Details
On the Palo Alto Networks firewall, the security zone that is assigned to a specific interface is essential for establishing security policies based on traffic that needs to be allowed, restricted or denied. The same principles of zone selection apply for VPN tunnel interfaces when defining security policies. Two scenarios are shown in this document to demonstrate how security policies are written based on how the security zone for the VPN tunnel interface is chosen:
- The tunnel interface is assigned the same zone as one of the inside interfaces.
- The tunnel interface is assigned an independent zone.
Scenario 1
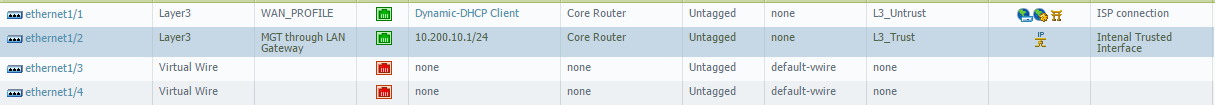
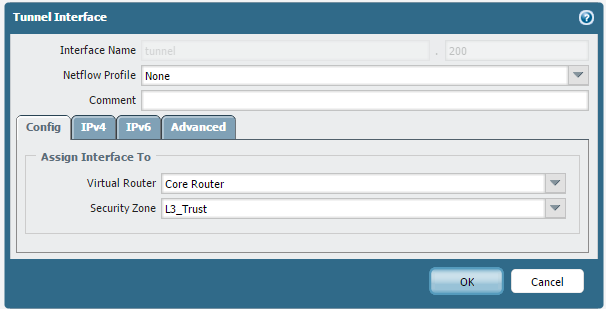
In this scenario, tunnel.200 interface has been assigned to the same zone as the ethernet1/2 interface which is the "L3_Trust" zone. Because of this, any existing security policies (including the implicit 'same-zone' allow rule) that match traffic from source "L3_Trust" zone to destination "L3_Trust" zone will be applied to the VPN traffic flowing between tunnel.200 and inside interface ethernet/12.
Ethernet1/2 is in 'L3_Trust' zone:
Tunnel.200 Interface is placed in the 'L3_Trust' zone:
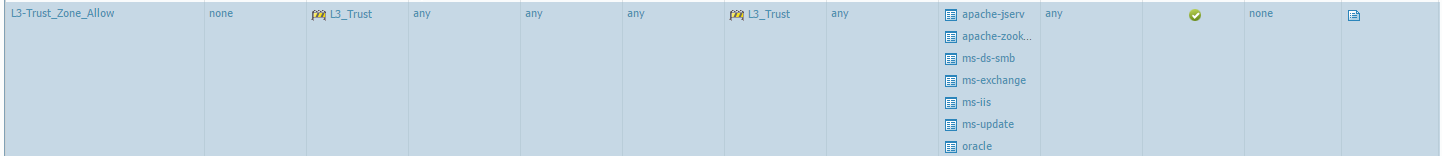
Pre-existing security policy applied to "L3_Trust" zone:
In situations where an "Any/Any/Deny" policy is configured which may override the implicit 'same-zone' policy, a policy must be explicitly created to allow the 'L3-Trust' to 'L3-Trust' zone traffic as shown below:
For more information regarding the Any/Any/Deny policy, see: Any/Any/Deny Security Rule Changes Default Behavior
Scenario 2
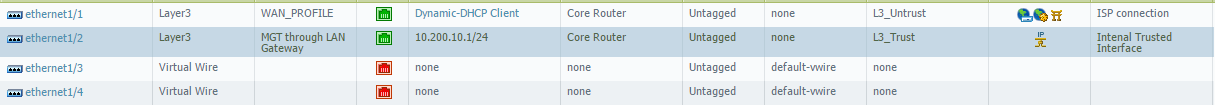
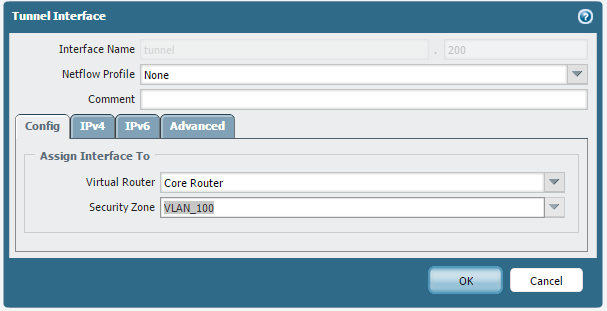
In this scenario, the tunnel.200 interface is assigned an independent zone called 'VLAN_100' while the inside interface ethernet/12 is in the 'L3_Trust' zone:
Ethernet1/2 is in 'L3_Trust' zone:
Tunnel.200 Interface is placed in a separate 'VLAN_100' zone:
This approach will allow for a separate set of restrictions to be applied only to traffic flowing to/from the inside interface(ethernet1/2) to/from the VPN "VLAN_100" security zone. This approach will provide more granularity if the security requirement is different for VPN traffic.
New Security Policy created and applied only for traffic from VPN 'VLAN_100' to inside 'L3_Trust' zone:

See Also
How to Configure IPSEC VPN
owner: jperry