Need some help with Proxy IDs? Looks like a popular topic in our Live Community. Take a look at a couple of different scenarios, see what expertise our community brings to bear on the topic, and see what solutions we recommend.
See the discussion about Proxy IDs for this week's Discussion of the Week (DotW) here:
https://live.paloaltonetworks.com/t5/General-Topics/Proxy-IDs-help/m-p/3579#M2638
Community member Neo.The.One posted this topic about IPSec VPN Proxy IDs. He was setting up a VPN with a Check Point firewall, and needed to know what Proxy ID settings are required to get this VPN tunnel working properly.
Neo.The.One had 2 scenarios:
Case 1
My internal networks for VPN (Palo Alto Networks firewall): 173.16.10.0/24, 10.31.0.0/16, 10.40.40.0/24
Networks behind the peer (Check Point firewall): Unknown
Case 2
My internal networks for VPN (Palo Alto Networks firewall): 172.16.10.0/24 , 10.31.0.0/16, 10.40.40.0/24
Networks behind the peer (Check Point firewall): Exactly the same, such as 172.16.10.0/24 , 10.31.0.0/16, 10.40.40.0/24
Both Live Community members HULK and Satish responded with great answers to help Neo.The.One.
Hulk was the first to respond. He explained that Proxy IDs are required to define the SPI keys in the IPSec VPN. SPI is a key pair, used for encapsulation and decapsulation of an ESP packet.
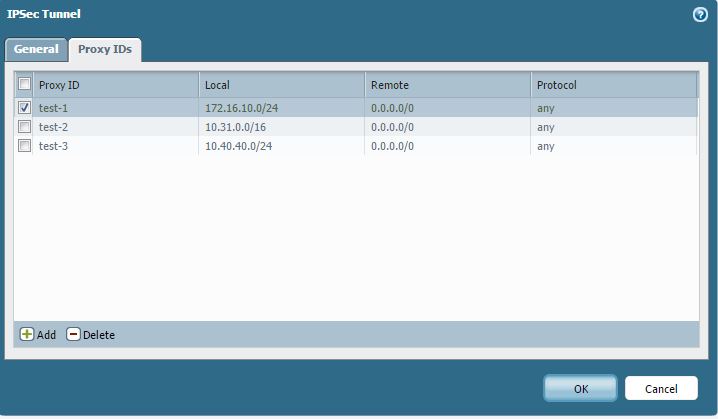
The first case Neo.The.One asked about can be resolved if the Proxy IDs are configured properly. Hulk provided a great screenshot of the Proxy ID config.
Network > IPSec Tunnels > Select a Tunnel > Proxy IDs tab
The second case can be resolved if you address the overlapping subnet issue.
Please see the following diagram showing overlapping subnets with an IPSec VPN tunnel:
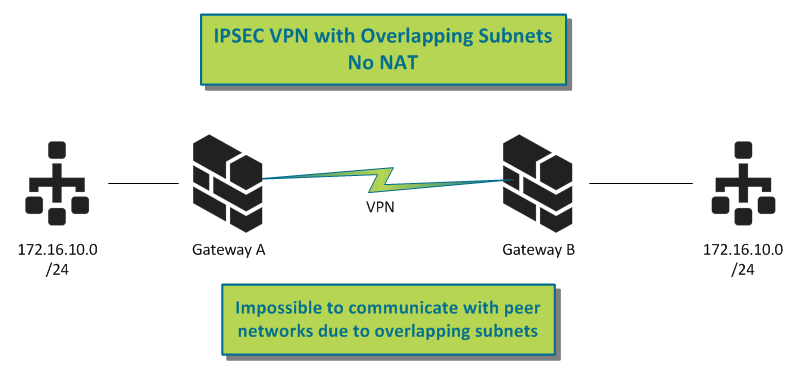
There's no way for the traffic to route over the VPN tunnel, as the same network exists on both sides of the tunnel.
The only way to resolve this issue is for both peer gateways to create NATs (Network Address Translation) to translate a new, unique network subnet to the internal network, or one side has to change the subnet IP. Please see the diagram:
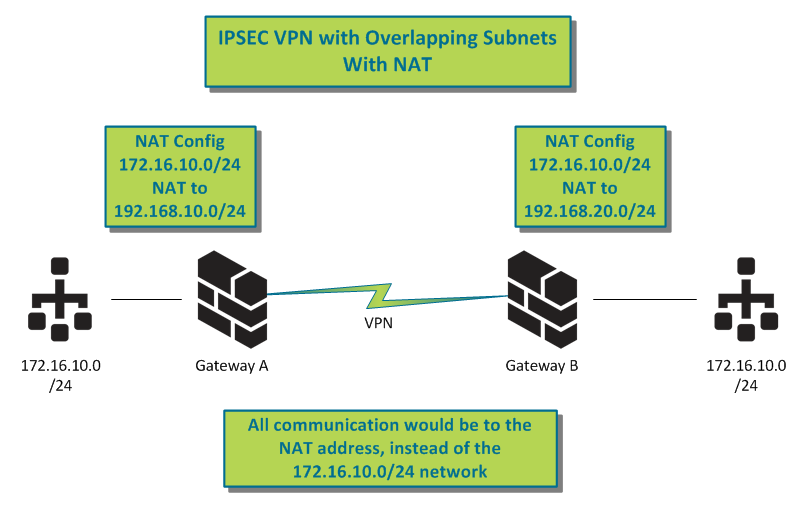
This way, all traffic on either side would be destined to the new NAT address instead of the other (same) network.
In this solution, both gateways would have to perform NAT for this to work properly. But this way, there would be no confusion about which network is on which side.
Neo.The.One had 2 follow-up questions to which Satish responded:
Question: Does he have to enter 0.0.0.0/0 or leave it blank?
Answer: An address is required.
Question: Does he have to add the IP addresses of external interfaces of Palo Alto Networks and peer firewalls in the Proxy IDs list?
Answer: Yes, you have to add the IP addresses of the external interfaces or NAT addresses to the Proxy ID list to get this to work properly.
Satish also provided this link to help with the VPN Config: How to Configure IPSec VPN
I hope that this helps you understand Proxy IDs and what to do if you have an overlapping subnet on both sides of the VPN tunnel.
To view the discussion, please use this link:
https://live.paloaltonetworks.com/t5/General-Topics/Proxy-IDs-help/m-p/3579#M2638
As always, we welcome all feedback and suggestions in the comments below!
Stay secure,
Joe Delio