Topology is as follows:
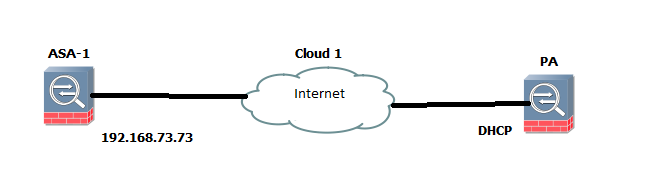
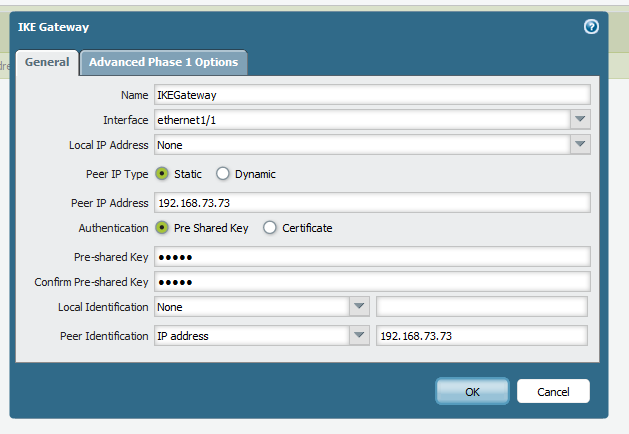
The Palo Alto Networks firewall is getting its IP address from DHCP. We have to configure the IP Sec tunnel between Palo Alto Networks device and Cisco ASA.The only difference on the Palo Alto Networks firewall is in IKE Gateway. The rest are the same as a normal VPN.
Configuration on Cisco ASA.
1. Define Proxy ACL for interesting traffic:
access-list ASA-PA-ACL extended permit ip 10.1.1.0 255.255.255.0 192.168.1.0 255.255.255.0
2. Define Phase 1 policy.
crypto ikev1 policy 110
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 enable inside
3. Define Preshared Key.
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key cisco
4. Define Phase 2 policy.
crypto ipsec ikev1 transform-set TSET esp-aes-256 esp-sha-hmac
5. Create Dyanamic crypto map for create IPSec tunnel with a dynamic peer.
crypto dynamic-map DMAP 110 match address ASA-PA-ACL
crypto dynamic-map DMAP 110 set ikev1 transform-set TSET
6. Bind the Dynamic Crypto map with the Static Crypto Map. If multiple IPSec tunnels are running on Cisco ASA, just use an existing Crypto MAP but with a new number.
crypto map CMAP 10 ipsec-isakmp dynamic DMAP
7. Apply the Crypto map on interface.
crypto map CMAP interface inside