Overview
VPNC is an open-source third-party IPSec VPN client that supports Extended Authentication (X-Auth) and establishes a VPN tunnel to GlobalProtect Gateways for accessing internal corporate networks.
Check the link below for a list of supported X-Auth IPSec clients :
What X-Auth IPSec Clients are Supported ?
This document explains how split tunneling works when a VPNC client is connected to a GlobalProtect Gateway.
Details
- In order to define networks to be accessible from the VPNC client (or) for traffic to be sent over the VPN connection, access routes (also known as split tunneling) need to be added in the GlobalProtect Gateway's client configuration. Refer GlobalProtect Configuration Tech Note
- When access routes are configured on the GlobalProtect gateway, an aggregate route of all the access routes is sent to the VPNC client. If DNS server addresses are included, then they will also be taken into consideration while aggregating the routes.
For example:
If the access routes contain the networks 10.66.22.0/23 and 192.168.87.0/24, then the aggregate route sent to the third-party VPNC client is a default route 0.0.0.0/0 as shown below.
> show global-protect-gateway gateway name test_vpnc
GlobalProtect Gateway: test_vpnc (0 users)
Tunnel Type : remote user tunnel
Tunnel Name : test_vpnc-N
Tunnel ID : 7
Tunnel Interface : tunnel.1
Encap Interface : ethernet1/3
Inheritance From :
Local Address : 10.66.24.87
SSL Server Port : 443
IPSec Encap : yes
Tunnel Negotiation : ssl,ike
HTTP Redirect : no
UDP Port : 4501
Max Users : 0
IP Pool Ranges : 172.16.7.1 - 172.16.7.7;
IP Pool index : 0
Next IP : 0.0.0.0
DNS Servers : 4.2.2.2
: 0.0.0.0
WINS Servers : 0.0.0.0
: 0.0.0.0
Access Routes : 10.66.22.0/23; 192.168.87.0/24;
Access Route For Third Party Client: 0.0.0.0/0
VSYS : vsys1 (id 1)
SSL Server Cert : SERVER_CERT
Auth Profile : vpnc_auth
Client Cert Profile :
Lifetime : 2592000 seconds
Idle Timeout : 10800 seconds
If the access routes contain the networks 10.66.22.0/23 and 10.66.12.0/23, then the aggregate route sent to the third-party VPNC client is 10.66.0.0/19, as shown below.
> show global-protect-gateway gateway name test_vpnc
GlobalProtect Gateway: test_vpnc (0 users)
Tunnel Type : remote user tunnel
Tunnel Name : test_vpnc-N
Tunnel ID : 7
Tunnel Interface : tunnel.1
Encap Interface : ethernet1/3
Inheritance From :
Local Address : 10.66.24.87
SSL Server Port : 443
IPSec Encap : yes
Tunnel Negotiation : ssl,ike
HTTP Redirect : no
UDP Port : 4501
Max Users : 0
IP Pool Ranges : 172.16.7.1 - 172.16.7.7;
IP Pool index : 0
Next IP : 0.0.0.0
DNS Servers : 10.66.22.77
: 0.0.0.0
WINS Servers : 0.0.0.0
: 0.0.0.0
Access Routes : 10.66.22.0/23; 10.66.12.0/23;
Access Route For Third Party Client: 10.66.0.0/19
VSYS : vsys1 (id 1)
SSL Server Cert : SERVER_CERT
Auth Profile : vpnc_auth
Client Cert Profile :
Lifetime : 2592000 seconds
Idle Timeout : 10800 seconds
Note: If the aggregate route sent to the VPNC client is a default route (0.0.0.0/0), then the VPNC client needs to be configured for split-tunneling as shown below.
Navigate to the VPNC client and go to IPv4 Settings > Routes
Add the required access route and ensure that the option "Use this connection only for resources on its network" is checked.
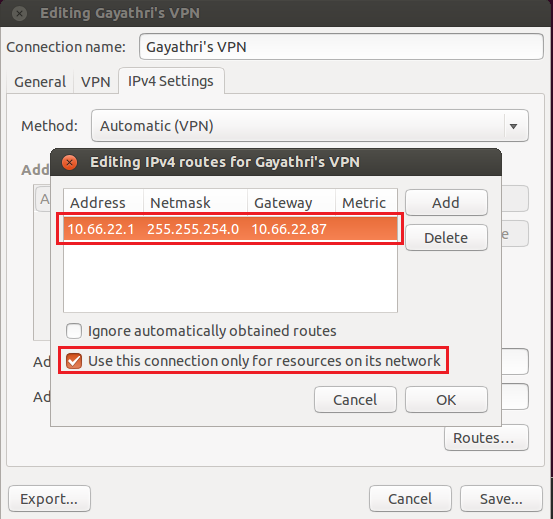
Though the aggregate route sent by GlobalProtect is 0.0.0.0/0, access will only be allowed to the network 10.66.22.0/23 as shown below.
Linux host's terminal output:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:172.16.7.1 P-t-P:172.16.7.1 ask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1412 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueue1en:500
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Access route was not added for 192.168.87.0/24 though the aggregate route sent to the VPNC client was 0.0.0.0/0
tobby@VirtualBox:~$ ping 192.168.87.1
PING 192.168.87.1 (192.168.87.1) 56(84) bytes of data.
--- 192.168.87.1 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2014ms
Access route added for 10.66.22.0/23 in the VPNC client
tobby@VirtualBox:~$ ping 10.66.22.87
PING 16.66.22.87 (16.66.22.87) 56(84) bytes of data.
64 bytes from 10.66.22.87: icmp_req=1 ttl=61 time=6.87 ms
64 bytes from 10.66.22.87: icmp_req=2 ttl=61 time=2.02 ms
--- 16.66.22.87 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 2.021/4.450/6.879/2.429 ms