PBF monitoring probes are generated by the dataplane to verify connectivity to a target IP address or to the next hop IP address. If target IP address is reachable, the PBF rule is applied else the traffic goes through normal route lookup phase.
Similarly Tunnel Monitoring probes is a keepalive mechanism for Phase 2 of IPSEC tunnels to monitor a remote IP over the tunnel. If the monitored IP is down, then the Phase 2 SA is deleted and renegotiated if monitor profile is configured as “Fail Over"
Read the following document for the basic use cases of PBF monitoring: Policy Based Forwarding
Read the following document to understand how to select an IP for PBF or Tunnel Monitoring : Selecting an IP Address for PBF or Tunnel Monitoring
Note: PBF does not apply for traffic sourced from the firewall. Read the following document for the same: Policy-based forwarding doesn't work for traffic sourced from the Palo Alto Networks firewall
Tips to remember while using PBF monitoring:
- Probes use ICMP echo requests with the source IP address of the egress interface as configured under the Forwarding tab of the PBF rule.
- Probes do not go through flow module. Route lookup/ policy lookup/ nat lookup etc. do not apply on these probes on the firewall where monitoring is configured.
- Probes are sent out of the same egress interface as configured in the PBF rule, either via the next hop mentioned, or in case of a tunnel interface, via the same tunnel.
- Further down the network, these probes should be treated as normal ICMP echo requests and for probes to be successful, proper Access Lists, routes should be configured.
- Probes are NOT sent out using the interface as returned by route lookup, so pinging the monitored target IP address from dataplane using CLI is not always a valid test to troubleshoot monitoring probe failures.
- Probes do not create sessions, or traffic logs or data plane debug logs or packet captures on the source firewall, so to check them the most appropriate place to check is outside firewall.
- If no IP address is specified for PBF monitoring, then the next hop router is monitored.
See the example of Verification of Monitoring probes in a case where egress interface is a tunnel interface:
Topology
PA1 (tunnel.1:100.1.1.1/32) =========== IPSEC Tunnel ==========(tunnel.1:100.1.1.2/32)PA2 (eth1/4: 30.1.1.1/24)
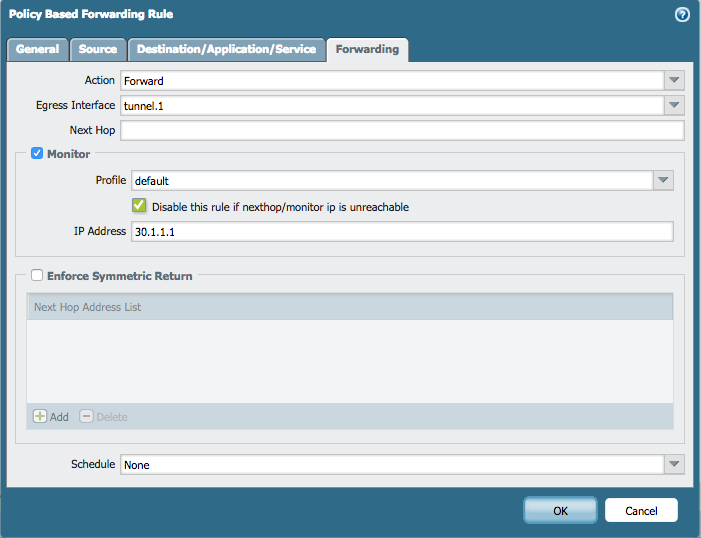
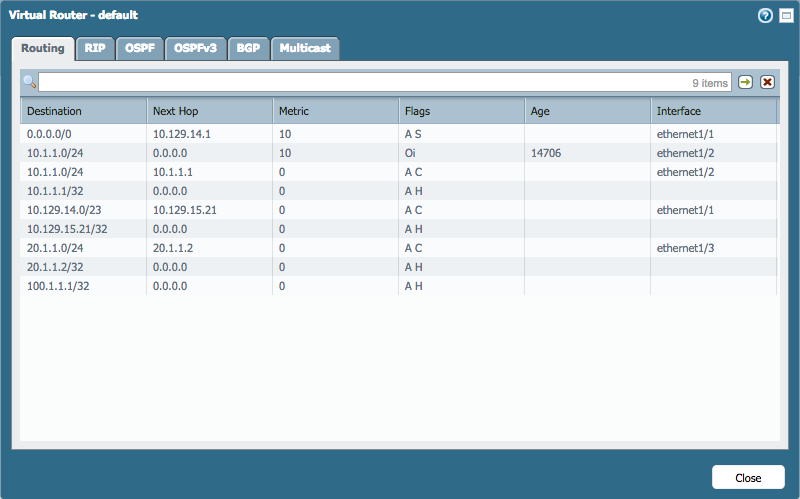
In the above scenario, there is a PBF rule on the PA1 to forward some traffic via tunnel.1. PBF monitoring is enabled with target IP address is 30.1.1.1, which is the ethernet1/4 interface IP on the remote peer.
Tunnel Interface configuration on PA1: (Must have an IP address)
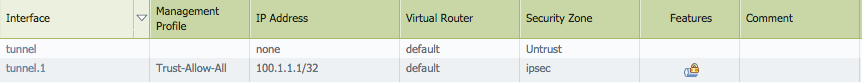
Forwarding tab configuration on PFB rule on PA1:
Routing table on PA1 (No explicit route for target IP 30.1.1.1):
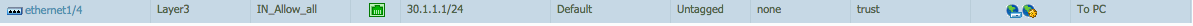
Security Policy to allow the probes on PA2:

Management Profile on ethernet1/4 to allow ping on PA2:
Reverse route for 100.1.1.1/32 (Source IP of probes) on PA2:
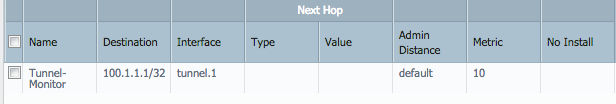
Verification:
PBF rule status on PA1 when target is reachable:
admin@PA-200> show pbf rule name Test-pbf
Rule: Test-pbf(2)
Rule State: Active <<<<<<<<<<<<<
Action: Forward
Symmetric Return: No
Egress IF/VSYS: tunnel.1
NextHop: 0.0.0.0
Monitor Slot: 1
Monitor IP: 30.1.1.1
NextHop Status: UP <<<<<<<<<<<<<
Monitor: Action:Monitor, Interval:3, Threshold:5
Stats: KA sent:1559, KA got:287, Packet Matched:0
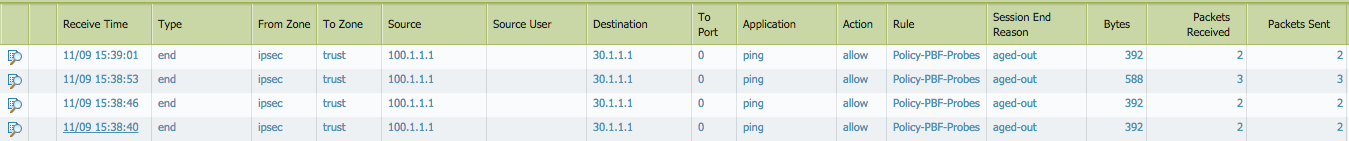
Traffic logs on PA2 showing probe traffic as ping: (Look at the Packets send and received counter)
PBF rule status on PA1 when target is unreachable:
admin@PA-200> show pbf rule name Test-pbf
Rule: Test-pbf(2)
Rule State: Disabled <<<<<<<<<<<<<
Action: Forward
Symmetric Return: No
Egress IF/VSYS: tunnel.1
NextHop: 0.0.0.0
Monitor Slot: 1
Monitor IP: 30.1.1.1
NextHop Status: DOWN <<<<<<<<<<<<<
Monitor: Action:Monitor, Interval:3, Threshold:5
Stats: KA sent:1675, KA got:342, Packet Matched:0
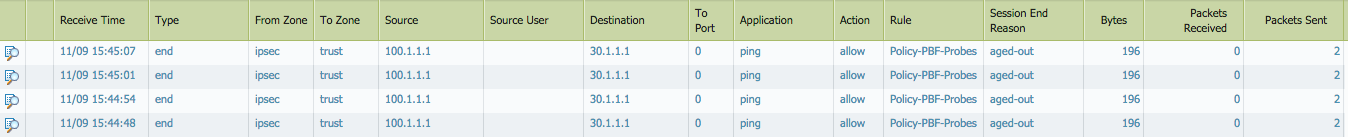
Traffic logs still showing on PA2 (Look at the Packets received counter):
Related Articles:
Policy Based Forwarding Rule is Not Applied when the Monitoring Host is Unreachable
PBF Rule is not Working When PBF Monitoring is Enabled for the IPAcross the Tunnel
How to Configure a Palo Alto Networks Firewall with Dual ISPs and Automatic VPN Failover