In this week's Discussion of the Week, we highlight a question posed by user 'merrick' about using a loopback interface in a site-to-site VPN configuration.
Although configuring a site-to-site VPN on a loopback interface introduces additional complexity, some situations may merit its use. A common use case is the need to set the VPN interface to an alternate IP address than the external interface.
The loopback interface must be in the same zone as the external interface (usually referred to as the untrust zone), if not the tunnel traffic would not work, as ESP packets would be dropped.
Refer: ESP packets dropped with error cannot handle IPv4 host bound ESP/AH packet""
VPN Tunnel Traffic Encapsulation Incrementing but no Decaps
The recommended configuration is to make sure the loopback IP address in the same subnet as the external interface.
This setup allows for a seamless configuration, nearly identical to configuring the VPN on the external interface.
The tunnel interface should be in a different zone, allowing for more granular security policies for sessions inside the tunnel.
Below, I'll highlight a less common implementation of performing NAT on an internal loopback in a different zone, to highlight some requirements:
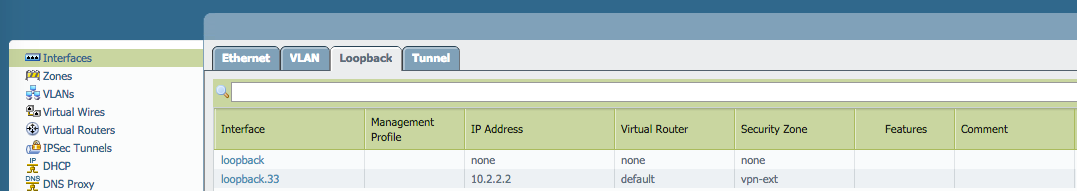
In this example, the loopback interface is set to private IP 10.2.2.2 in the vpn-ext zone:
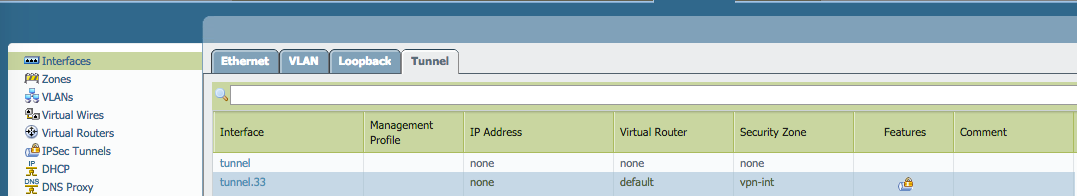
The tunnel interface is set to the vpn-int zone:
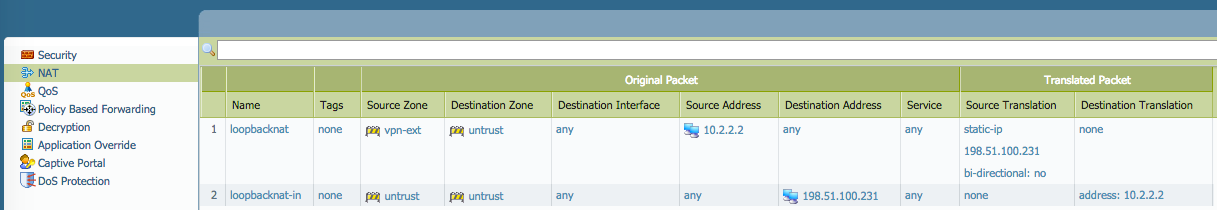
To allow the loopback interface to make outbound and receive inbound VPN connections, create appropriate NAT rules:
And create appropriate security policy to allow the loopback interface to communicate with ipsec peers and the tunnel interface to connect to internal resouces
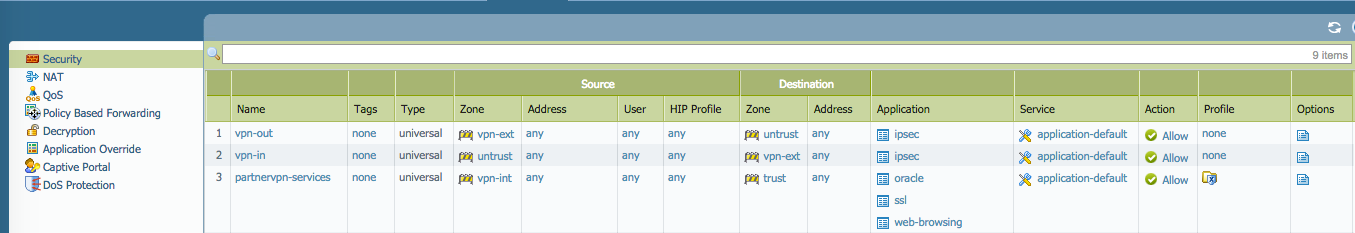
The local IKE gateway can be configured as usual with a static remote peer...
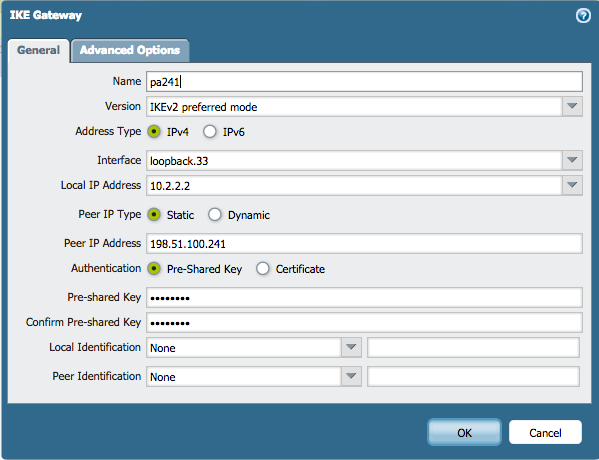
but NAT-T needs to be configured:
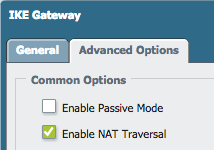
Set the remote peer's configuration for a dynamic peer, including NAT-T:
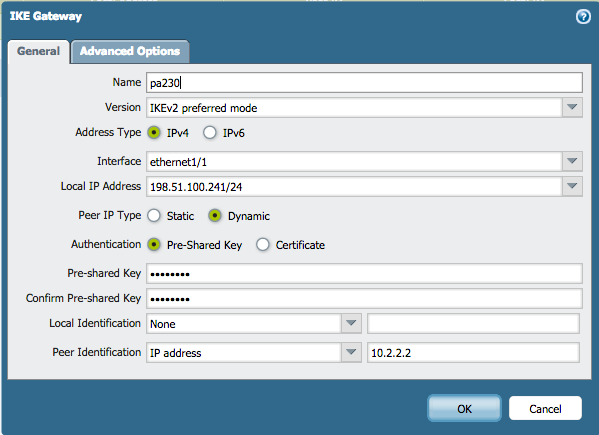
Peer identification on the remote end is required, as the host receives the loopback's private IP as an identification parameter, but the physical IP address is different due to the NAT configurtion.
Lastly, the IPSec Tunnel object can be created without any special configuration:
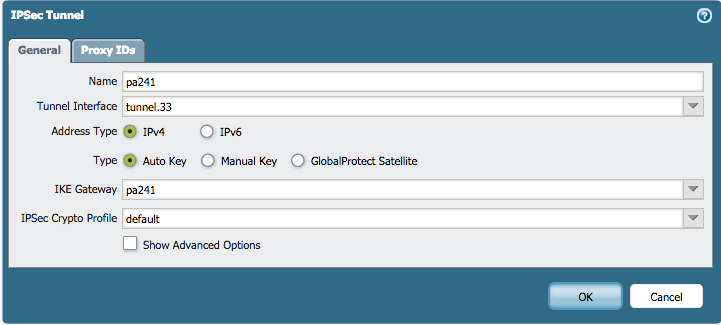
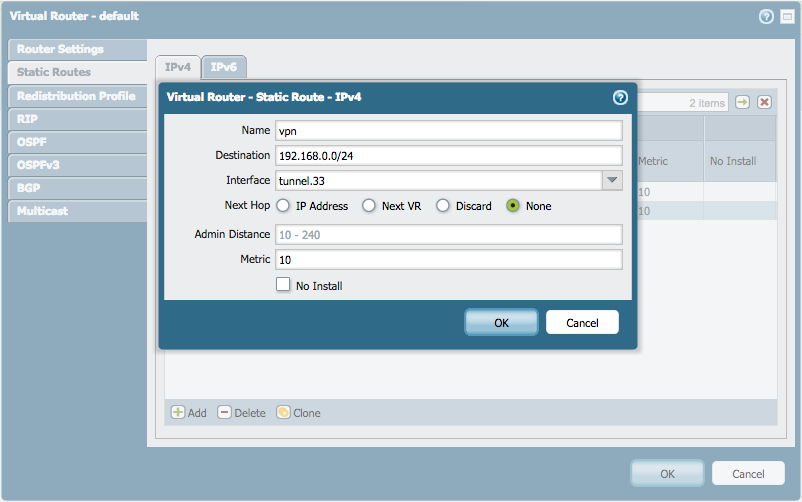
Route the appropriate subnets into the tunnel on either side by adding a route:
To view the discussion, please refer to the following link: Using Loopback interfaces for a site-to-site IPSEC VPN
All comments or suggestions are encouraged.
Thanks for reading!
Tom Piens