The Tor network (The Onion Router) disguises user identity by moving their data across different Tor servers, and encrypting that traffic so it isn't traced back to the user. Anyone who tries to trace would see traffic coming from random nodes on the Tor network, rather than the user's computer.
The following configurations on the Palo Alto Networks Next-Generation firewall can block Tor application traffic on your network.
- Security Policy to Block Tor App-ID
- Use Application Filters
- Block Risky URL Categories
- Deny Unknown Applications
- Blocking Untrusted Issues and Expired Certificates with a Decryption Profile
- Turn on SSL Decryption
- Source/Dest Based Control using External Dynamic List
The above are explained in detail below.
Note: Blocking any evasive application like Tor needs a combination of different capabilities as outlined above. In many cases, just using a single capability is not enough. Use as many of these configurations as needed to properly block Tor.
1. Security Policy to Block Tor App-ID
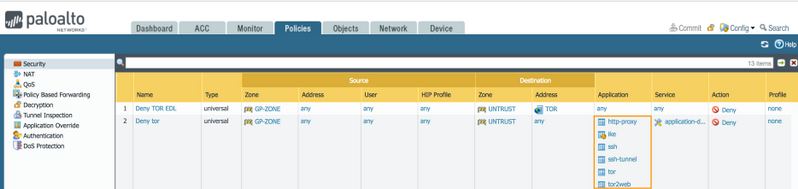
Palo Alto Networks has created applications such as tor and tor2web to identify Tor connections. Like any other anonymizer, Tor uses different techniques to bypass your security. Just blocking tor and tor2web applications in the security policy is not enough.
Create a security policy to block the following applications to the internet:
- tor
- tor2web
- ssh
- ssh-tunnel
- ike
- ipsec-esp
- http-proxy
Inside the WebGUI > Policy > Security, be sure to create a rule that denies access to the above list, and make sure that the "Service" is set to "Application Default".
2. Use Application Filters
There are many avoidance applications out there that are being created as demand rises from users wanting to bypass restrictions. A good way to keep up with new applications is to use application filter and block applications based on behavior rather than manually adding each individual application to the security policy.
Application Filter dynamically groups applications based on the chosen category. More details on how to create application filters can be found in the PAN-OS Administration Guide - Create an Application Filter,
Using Application Filter,(Objects > Application Filters) we can create a new group (Name - VPN) of applications based on the category "networking" and subcategory "proxy". This filter will include applications such as psiphon, tor2web, your-freedom...etc
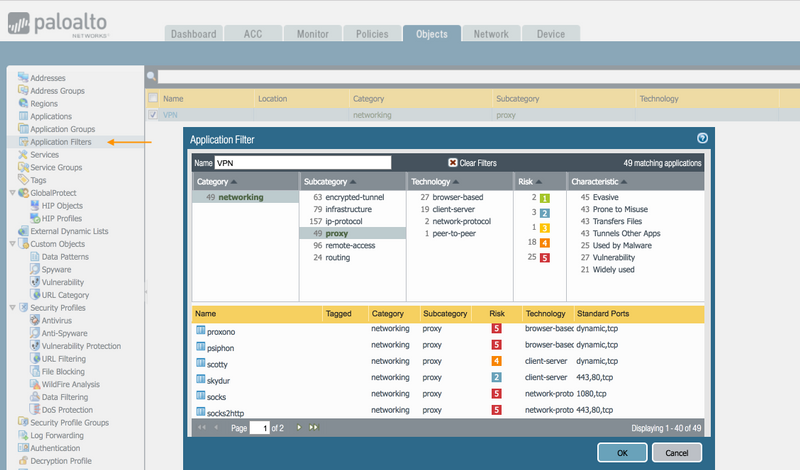
Next, inside Policies > Security, create a security policy to block applications that are subcategorized as proxy. Include the application filter "VPN" in the security policy and set the action to "Deny".
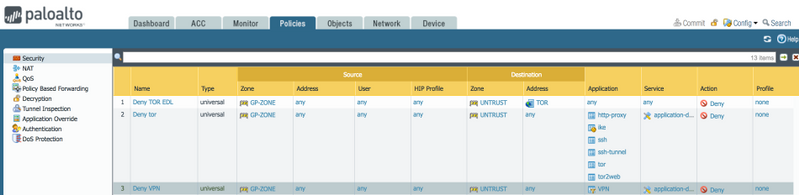
Note: As a best practice, while white listing applications in your security policy, use "application-default" for the Service. The firewall compares the port used with the list of default ports for that application. If the port used is not a default port for the application, the firewall drops the session and logs the message "appid policy lookup deny".
3. Block Risky URL Categories
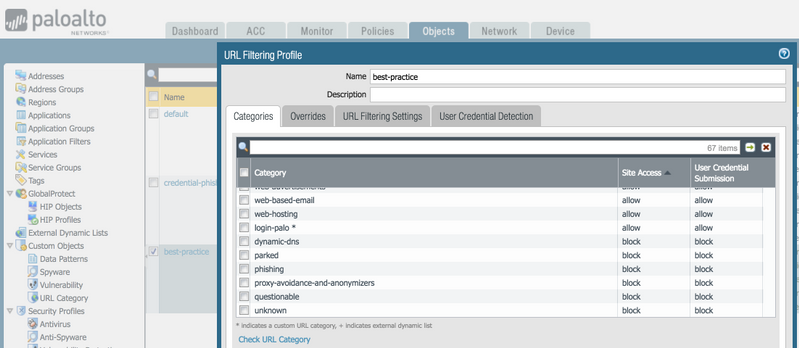
Create URL Filtering profile that blocks access to web sites categorized as:
- proxy-avoidance-and-anonymizers
- malware
- phishing
- dynamic-dns
- unknown
- parked
- phishing
- questionable
Associate the URL Filtering profile to security policy to enforce stricter control. Do this inside Objects > Security Profiles > URL Filtering. Find each category and block access to those categories above.
Note: Please follow the link: Create Best Practice Security Profiles for best practices when it comes to configuring security profiles.
4. Deny Unknown Applications
As a best practice, it is advised to block any applications that are categorized as unknown-tcp, unknown-udp and unknown-p2p in your network.
If there are applications that users need to access in the internet that gets identified by the firewall as unknown-tcp or unknown-udp and if there is a need to allow access to these applications, create a security policy that allows unknown-tcp or unknown-udp on specific ports used by that specific application.
For other traffic that gets identified as "unknown-tcp" or "unknown-udp" or "unknown-p2p", we will create a security policy that denies the traffic.
Make sure you create this rule inside of Policies > Security, to look like below.
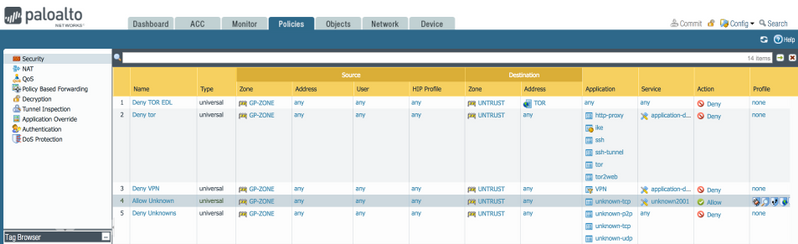
5. Blocking Untrusted Issues and Expired Certificates with a Decryption Profile
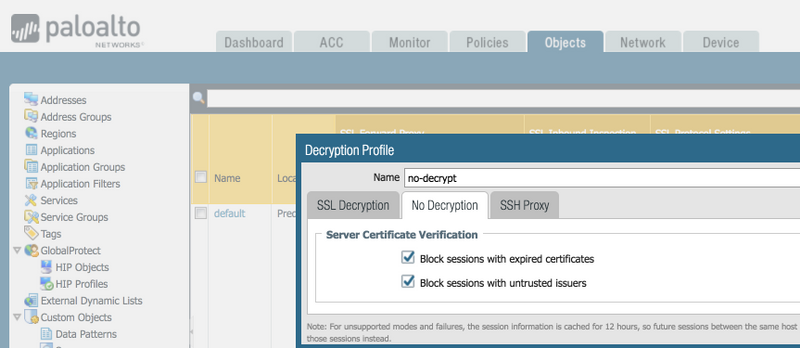
This can be achieved without having to actually decrypt traffic and can be quite effective in blocking Tor. We recommend customers use a "decryption profile" as shown below as part of a no-decrypt rule to limit Tor from connecting.
To do this, go into Objects > Decryption Profile. If you do not already have a no-decrypt rule, please add it with the "Add" button. Inside the "No Decryption" tab, make sure the 2 options are selected.
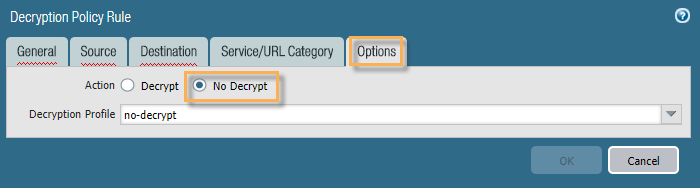
Then inside Policies > Decryption and again, if you do not have a No Decryption rule, please add it with the "Add" button, and then inside of that rule, in the Options tab,
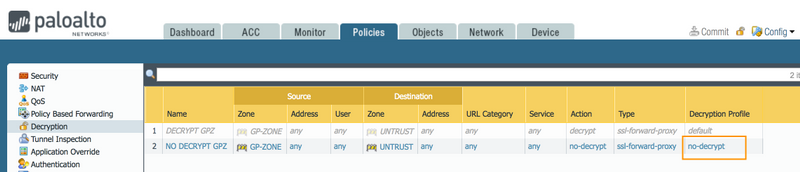
Once done, you should see the Decryption Profile name listed in the rules.
6. Turn on SSL Decryption
If, despite implementing all the controls suggested above, Tor can still connect, then we recommend turning on SSL decryption for this traffic, which will help blocking Tor.
Create a decryption profile iniside Objects > Decryption Profile. Click "Add" at the bottom and give it a name. I used "decrypt". Be sure to select any options for Server Certificate Verification and Unsupported Mode Checks.
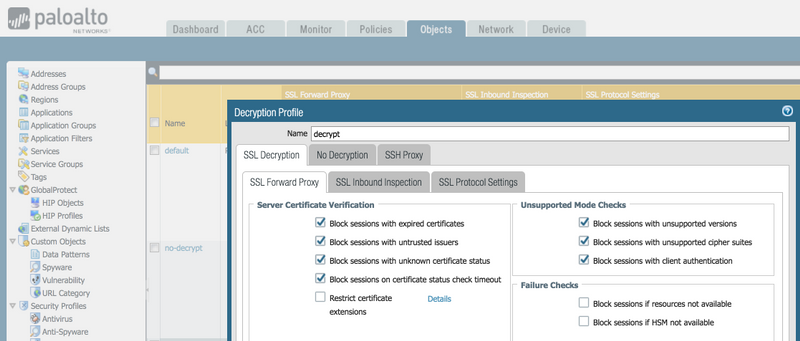
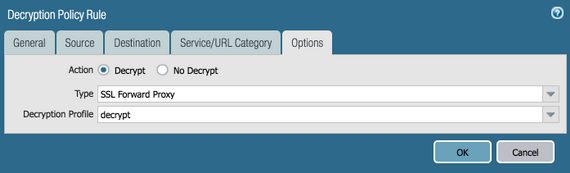
Then be sure to go into Policies > Decryption and associate the decrypt profile to a decrypt policy. Do this inside the "Options" tab inside the Decryption Policy Rule.
For more information on setting up SSL Decryption, please see:
How to Implement and Test SSL Decryption
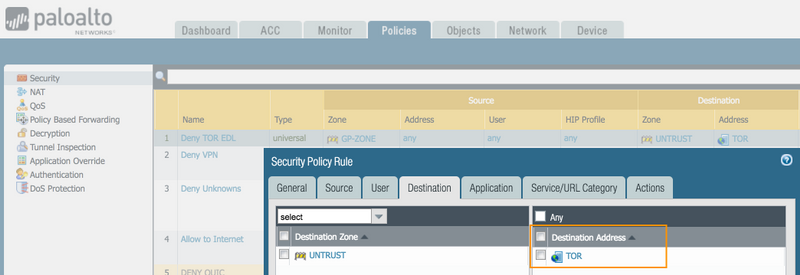
7. Source/Dest Based Control using External Dynamic List
In addition to precautions taken in previous steps to prevent tor traffic, we can use the external dynamic list feature to block connectivity from the Tor application to Tor nodes. This will block based on the destination IP address matching a security policy that has an EDL configured in it.
Note: The documented URLs in the diagram below are currently not available. So one cannot use it as the source of EDL. Instead, one can use the other available exit node list such as https://www.bigdatacloud.com/insights/tor-exit-nodes or https://raw.githubusercontent.com/jtschichold/panwdbl-actions/tor/exit-nodes.txt. Note that these lists/sites are not verified by Palo Alto Networks.
- Please refer to the PAN-OS administration guide to create External Dynamic List.
- Newer content update of Palo Alto (Dynamic Updates 8435 from 7/7/21) supports Built-In External Dynamic Lists. This list can be used in the EDL configuration to block unwanted traffic.
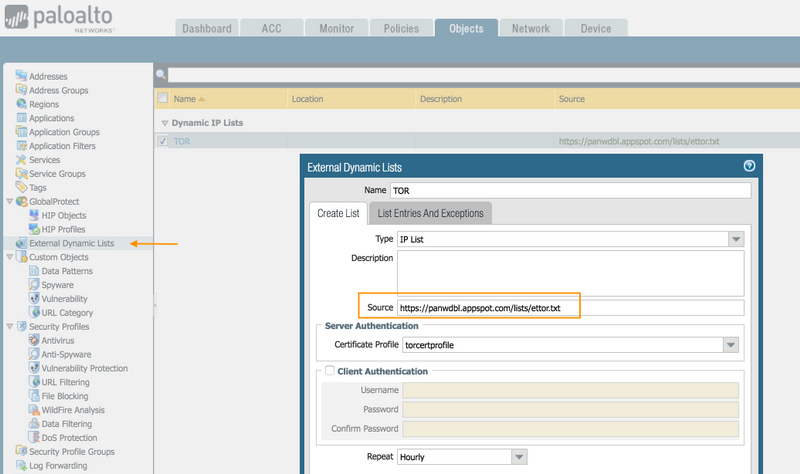
To set the External Dynamic List, go into Objects > External Dynamic Lists and create a new list with "Add". Give it a name - Tor. Be sure to put the URL inside of the source field.
Then inside of Policies > Security, create a new rule (Add) for the new EDL (External Dynamic List).
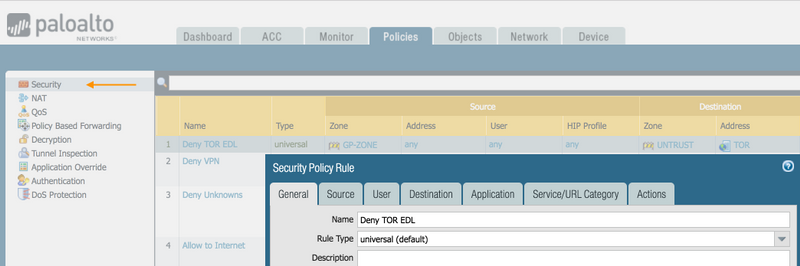
Inside of the Destination tab, be sure to use the EDL you just created "Tor".
Blocking any evasive application like Tor needs a combination of different capabilities as outlined above. In many cases, just using a single capability is not enough.