Configured Palo Alto Networks firewalls can establish peer relationships between BGP instances running on separate Virtual Routers (VR) within a single device or a cluster. This enables the firewall to advertise prefixes between Virtual Routers, and direct traffic accordingly.
The two BGP instances must have network communication between two interfaces where each interface is on a different Virtual Router. This can be accomplished by having both VRs connected to the same physical network and ensuring that they belong to the same IP subnet. Communication between the instances leaves the firewall from one interface on one VR onto the physical network and returns on a different interface on the other VR. Another possibility is to have internal communication occur between the BGP instances.
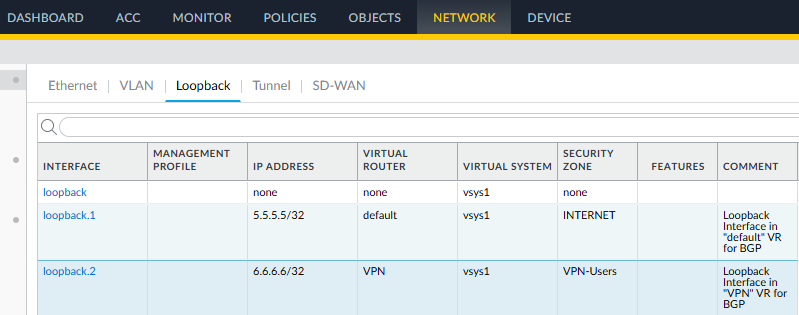
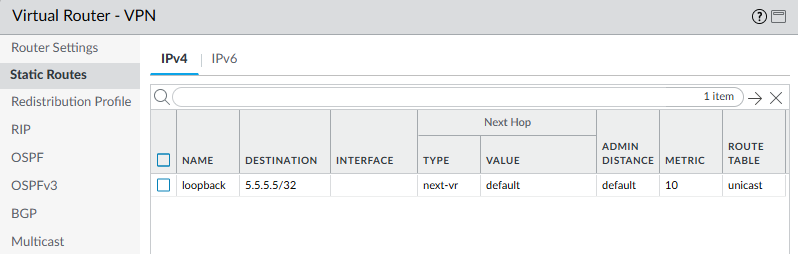
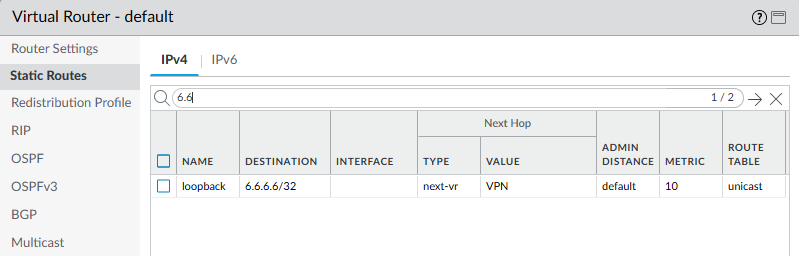
Internal communication between Virtual Routers can be accomplished by configuring two loopback interfaces, each with a /32 network address on each VR. Then configure a static host route (/32 route) on each VR to reach the address of the other loopback interface using the other VR as the next-hop. When configuring the static routes, choose the Next-VR option as the Next-Hop and then give the other VR. The routes accepted by a BGP peer and installed in the routing table will have a next-hop IP address of the other VR loopback interface IP address. Since a route exists to reach that next-hop through the next VR, the packet will be routed into the other VR.
Notes:
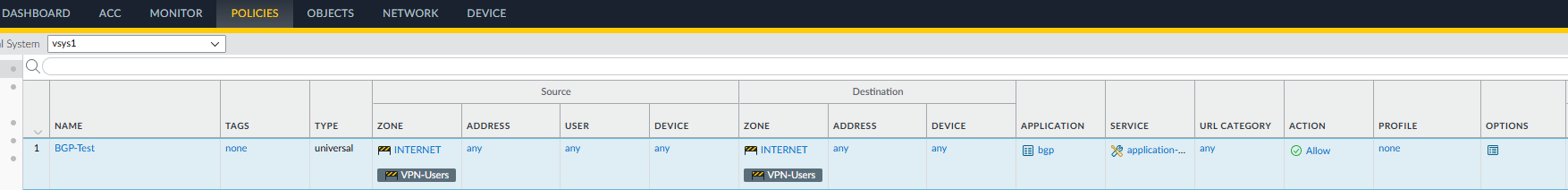
- If the loopback interfaces are set to different zones, then security policies must allow communication between those interfaces in those zones or communication between the peers will fail.
- The destination zone determined for sessions where the first packet is routed from one VR to the other is delayed until the routing decision in the next VR is made and the final destination interface is determined.
Snapshots representing the configuration:
Loopback interfaces: (We can use any /32 IP address for loopback interfaces)
Routing required for BGP to come up:
Security policies required to allow BGP traffic since interfaces are in different zone:
Monitor traffic logs for BGP traffic:
