How to Block a Specific HTTPS Site with URL Filtering
Procedure
Overview
URL filtering presents some challenges when blocking a specific HTTPS site and, at the same time, allowing everything else under that site.
For example, the requirement is to block "https://public.example.com/extension1/a", but allow "https://public.example.com/extension1/b".
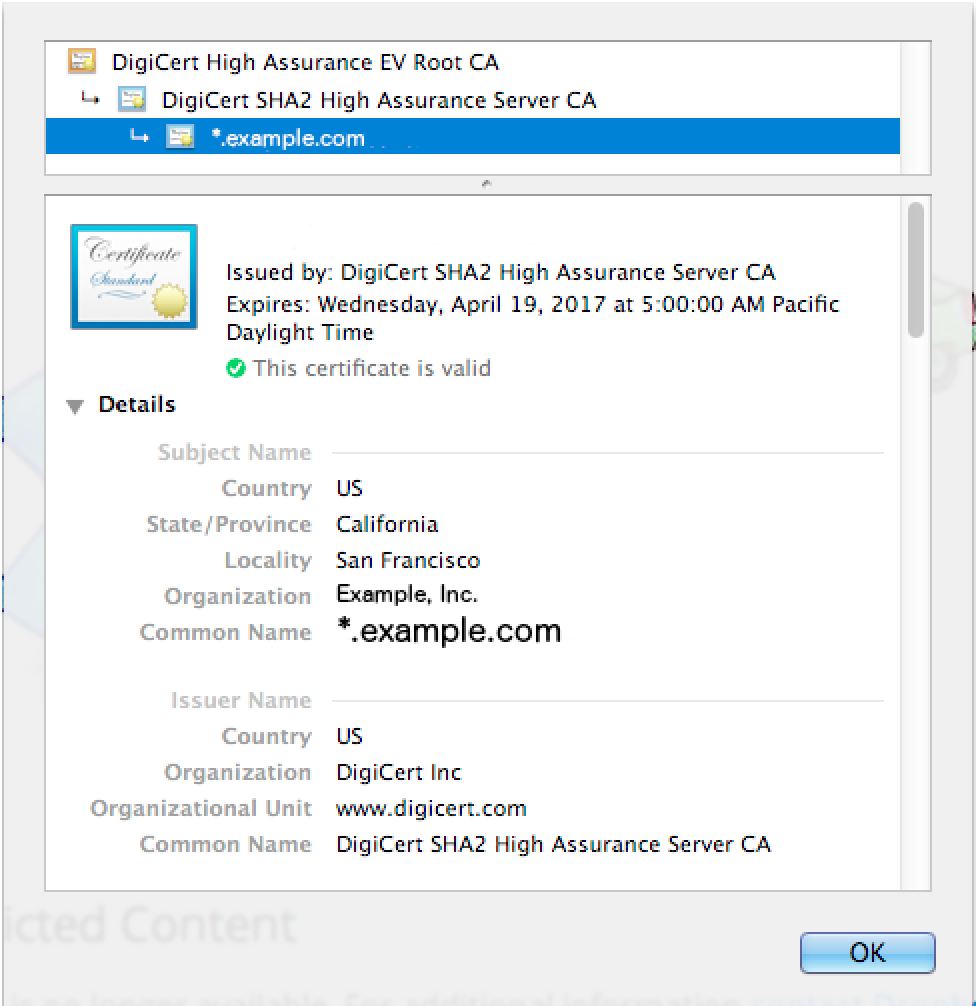
Using Security Policies and Custom URL Categories will only match the "Issued To" Common Name (CN) on the certificate presented by the site.
Note: With the release of PAN-OS 6.0, there is an additional match through the SNI field, which is presented on the SSL Client "Hello message."
The example screenshot below shows the Common Name value as "*.example.com".
A security policy can block "*.example.com", but that will result in blocking the entire site. Since this is not desired result, a URL Filtering Profile needs to be configured. However, the problem with the URL Filtering Profile, is that the firewall needs to look into the session to be able to pick up the full URL. The session is ssl-encrypted, and the firewall cannot inspect it to apply the URL Filtering unless a decryption policy is enabled on the traffic.
Decryption should be implemented with care. If not already implemented on the firewall, the goal is to configure the decryption to inspect the desired traffic. In a decryption policy, there is an URL category option. Decryption does not know the specific sub-page on the https site required to block, as it works in the same manner as a Security Policy. The Decryption policy will check the "Issued To CN" on the presented Certificate. If it matches the setting under "URL Category", then it will decrypt the SSL session.
This is useful when decrypting traffic only for *.example.com, but applying a URL Filter to block only if a user goes to: public.example.com/extension1/a
Note: "https://" was removed from the above URL.
Steps
Follow the steps shown below to configure the desired behavior:
- Go to Objects > Custom Objects > URL Category, add a custom URL category named "Example Blacklist". Add public.example.com/extension1/a as an URL, do not prepend https:// to the URL list.
- Go to Objects > Custom Objects > URL Category, add a custom URL category named "Wildcard Blacklist". Add *.example.com to the URL list.
- Go to Objects > Security Profiles > URL Filtering, create an URL Filtering profile named "Blacklisted HTTPS Sites" with "Example Blacklist" Custom URL Category with action *block*
- Go to Policies > Security, add a security policy for trust to untrust traffic named "Deny HTTPS Sites", leave the action to allow, select Profile Settings > Profile Type and select Profiles. Select URL Filtering "Blacklisted HTTPS Sites".
- If you already have SSL Decryption in place, proceed to Step 6. If you do not have SSL Decryption configured, please follow the steps here: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClEZCA0
- After confirming Decryption is configured, go to Policies > Decryption, add a Decryption Policy named "Decrypt Blacklisted Sites", set source zone trust, destination zone untrust, select URL Category "Wildcard Blacklist", and options Action: Decrypt, Type: SSL Forward Proxy.
- Commit, https://public.example.com/extension1/a will now be blocked.
owner: mivaldi