Overview
This document describes how to enable encryption on HA1 traffic between two Palo Alto Networks firewalls.
Steps
Every Palo Alto Networks firewall has its own high-availability-key that can be used to encrypt HA1 traffic. Before the encryption can be enabled, the key needs to be exported from PA1 and imported into PA2. The PA2 key also needs to be exported and imported into PA1. After the keys are imported, the final step is to have each firewall explicitly accept its peer's DSA key. This operation can only be done via the CLI.
- Export key on PA1.
From the CLI:
> scp export high-availability-key from HA-key-0009C100762 to user@server_ip:/directory
From the GUI:
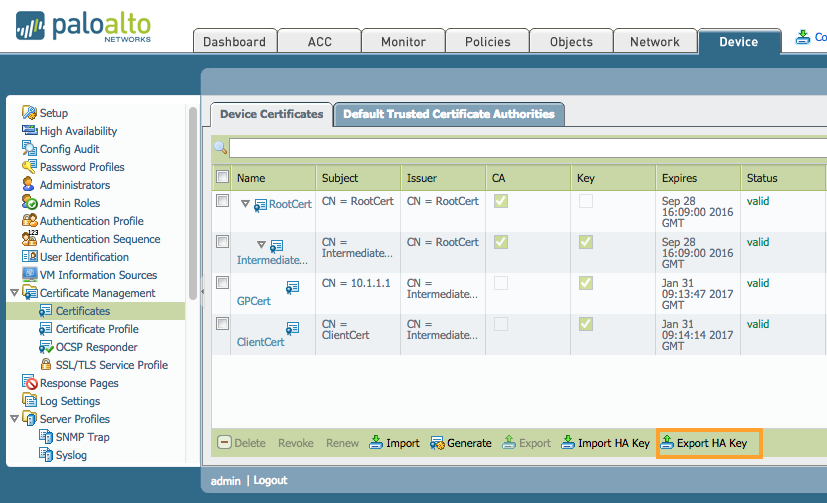
- Import key on PA2.
From CLI:
> scp import high-availability-key from user@server_ip:/directory/HA-key-0009C100762
From GUI:
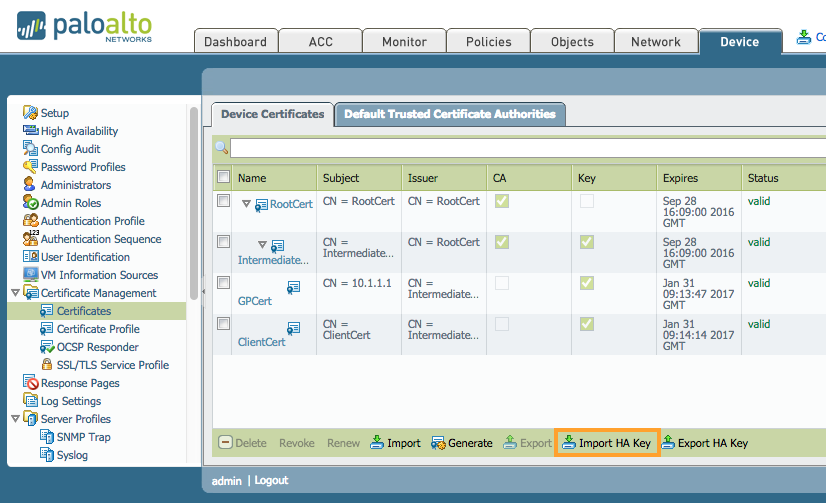
- Repeat steps 1 and 2 above, but export the key from PA2 and import into PA1.
- Enable the encryption and perform a commit on both devices.
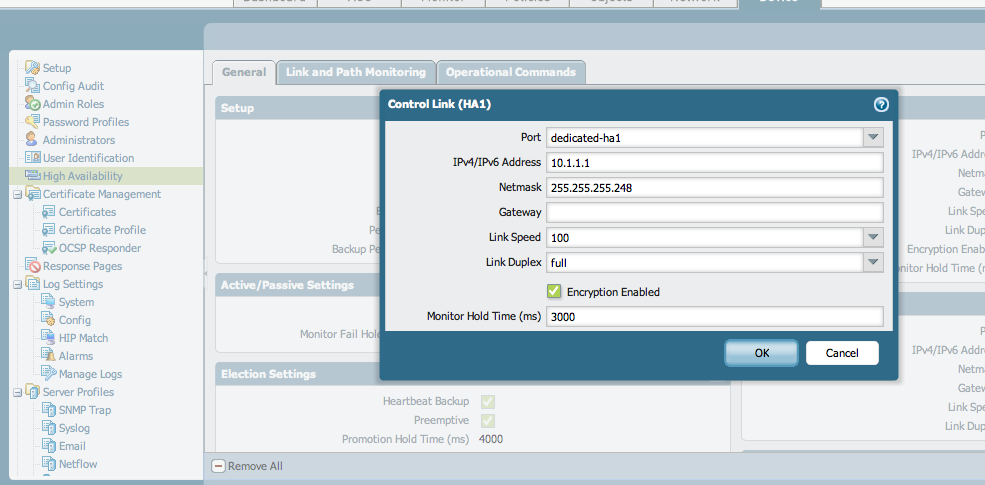
- To finalize the RSA key exchange between HA nodes, access the CLI from each node and SSH to the peer. When prompted to install the RSA token, type yes.
For example:
1.1.1.1 < HA Peer MGT Interface IP address.
admin@PA-3050> ssh host 1.1.1.1
The authenticity of host '1.1.1.1 (1.1.1.1)' can't be established.
DSA key fingerprint is e9:de:76:fb:db:95:98:7d:c8:45:c4:83:dc:35:f1:2b.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '1.1.1.1' (DSA) to the list of known hosts.
admin@1.1.1.1's password:
Additional info
- If you have issues with the key or simply want to renew them, use the following CLI command.
Note: Please be aware that this command will cause the firewall to reboot automatically.
> debug system ssh-key-reset high-availability
Executing this command will reset the high-availability SSH keys and reboot the system. Do you want to continue? (y or n)
Broadcast message from root (Fri Mar 29 10:10:28 2013):
The system is going down for reboot NOW!
- After running the command, it will be necessary to Resync the keys between the two devices by using the SCP export/import commands or through the GUI as previously explained once the device is rebooted
owner: rvanderveken