A session timeout defines how long PAN-OS maintains a session on the firewall after inactivity in the session. By default, when the session timeout for the protocol expires, PAN-OS closes the session.
On the firewall, you can define a number of timeouts for TCP, UDP, and ICMP sessions. The default timeout applies to any other type of session. All of these timeouts are global, meaning they apply to all of the sessions of that type on the firewall.
The Palo Alto Network devices offer optimal values for these timeouts. However, in some scenarios, these values might not work for your network needs. Setting a number too low can cause sensitivity to minor network delays and adversely affect connecting with the firewall. Setting a session timeout that's too high can delay failure detection. In other words, you might find yourself in a situation where you'd like to make some adjustments here and there.
In the WebGUI, you'll find these settings at Device > Setup > Session > Session timeout
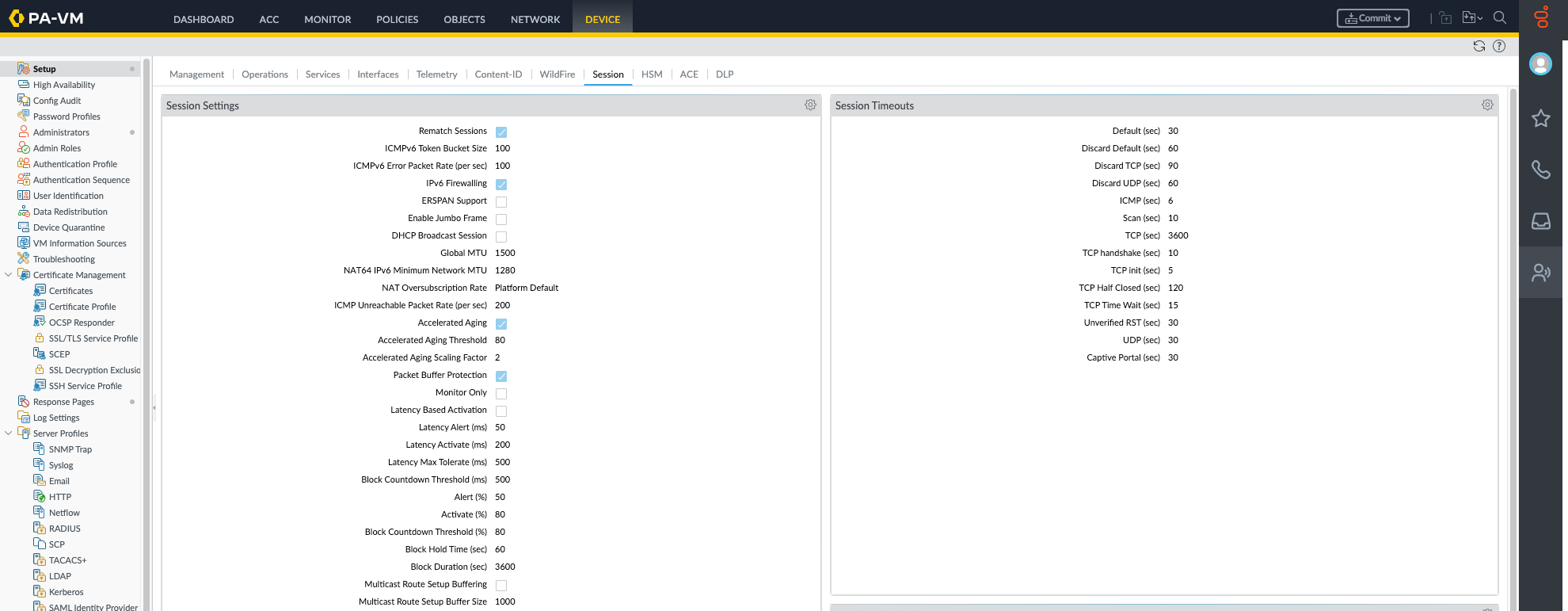
If you need to change the default values of the global session timeout settings for TCP, UDP, ICMP, Captive Portal authentication, or other types of sessions, click the 'Edit' icon:

Note that all the values are in seconds:
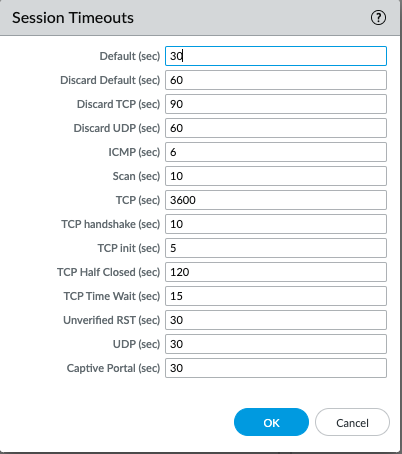
Please refer to the following document for a more detailed explanation about each timeout:
Configure Session Timeouts
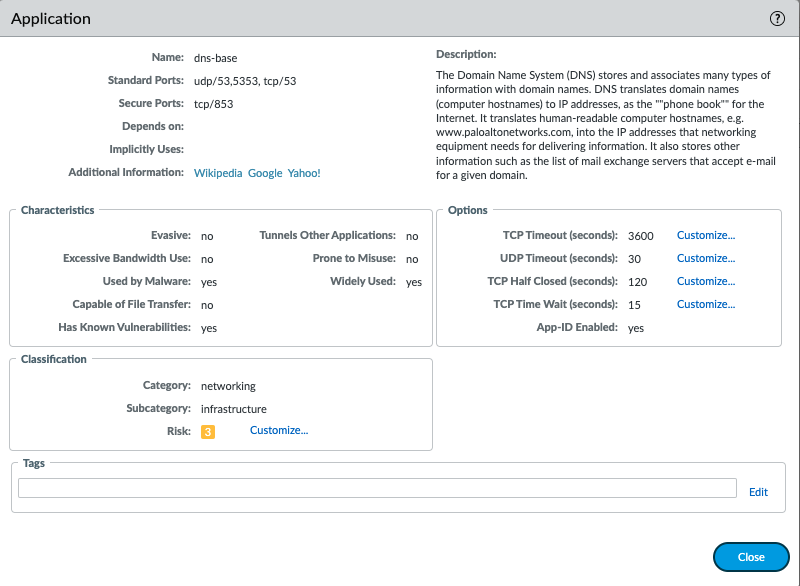
In addition to the global settings, you can optionally define timeouts for an individual application in the Objects > Applications tab. The firewall applies application timeouts to applications in an established state. When configured, timeouts for an application override the global session timeouts.
Only new session will be assessed for modified timeout value, no impact on existing sessions.
Notice the available options for the DNS application in the following example:
Alternatively, you can also use the CLI to view these timeouts:
> show session info
Session timeout
TCP default timeout: 3600 secs
TCP session timeout before SYN-ACK received: 5 secs
TCP session timeout before 3-way handshaking: 10 secs
TCP half-closed session timeout: 120 secs
TCP session timeout in TIME_WAIT: 15 secs
TCP session timeout for unverified RST: 30 secs
UDP default timeout: 30 secs
ICMP default timeout: 6 secs
other IP default timeout: 30 secs
Captive Portal session timeout: 30 secs
Session timeout in discard state:
TCP: 90 secs, UDP: 60 secs, other IP protocols: 60 secs
You can also edit the values in the CLI. Following is the list of global timeout values as seen in operational mode:
> set session timeout-tcp <1-15999999>
> set session timeout-udp <1-15999999>
> set session timeout-icmp <1-15999999>
> set session timeout-default <1-15999999>
> set session timeout-tcpinit <1-60>
> set session timeout-tcphandshake <1-60>
> set session timeout-tcp-half-closed <1-604800>
> set session timeout-tcp-unverified-rst <1-600>
> set session timeout-tcp-time-wait <1-600>
> set session timeout-captive-portal <1-15999999>
> set session timeout-scan <5-30>
> set session timeout-discard-tcp <1-15999999>
> set session timeout-discard-udp <1-15999999>
> set session timeout-discard-default <1-15999999>
Here is the same list with a comment about each timeout:
> set session
timeout-captive-portal set captive portal session timeout value in seconds
timeout-default set session default timeout value in seconds
timeout-discard-default set timeout of non-tcp/udp session in discard state
timeout-discard-tcp set timeout of tcp session in discard state
timeout-discard-udp set timeout of udp session in discard state
timeout-icmp timeout-icmp
timeout-scan application trickling timeout value in seconds
timeout-tcp timeout-tcp
timeout-tcp-half-closed set session tcp half closed timeout value in seconds
timeout-tcp-time-wait set session tcp half closed timeout value in seconds
timeout-tcp-unverified-rst set session tcp timeout value after receiving a RST
with unverified sequence number in seconds
timeout-tcphandshake set session tcp handshake timeout value in seconds
timeout-tcpinit set session tcp initial timeout value in seconds
timeout-udp timeout-udp
Here are examples :
> set session timeout-udp 60
> set session timeout-icmp 15
Note that the above CLI commands are not persistent, meaning that default values return after restarting the device.
To make the changes persistent, you will have to make the configuration changes in configuration mode.
> configure
#
Below is the list of global timeout values as seen in configuration mode and two example commands:
# set deviceconfig setting session
+ timeout-captive-portal set captive-portal session timeout value in seconds
+ timeout-default set session default timeout value in seconds
+ timeout-discard-default set timeout of non-tcp/udp session in discard state
+ timeout-discard-tcp set timeout of tcp session in discard state
+ timeout-discard-udp set timeout of udp session in discard state
+ timeout-icmp set icmp timeout value in seconds
+ timeout-scan application trickling timeout value in seconds
+ timeout-tcp set tcp timeout value in seconds
+ timeout-tcp-half-closed set session tcp half close timeout (after receiving first
FIN/RST) value in seconds
+ timeout-tcp-time-wait set session tcp time wait timeout (after receiving second
FIN/RST) value in seconds
+ timeout-tcp-unverified-rst set session tcp timeout value after receiving a RST with
unverified sequence number in seconds
+ timeout-tcphandshake set tcp handshake session timeout (before 3-way handshaking
is completed) value in seconds
+ timeout-tcpinit set tcp initial session timeout (before SYN-ACK is received)
value in seconds
+ timeout-udp set udp timeout value in seconds
Example commands for setting session timeouts:
# set deviceconfig setting session timeout-captive-portal 60
# set deviceconfig setting session timeout-udp 60
Perform a commit to save changes to the configuration:
# commit
If these global and built-in application timeouts are still too broad, and you'd like more granular control, then configure an application override so that a certain connection triggers a custom application. Like any built-in application, a custom application also has configurable timeouts, as illustrated below:
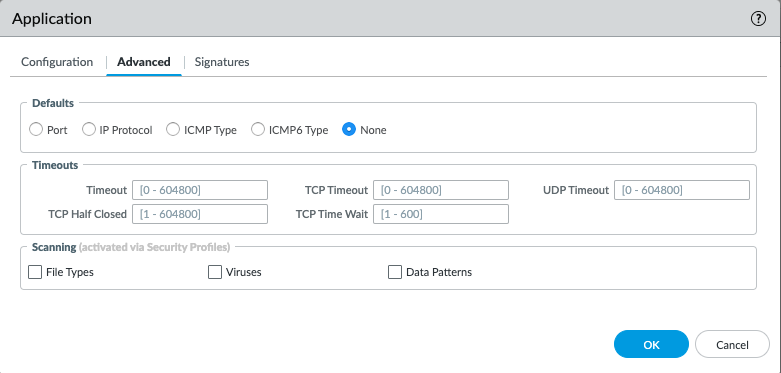
Refer to the following document if you need more information on how to configure an application override:
How to Create an Application Override
As always, feel free to post feedback or comments below.
Please also Like if this article has helped you in any way.
Thanks for reading,
Kim Wens