Site-to-Site IPSec VPN Between Palo Alto Networks Firewall and Cisco Router using VTI Not Passing Traffic
156866
Created On 09/25/18 17:52 PM - Last Modified 10/30/23 23:38 PM
Symptom
- IKE Phase 2 traffic is not being passed between the Palo Alto Networks firewall and Cisco router.
- The Interface Tunnel is Down
- IKE Phase 1 Up but IKE Phase 2 Down
Environment
- Site-to-Site IPSec VPN has been configured between Palo Alto Networks firewall and Cisco router using Virtual Tunnel Interface (VTI)
Cause
The issue may be caused by an IKE Phase 2 mismatch. PFS mismatch.
Resolution
Configure the Palo Alto Networks Firewall and the Cisco router to have the same PFS configuration.
- On the Palo Alto Networks firewall, go to Network > IPSec Crypto.
- Select the crypto profile applied to tunnel as follows and make sure the DH Group values match the ones on the Cisco router.
- On the Cisco router, set the PFS to match the settings on the Palo Alto Networks Firewall.
- Below is an output on Palo Alto Networks Firewall CLI running tail follow yes ikemgr.log. The first highlighted box shows message for a PFS mismatch. The second highlighted box shows the messages after correcting the PFS mismatch.
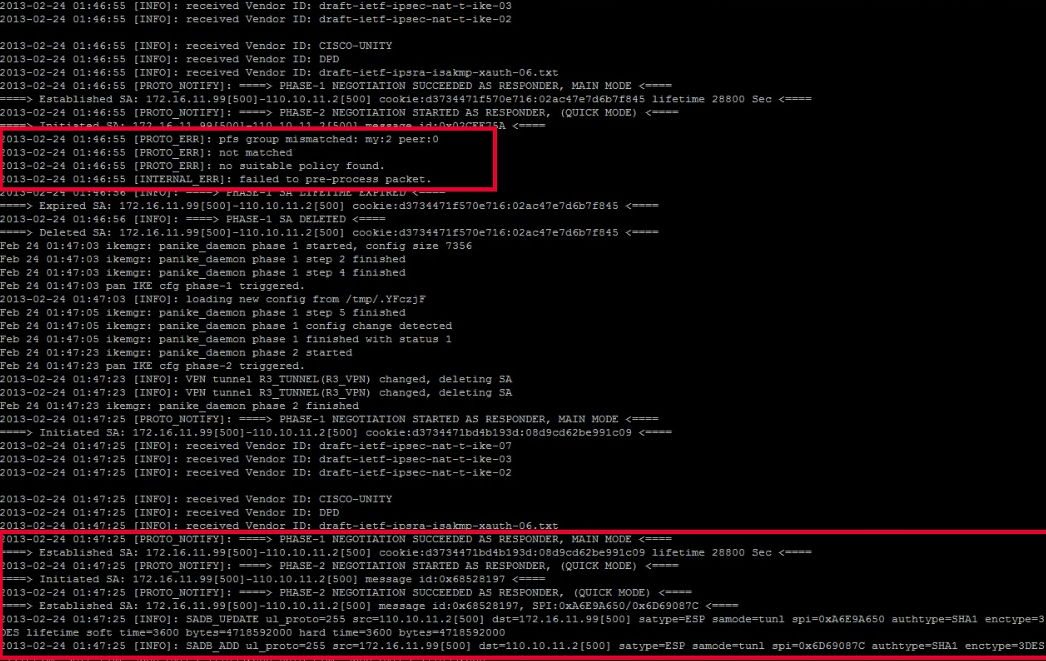
- On the Palo Alto Networks firewall, run show vpn flow tunnel-id <id-number> to check whether encap and decap packets are incrementing.
- On the Cisco router, enter show crypto ipsec sa to check whether encap and decap pcakets are incrementing.