Last week, community member ghostrider posted an interesting question regarding asymmetric routing. Community members licenselu and pulukas each provided a different solution, which we'll highlight below:
As ghostrider indicates, when outgoing packets egress interface eth1/1 and returning packets ingress on interface eth1/2, a phenomenon called asymmetric routing takes place. The Palo Alto Networks firewall has checks built in to make sure packets follow a logical sequence of events. One expectation is that the packets keep using the same interfaces, as packets coming from a different interface could be an attempt by a malicious source to inject a packet in an active session. If unexpected asymmetry occurs, the packets should be discarded.
If you verify the global counters of your device, you can easily identify these types of packets being discarded if you see these counters:
> show counter global filter delta yes
then search the result or use the "| match " filter for these counters
tcp_drop_out_of_wnd out-of-window packets dropped
tcp_out_of_sync can't continue tcp reassembly because it is out of sync
flow_tcp_non_syn Non-SYN TCP packets without session match
flow_tcp_non_syn_drop Packets dropped: non-SYN TCP without session match
licenselu points out that that the check can be disabled via a zone protection profile on the interfaces' zones.
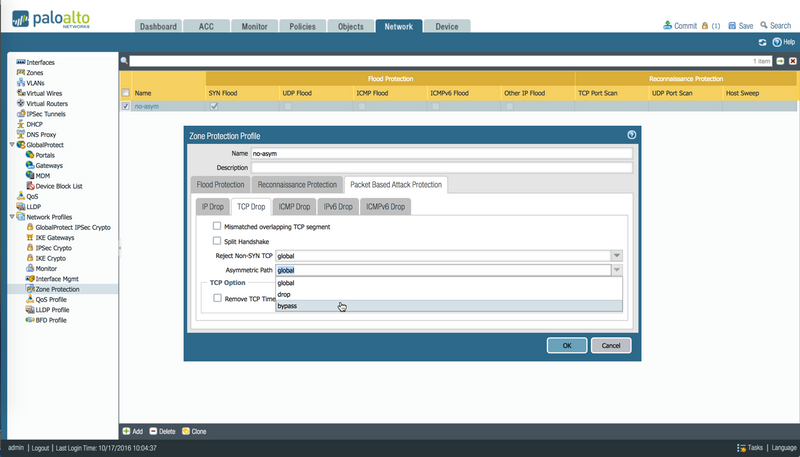
The advantage of this approach is that you can have both interfaces in different zones and can apply more granularity in your security profiles, if needed. The disadvantage is that a low-level session sanity check will be disabled, which may come with implications.
Community member pulukas proposed a second workaround based on how the operating system processes packets and manages flows: the firewall is zone based, which means that for all received packets during the session creation and subsequent packets, a source zone lookup will occur before moving to the next step of matching an existing session. So if both the interfaces are placed in the same zone, they will be treated as the same area and asymmetry will not be applied within the same zone. This way, the asymmetry protection does not need to be disabled.
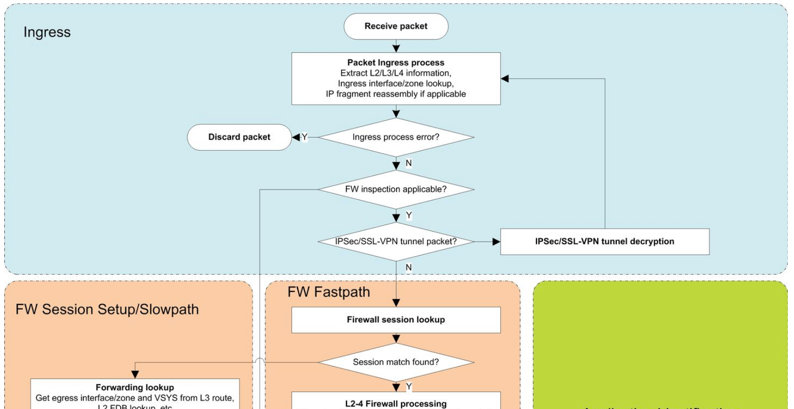
Please check out this article for more information about Packet Flow Sequence in PAN-OS.
Note: It does not apply for Vwire mode in the scenario where the zones are present different VWire group
A big thanks to licenselu and pulukas for helping other community members with sage advise!
Reaper