The example configuration below is for one portal and one gateway residing on the same Palo Alto Networks device but can be expanded to reflect multiple gateways. Local Database authentication is used for this example but other authentication methods (LDAP, Kerberos, Radius, etc.) can be applied.
- Generate the root Certificate Authority (CA) certificate on the Palo Alto Networks device. This will be used to sign the server certificates for for both GlobalProtect Portal and Gateway, as well as the machine certificate that will be deployed to the client machines.

- Generate the server and machine certificates. Each certificate should be signed by the CA certificate created in Step 1.


3.Device certificates associated with GlobalProtect should appear as follows:

4.Create a Certificate Profile. This will be used to confirm machine certificate validity when cross-checking with the CA Certificate. Make sure to select the CA Certificate when adding 'CA Certificates'.

5. Create your GP Portal as follows:
a.Under Portal Configuration, configure the network and authentication settings. Select the server certificate generated in Step 3 above. For Certificate Profile, select the profile created in Step 4.

b.Under Client Configuration, create a config file. This will be pushed to GlobalProtect clients during initial connection and rediscover network attempts.
Configure the pre-logon client config with pre-logon access method. Configure another config with 'any' user so that all users including pre-logon will get the same config. In the Trusted Root CA section, add the root CA created in Step 1. This certificate will be pushed out to the connecting agents.

6. A sample GlobalProtect Gateway configuration is shown below. Make sure to use the same server certificate and certificate profile used in the GlobalProtect Portal configuration.

7.Next step is to export the machine certificate which will then be added to the trusted certificate store on the local computer. Use the PKCS12 file format and provide a passphrase.

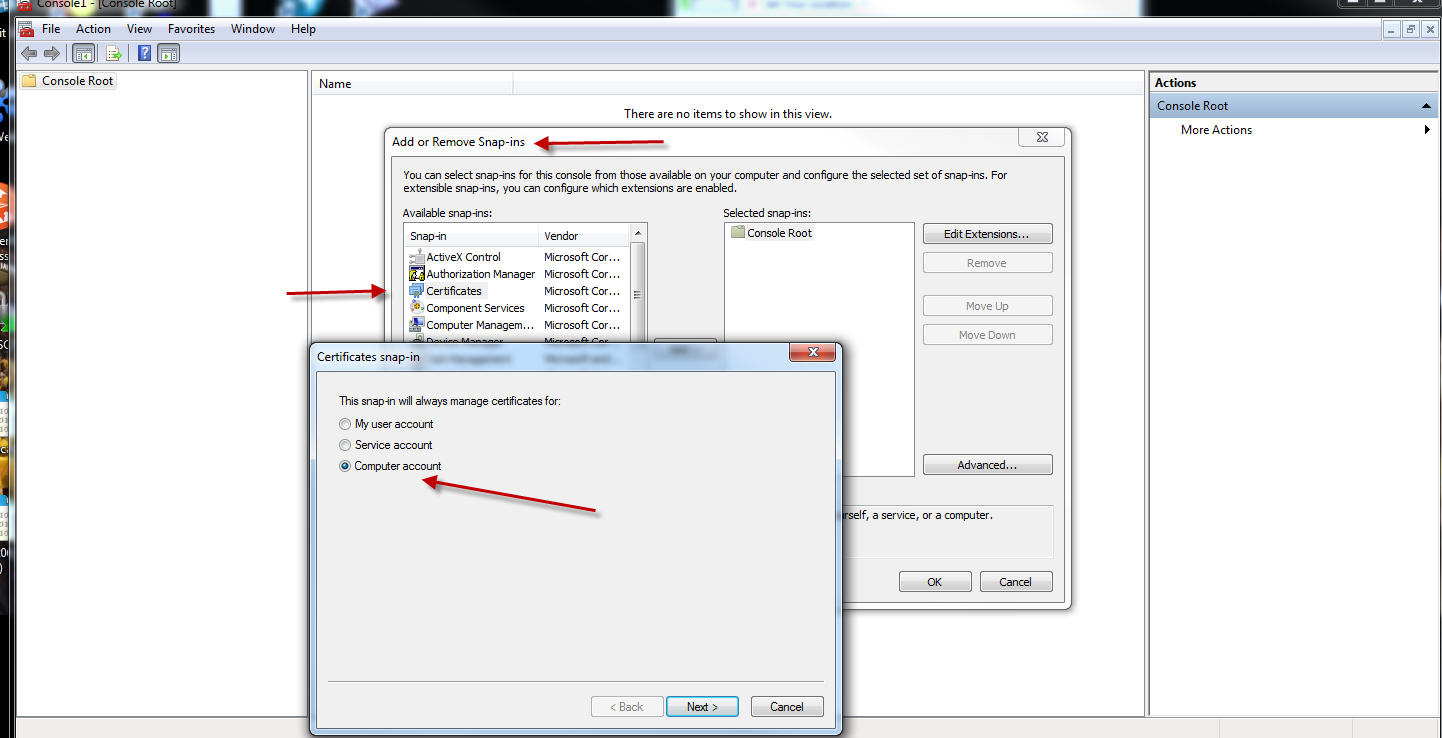
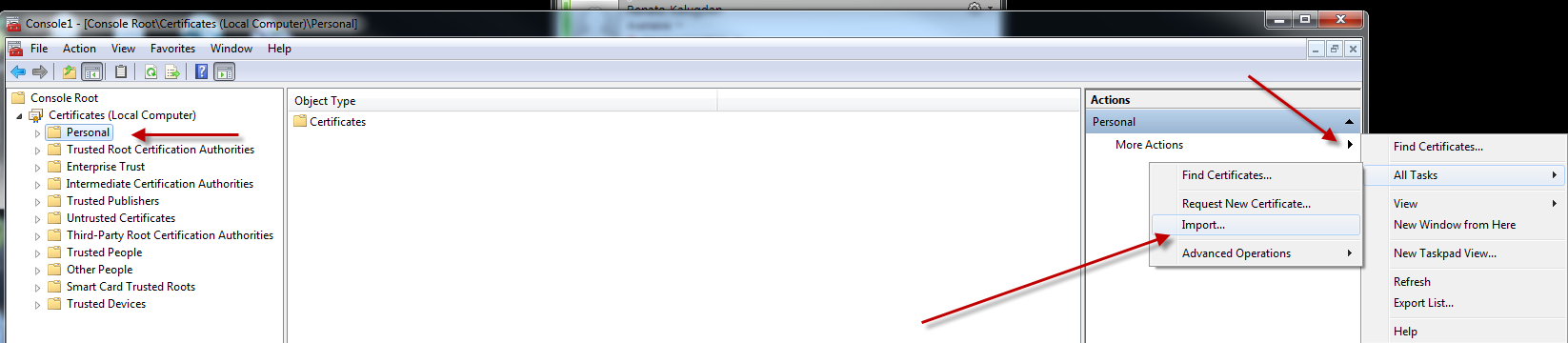
8.On the client machine, import the previously exported machine certificate. The image below demonstrates the use of the MMC certificate snap in for the local computer.
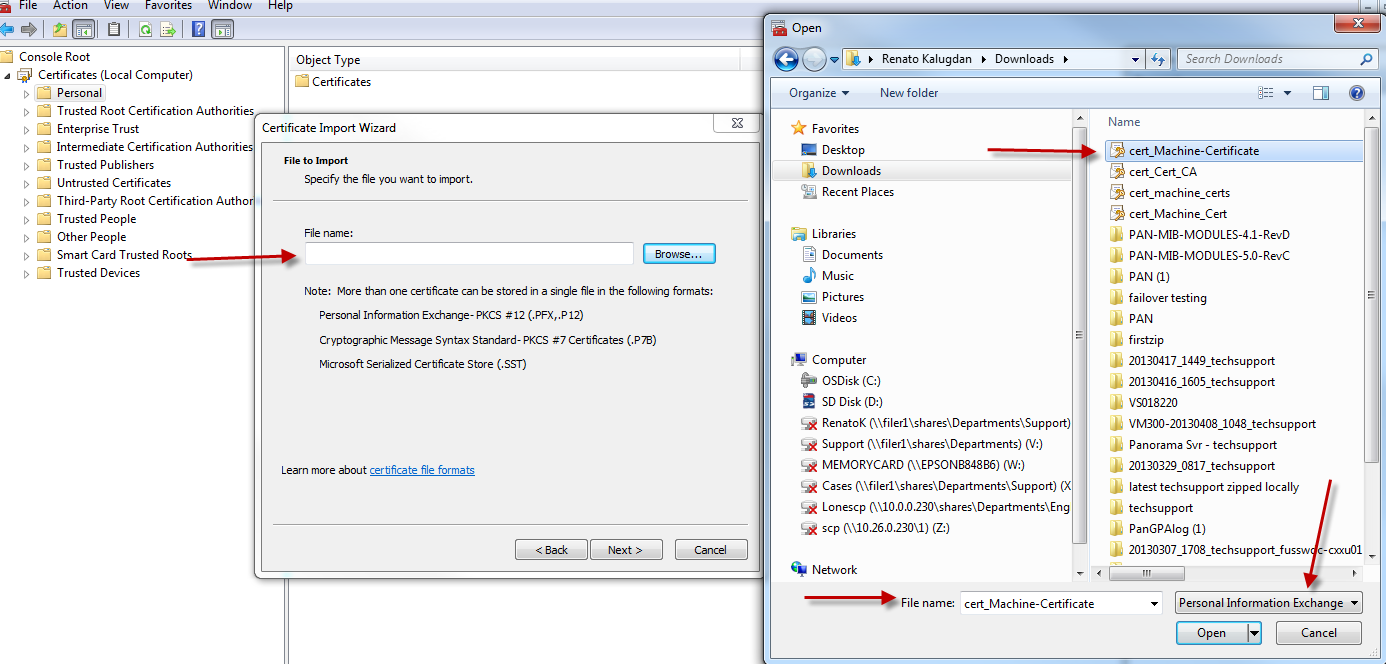
9.This will execute the Certificate Import Wizard. Follow the steps to complete the import. The certificate for this example was exported in pkcs12 file format. Make sure to confirm the correct cert is detected.
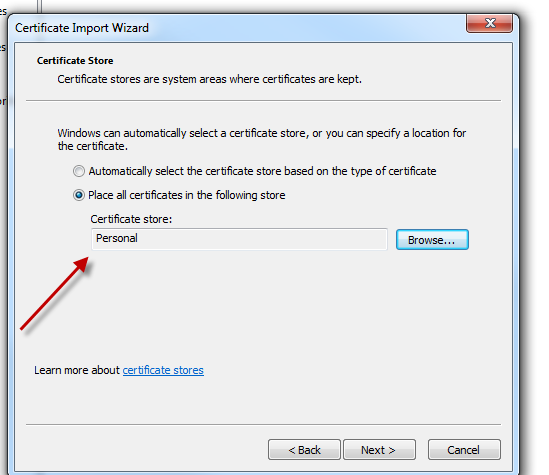
10.Install the certificate into the local computer personal certificate store and then confirm the installation.

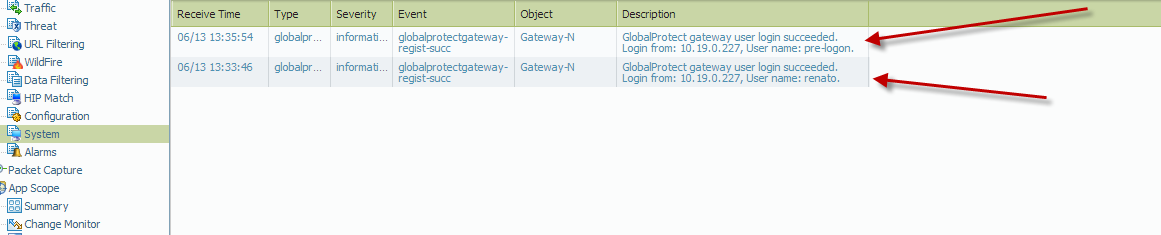
11.Here, syslog indicates the initial connection with the agent using the user credentials to successfully connect. Subsequently, log off the machine and verify that the machine is still able to make a successful connection to both GlobalProtect Portal and Gateway as a 'pre-logon' user with the machine certificate validated by the CA certificate.
owner: rkalugdan




