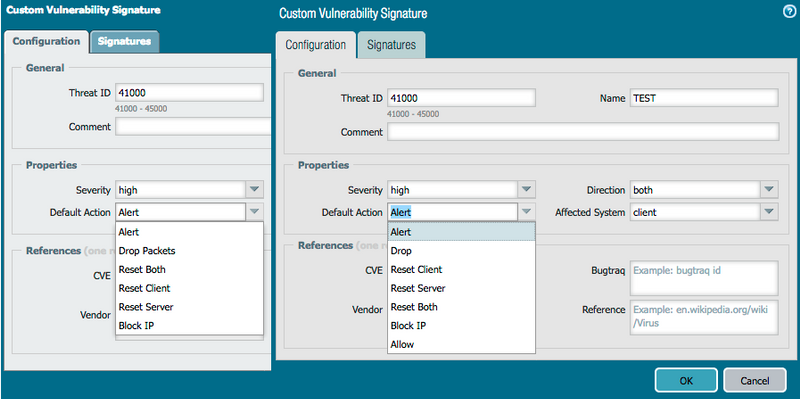 Added Action from PAN-OS 7.0 OnwardsWe did the same for Custom Spyware.
Added Action from PAN-OS 7.0 OnwardsWe did the same for Custom Spyware.
Under Objects tab > Custom Objects > Spyware
 Added Actions from PAN-OS 7.0 OnwardsNotice that the new actions will also be logged in the threat logs :
Added Actions from PAN-OS 7.0 OnwardsNotice that the new actions will also be logged in the threat logs :
 New Actions Also Logged in Threat Log
New Actions Also Logged in Threat Log
How does this translate exactly when you upgrade or downgrade?
The tables below illustrate the mapping of the actions upon upgrading or downgrading:
UPGRADING from a pre PAN-OS 7.0 version to PAN-OS 7.0 or later
| Pre PAN-OS 7.0 | PAN-OS 7.0 or later |
|
Default
Block
Block IP
Allow
Alert
drop-all-packets
drop-packets
|
Default
Reset Both
Block IP
Allow
Alert
Drop
Drop
|
DOWNGRADING from a PAN-OS 7.0 or later to a pre PAN-OS 7.0 version
| PAN-OS 7.0 or later | Pre PAN-OS 7.0 |
|
Reset Server
Reset Client
Reset Both
Drop
Block IP
Allow
Alert
|
Block
Block
Block
Block
Block IP
Allow
Alert
|
Cheers!
-Kim.