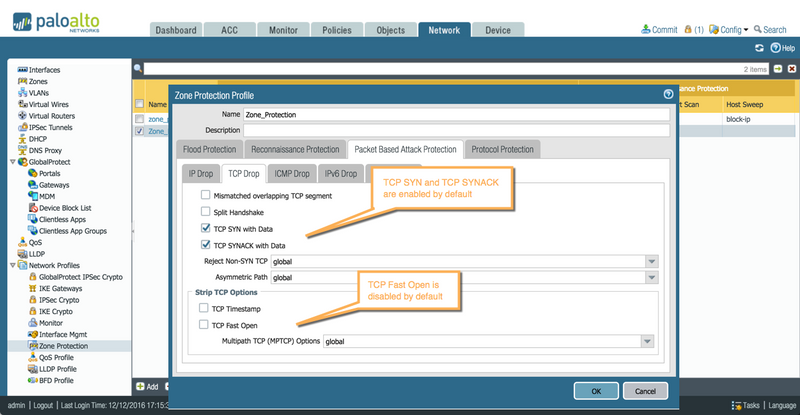
- Syn and Syn-Ack data checks will be enabled by default upon creation of a zone protection profile.
- Syn and Syn-Ack with TCP Fast Open option is allowed by default. Enabling 'TCP Fast Open option' “strips” TFO option in addition to the data payload for both SYN and SynAck packets
- If Syn Cookie is enabled and activated with TCP Fast Option not checked, Palo Alto device will still strip data payload in addition to TFO option which retains Syn Cookie behavior.
Handling of TCP Syn/SynAck packets with data payload
- Drop Syn packet
- Drop SynAck packet
Handling of TFO packet
- Overwrite TCP Fast Option field “Kind-Length-Data” with “TCP_OPT_NOP” (0x01)
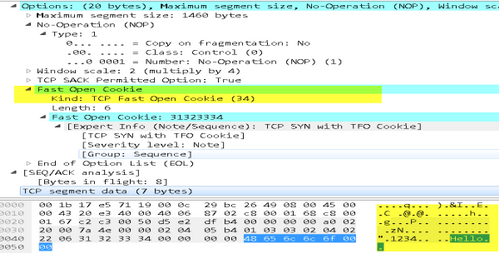
- Packet overwritten with NOP Options
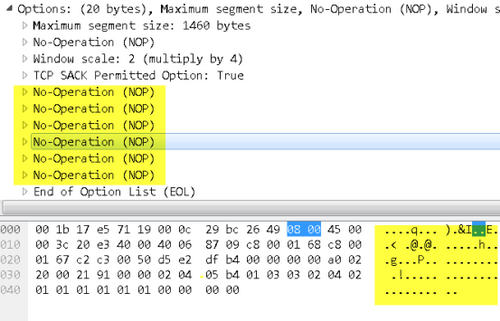
Stripping of data payload consists of the following:
- Modify IP/IPv6 packet to reflect zero L4 segment length
- Recalculate IP/IPv6 TCP checksums
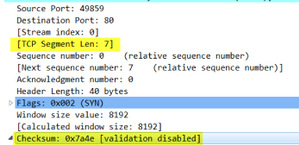
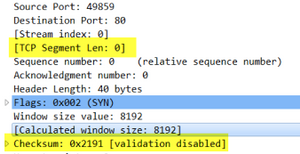
Feature interaction with TCP SYN Cookie
- SYN and SYN-ACK packets with data payload but lacking TFO will be dropped regardless of TCP SYN cookie configuration
- TCP packets with TFO enabled, PANOS will perform rewrite of segment length and recalculate checksums as follows:
- TCP SYN cookie is disabled
- TCP SYN cookie is enabled but not yet activated by zone profile threshold values
- Fallback to existing SYN cookie behavior if enabled and triggered by threshold values
Configuration
CLI Commands
- show zone-protection zone v1-untrust
> show zone-protection zone v1-untrust
------------------------------------------------------------------------------------------
Number of zones with protection profile: 1
------------------------------------------------------------------------------------------
Zone v1-untrust, vsys vsys1, profile Zone_Protection
------------------------------------------------------------------------------------------
tcp-syn SYN cookie enabled: yes
DP alarm rate: 10000 cps, activate rate: 0 cps, maximal rate: 1000000 cps
current: 0 packets
dropped: 0 packets
------------------------------------------------------------------------------------------
IPv(4/6) Filter:
discard-ip-spoof: enabled: yes, packet dropped: 0
discard-ip-frag: enabled: yes, packet dropped: 0
tcp-reject-non-syn: enabled: yes, (global), packet dropped: 0
tcp-timestamp: enabled: yes, packets modified: 0
discard-tcp-syn-with-data: enabled: yes, packet dropped: 0
discard-tcp-synack-with-data: enabled: yes, packet dropped: 0
IPv4 packet filter:
....
- show counter global | match syn
admin@PA-5020> show counter global | match syn
flow_dos_pf_tcpsyndata 126367 489 drop flow dos Packets dropped: Zone protection option 'discard-tcp-syn-with-data'
flow_dos_pf_tcpsynackdata 1000 3 drop flow dos Packets dropped: Zone protection option 'discard-tcp-synack-with-data'
admin@PA-5020> show counter global | match tfo
flow_dos_pm_tcptfodata 21868 1217 info flow dos Packets modified: Zone protection option 'strip-tcp-fast-open-and-data'
.