How to create GRE over IPSec using loopback interface
13973
Created On 07/16/23 16:05 PM - Last Modified 07/28/23 03:34 AM
Objective
To create GRE tunnel over IPSec tunnel using loopback interface.
Environment
- Palo Alto Firewalls
- PAN-OS PANOS- 9.1, 10.1, 10.2, 11.0 and 11.1
- IPSec Tunnel
- GRE Tunnel
Procedure
The configuration is explained using the following topology
- IPSec Tunnel is configured between FW-1 and FW-2. The tunnel interface is tunnel.1
- GRE Tunnel is configured over the existing IPSEC tunnel. The tunnel interface is tunnel.2
- Firewall-1 192.168.1.1 <--------ipsec (tunnel.1)--------------> Firewall2 192.168.1.2
- loopback 10.20.20.1 <-------- GRE (tunnel.2) -------------> loopback 10.20.20.1
- Configure IPSec between the two Firewalls using the external IP address. Refer to the knowledge article "How to configure IPSec tunnel "
- In the advanced option ensure "Add GRE Encapsulation" is enabled. Here tunnel.1 interface is used for the IPsec tunnel, configure remote side with opposite IP address.
GUI: Network > IPsec Tunnels > (tunnel name) > Click on "Show Advanced Options" and click on "Add GRE encapsulation"
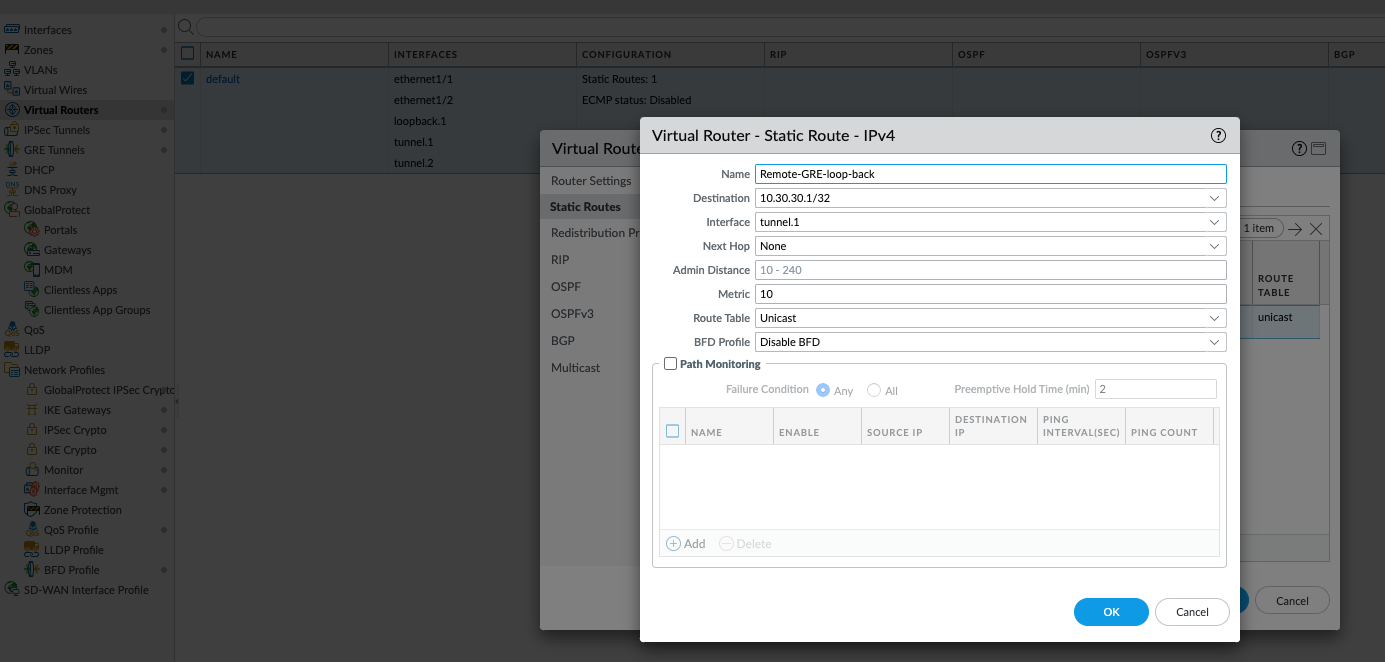
- Configure loopback interface and create a static route in both sites to reach that loopback IP address via IPsec tunnel ( in this example its tunnel.1 interface). In this example loopback IP address is 10.20.20.1/32 and the remote loopback IP address is 10.30.30.1/32. Static route is created via a tunnel.1 (ipsec) to reach 10.30.30.1/32
GUI: Network > Virtual Routers > (name of VR)> Static Routes > Add
- Create a tunnel interface for GRE and create GRE tunnel using loopback as local IP address and peer IP address and assign tunnel interface (in this example it's tunnel.2) on both sides, make sure to enable GRE keepalive which is being routed over IPsec tunnel.
GUI: Network > GRE Tunnels > Add
- Confirm the GRE tunnel is up by running the command "show interface tunnel <no>"
adminn@PA-FW1> show interface tunnel.2
--------------------------------------------------------------------------------
Name: tunnel.2, ID: 258
Operation mode: layer3
Virtual router default
Interface MTU 1500
Interface IP address: 172.16.2.1/30
Interface management profile: N/A
Service configured:
Zone: Internal, virtual system: vsys1
Adjust TCP MSS: no
Ignore IPv4 DF: no
Policing: no
Proxy protocol: no
--------------------------------------------------------------------------------
GRE tunnel name: GRE
tunnel interface state: Up
disabled: False
erspan: False
copy-tos: False
keep alive enabled: True
local-ip: 10.20.20.1
peer-ip: 10.30.30.1
- Add a route to reach remote networks over GRE tunnel
- Verify the connectivity by pinging the remote side. To confirm the session id can be checked ("show session all" and check one of the ping). This will show traffic is traversing over GRE tunnel over IPsec
adminn@PA-FW1> show session id 7632
Session 7632
c2s flow:
source: 10.10.10.1 [Internal]
dst: 10.100.100.1
proto: 1
sport: 26067 dport: 1
state: INIT type: FLOW
src user: unknown
dst user: unknown
s2c flow:
source: 10.100.100.1 [Internal]
dst: 10.10.10.1
proto: 1
sport: 1 dport: 26067
state: INIT type: FLOW
src user: unknown
dst user: unknown
.. <Output Omitted> ...
session traverses tunnel : True
session terminate tunnel : False
captive portal session : False
ingress interface : ethernet1/2
egress interface : tunnel.2
session QoS rule : N/A (class 4)
end-reason : aged-out
Additional Information
Note that create security policies accordingly between the zone if GRE, IPsec interface is configured in a different zone. In this example, IPsec, GRE belongs to the internal zone so the Interzone security policy will take care of traffic so no need to create a policy.