To implement GlobalProtect, configure:
- GlobalProtect client downloaded and activated on the Palo Alto Networks firewall
- Portal Configuration
- Gateway Configuration
- Routing between the trust zones and GlobalProtect clients (and in some cases, between the GlobalProtect clients and the untrusted zones)
- Security and NAT policies permitting traffic between the GlobalProtect clients and Trust
- Optional: NAT Policy for GlobalProtect clients to go out to the internet (if split tunneling is not enabled)
- For iOS or Android devices to connect, GlobalProtect app can be used.
Certificate Configuration: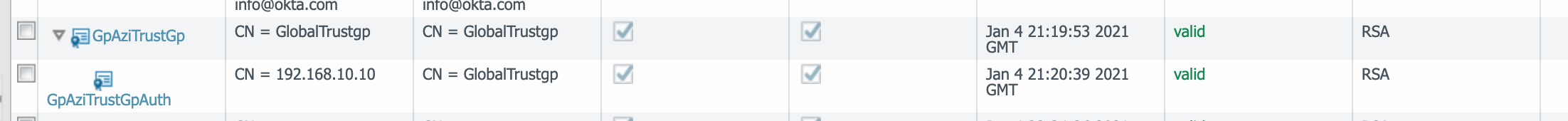
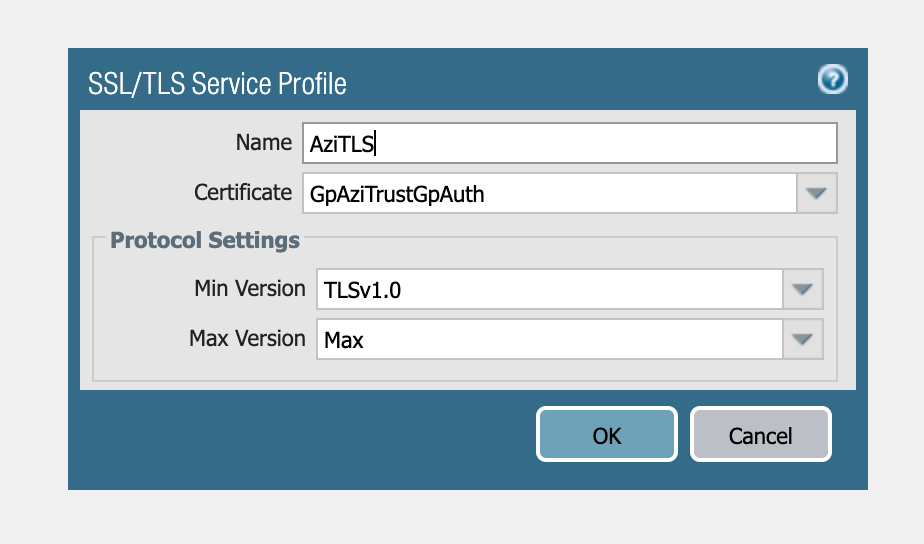
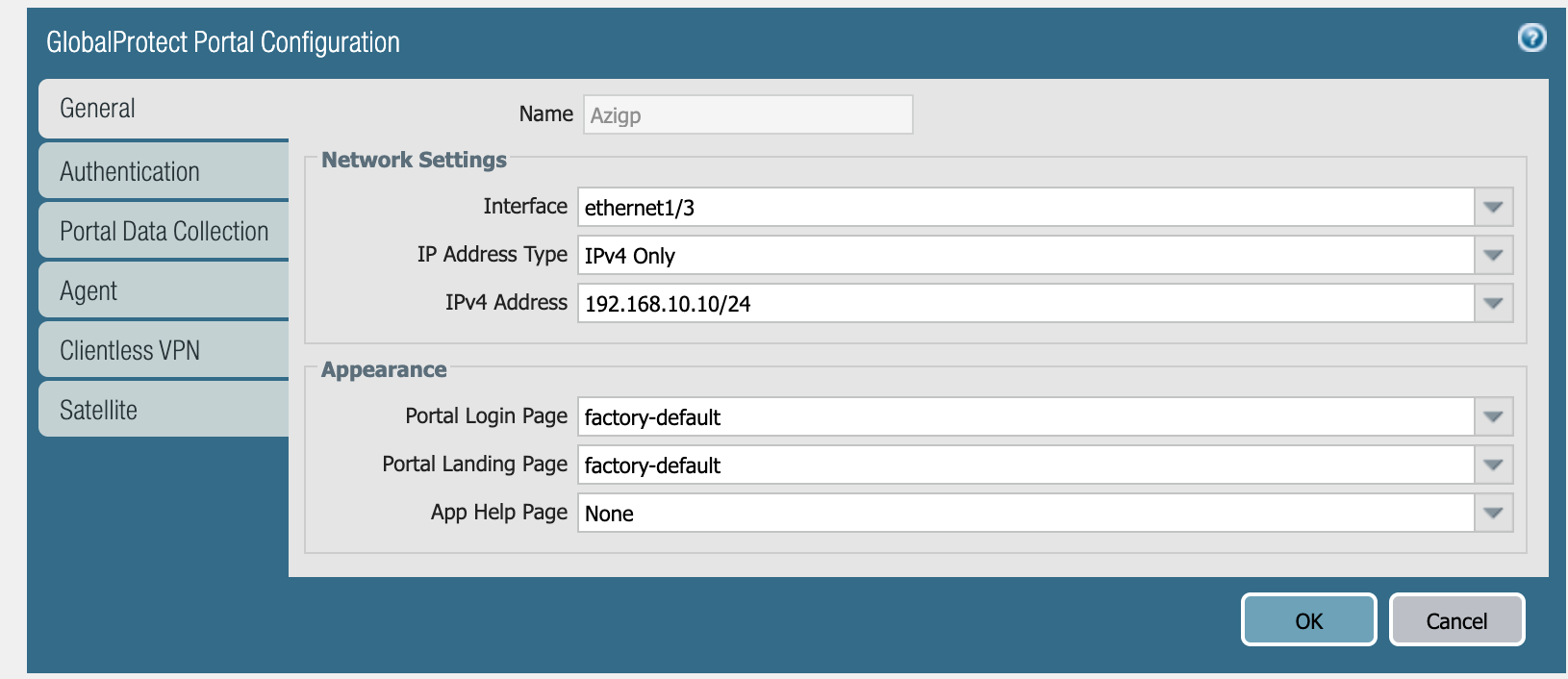
Portal Configuration
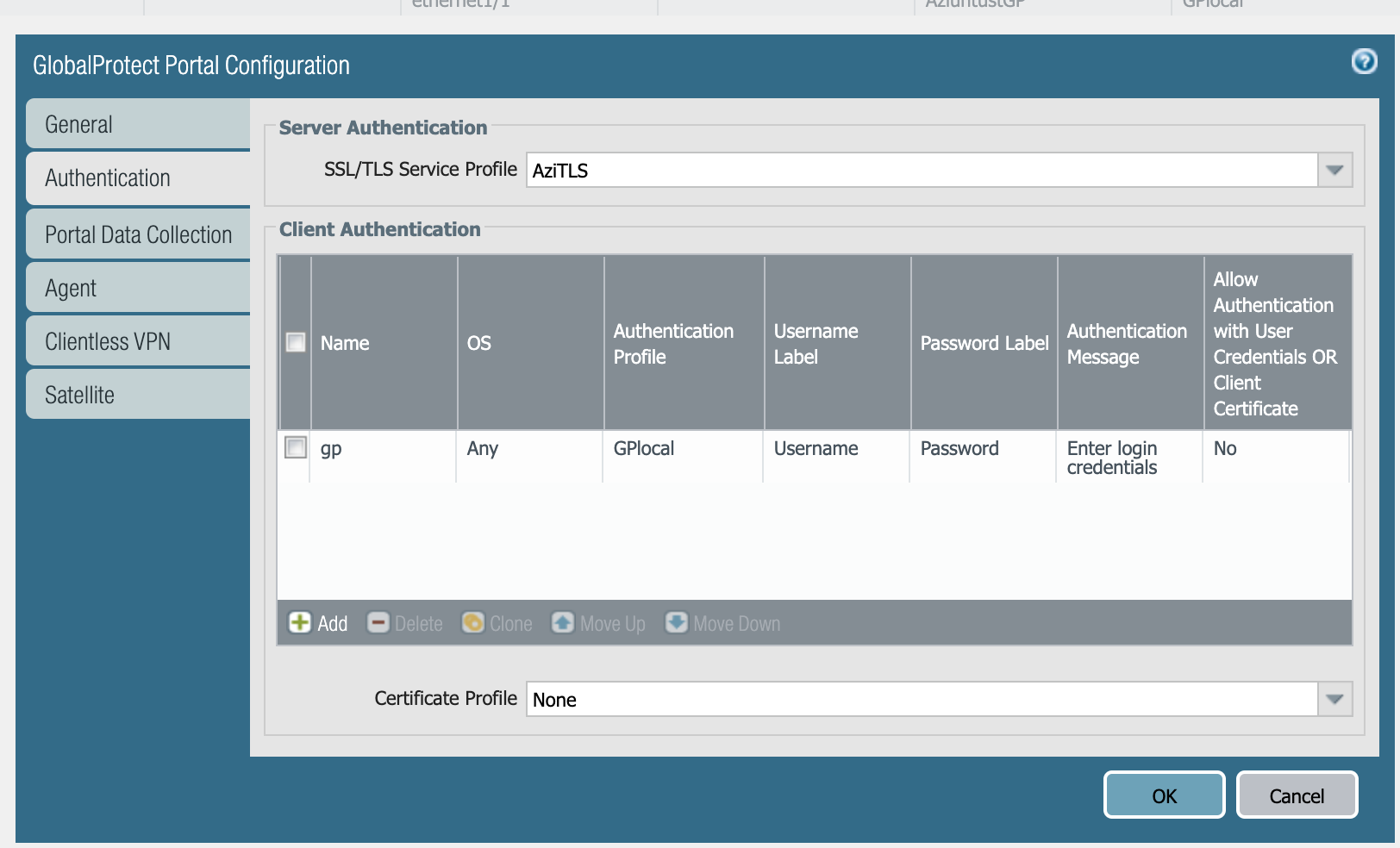
It is recommended to first test without a Certificate Profile, which allows for simpler troubleshooting, if the initial configuration does not work as intended. First successfully configure and test basic authentication, then add the Certificate Profile for certificate authentication.
The portal address is the address where outside GlobalProtect clients connect. In most cases, this is the outside interface's IP address. The gateway address is usually the same outside IP address.
GlobalProtect Connect Methods:
- On-demand: Requires manually connecting when access to the VPN is required.
- User-logon: VPN is established as soon as the user logs into the machine. When SSO is enabled, user credentials are automatically pulled from the Windows logon information and used to authenticate the GlobalProtect client user.
- Pre-logon: VPN is established before the user logs into the machine. Machine certificate is required for this type of connection.
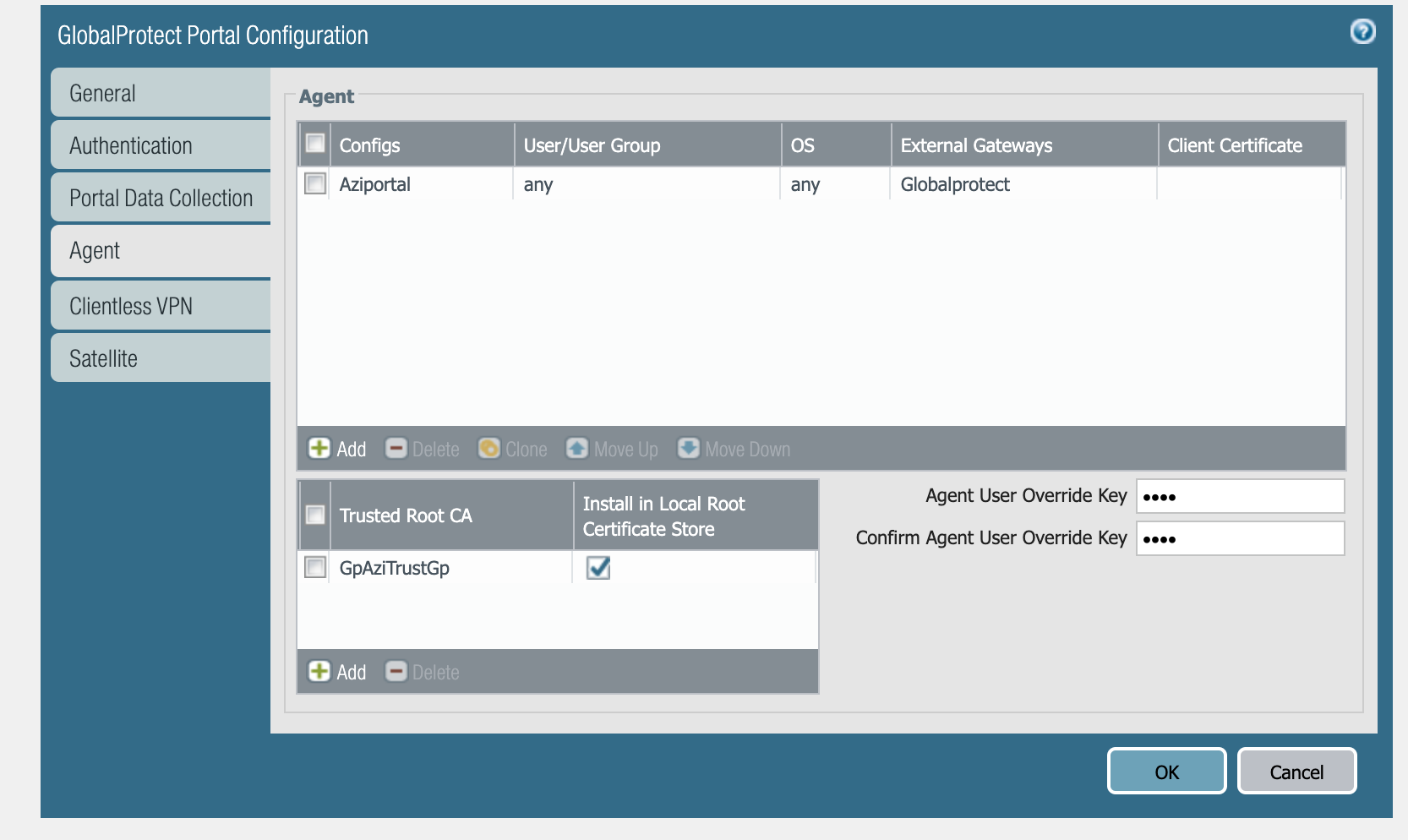
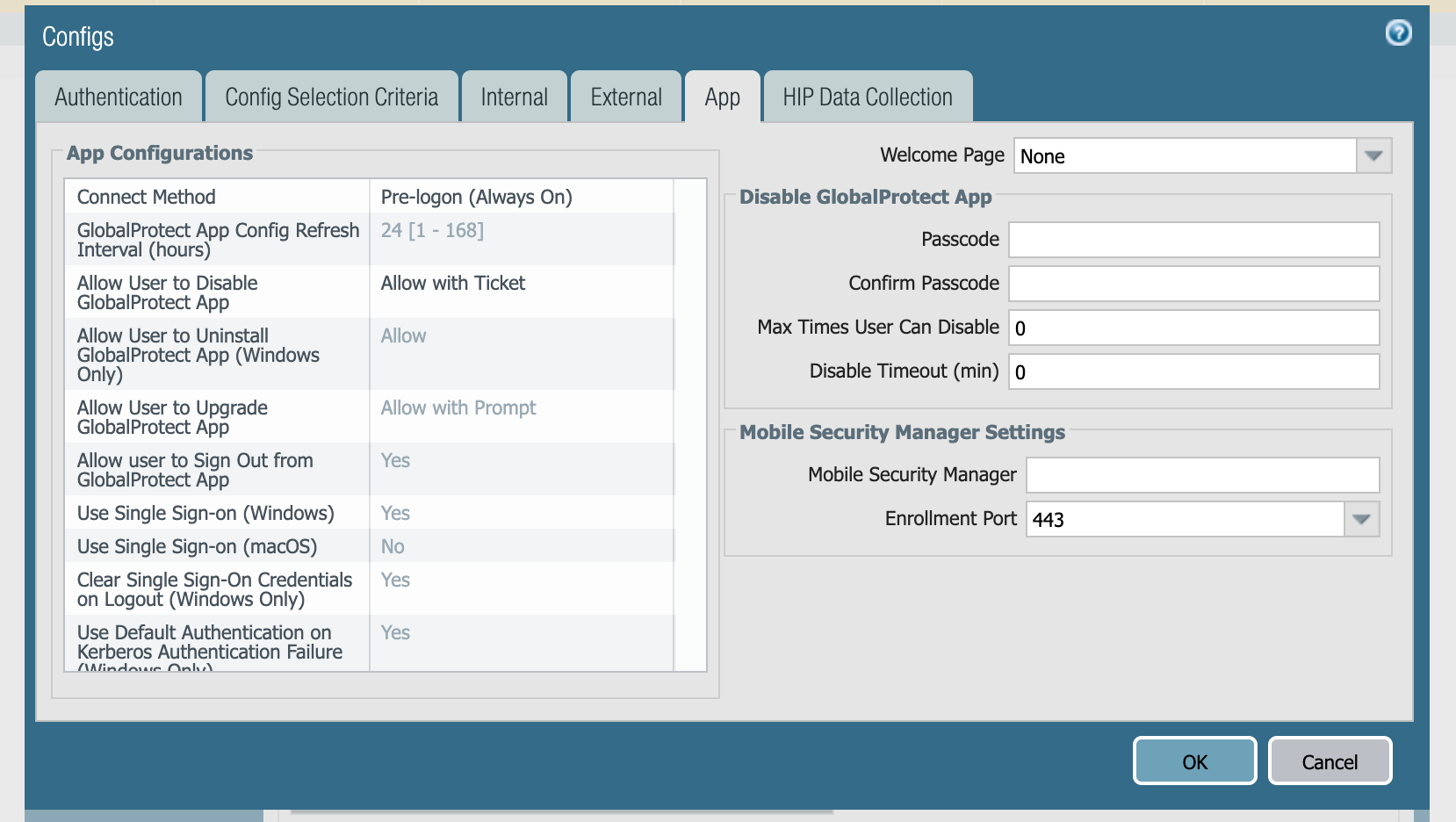
The Agent tab contains important information regarding what users can or cannot do with the GlobalProtect Agent. Enabling Agent User Override-with-comment allows users to disable the agent after entering a comment or reason. The comment appears in the system logs of the firewall when this user logs in next.
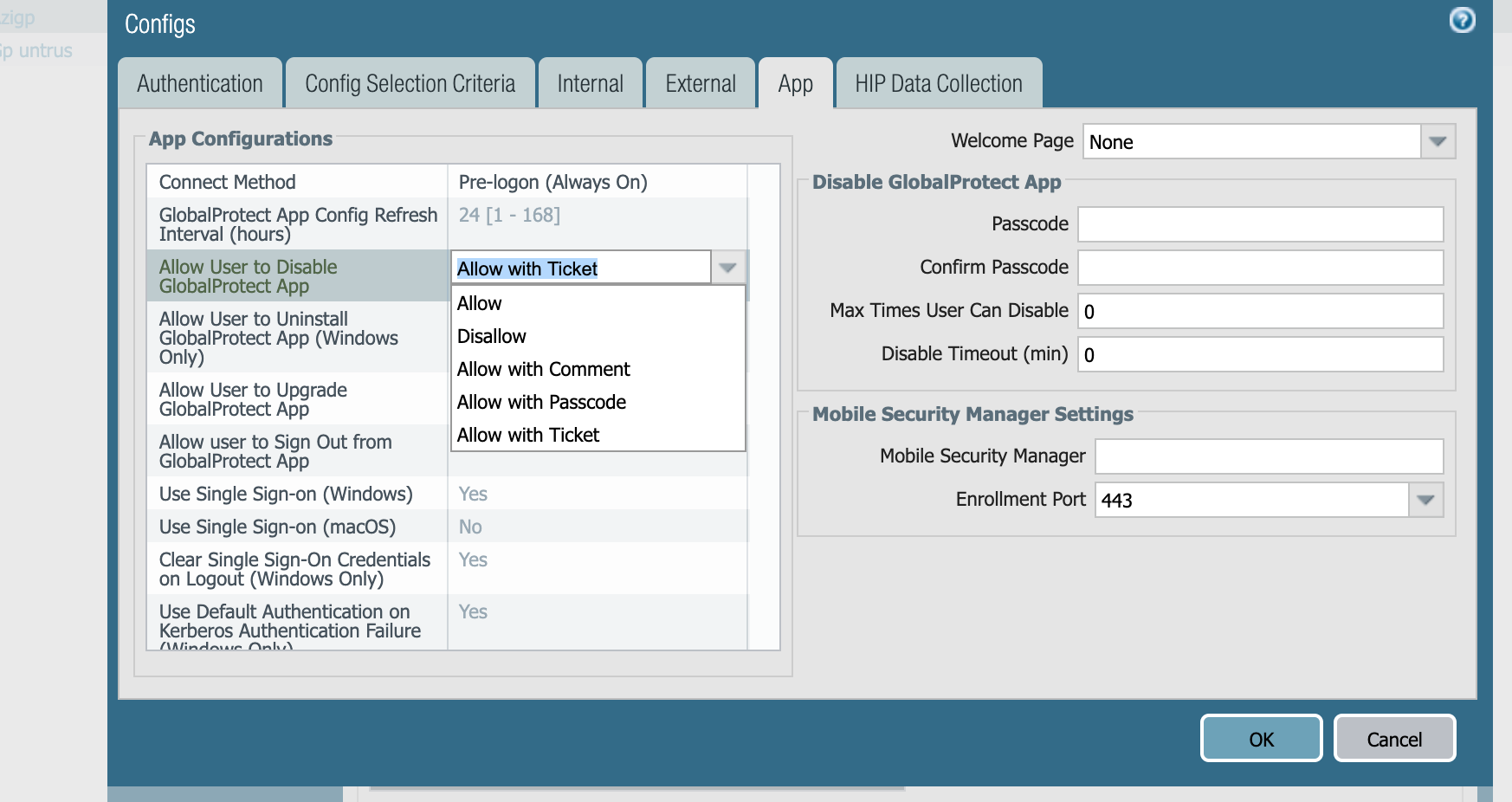
Selecting the "disabled" option for Agent User Override prevents users from disabling the GlobalProtect agent:
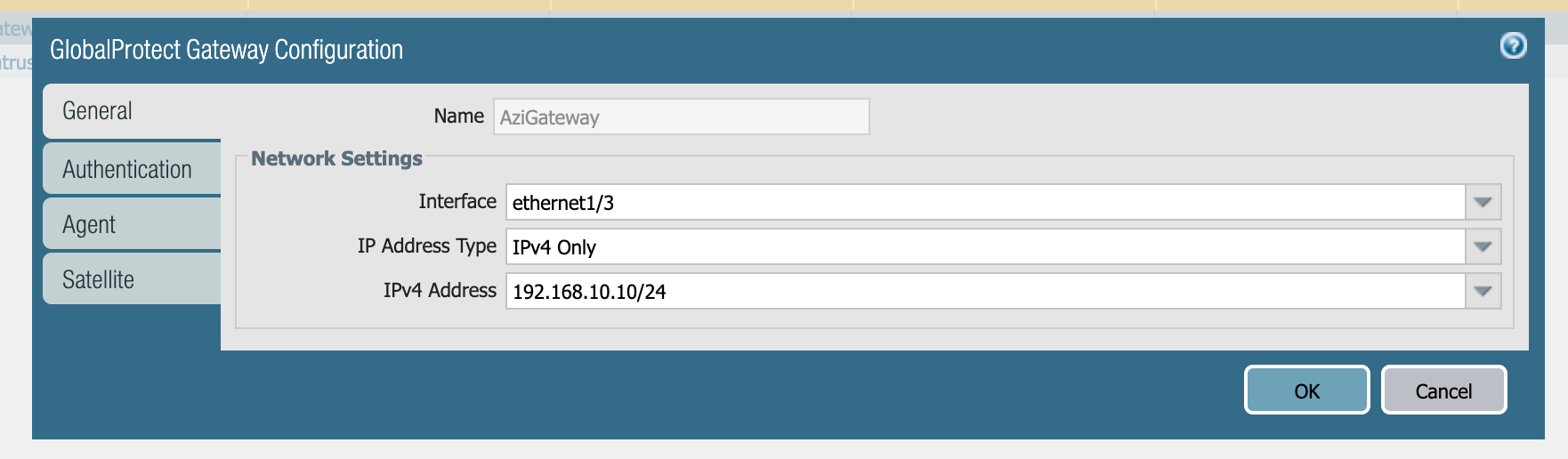
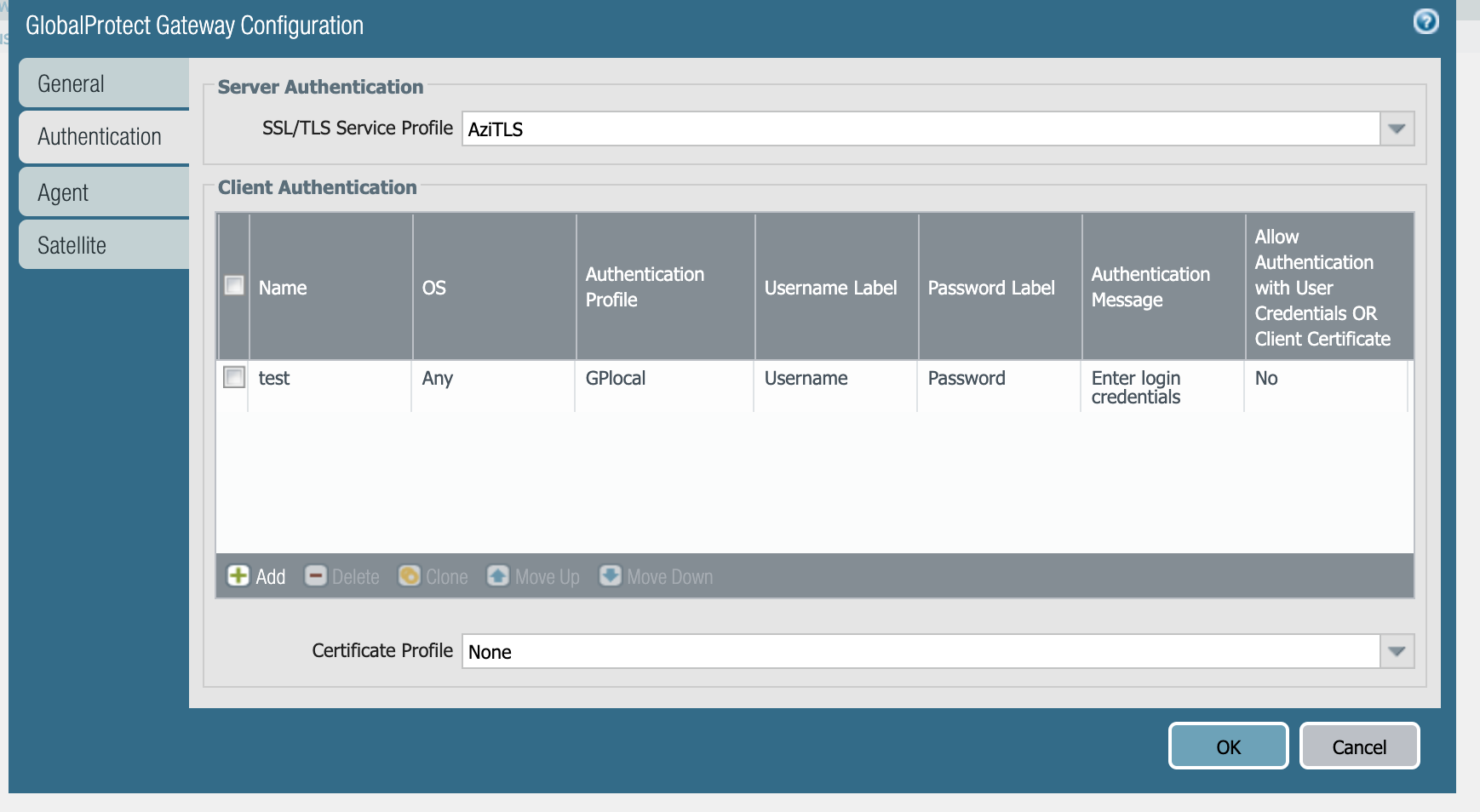
Gateway Configuration
For the initial testing, Palo Alto Networks recommends configuring basic authentication. When everything has been tested, adding authentication via client certificates, if necessary, can be added to the configuration.
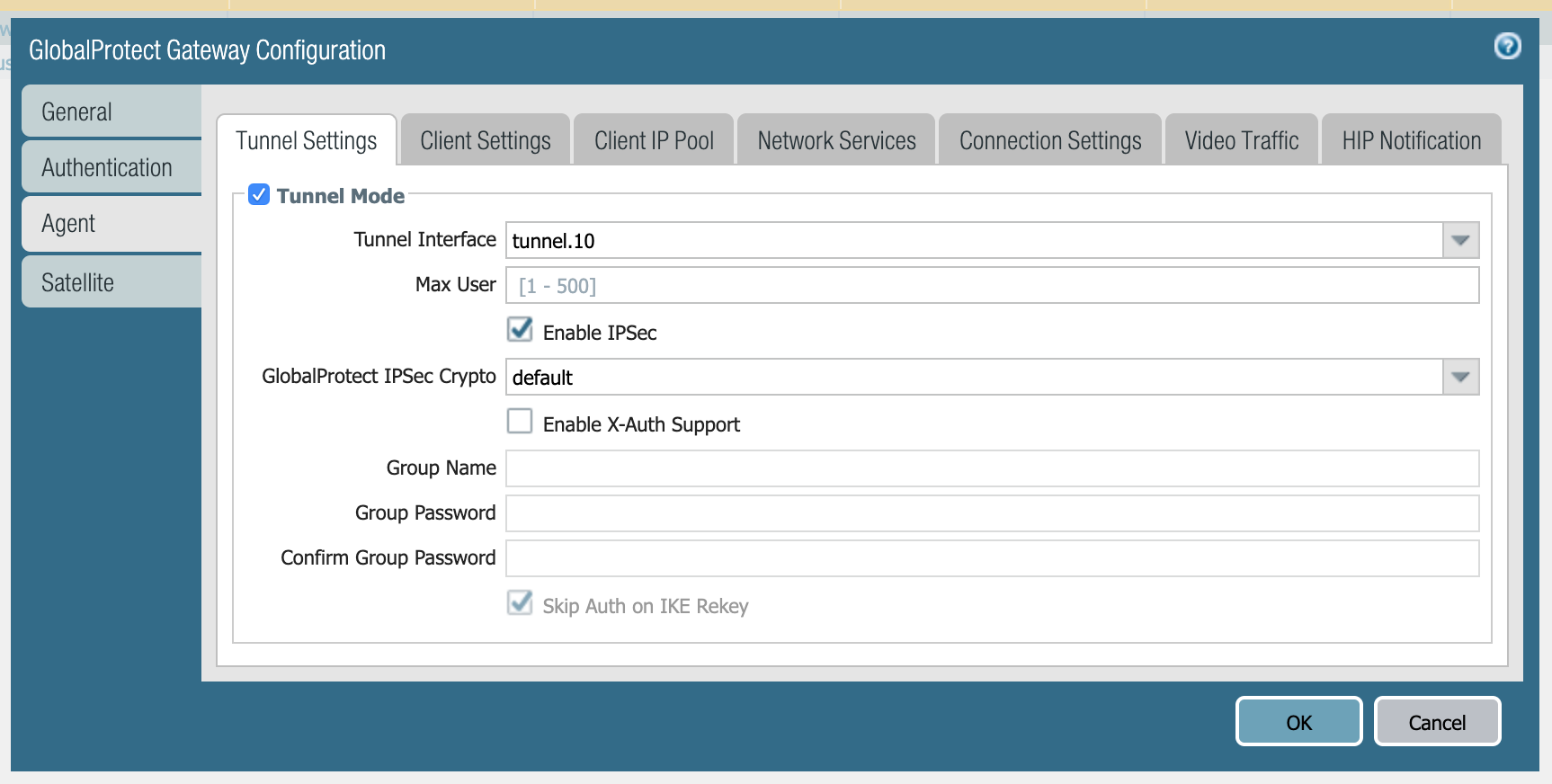
To authenticate devices with a third-party VPN application, check "Enable X-Auth Support" in the gateway's Client Configuration. Group Name and password must be configured for this setting.
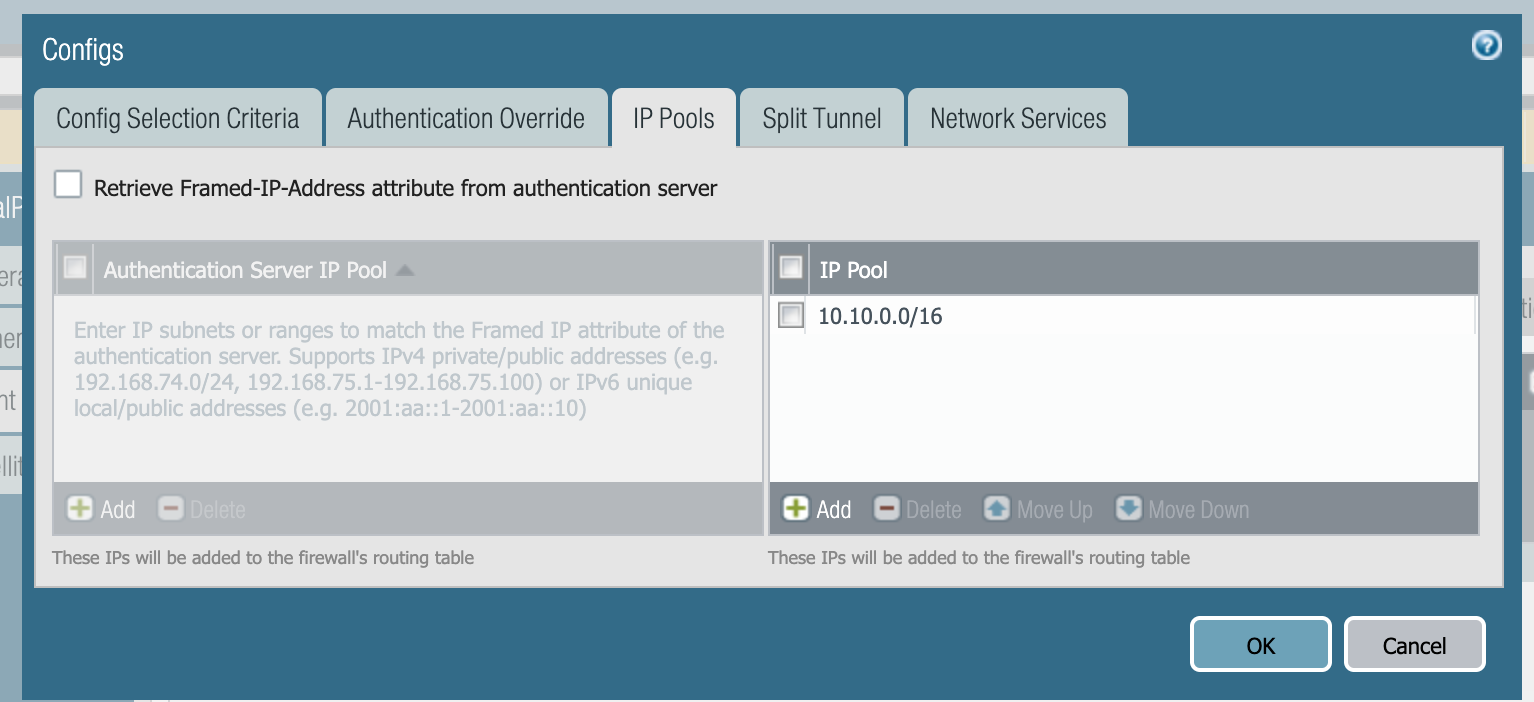
In most cases, for firewalls with static public IP addresses, set the inheritance source to none.
The IP pool settings information is important, because it is the pool of IP addresses that the firewall assigns to connecting GP clients. Even if Global Connect clients need to be considered as part of the local network, to facilitate routing, Palo Alto Networks does not recommend using an IP pool in the same subnet as the LAN address pool. Internal servers automatically know to send packets back to the gateway if the source is another subnet. If the GP clients were issued IP addresses from the same subnet as the LAN, then the internal LAN resources would never direct their traffic intended for the GP clients to the Palo Alto Networks Firewall (default GW).
Access Routes:
Access routes are the subnets to which GlobalProtect clients are expected to connect. In most cases this is the LAN networks. To force all traffic to go through the firewall, even traffic intended for the Internet, the network that needs to be configured is "0.0.0.0/0," which means all traffic.
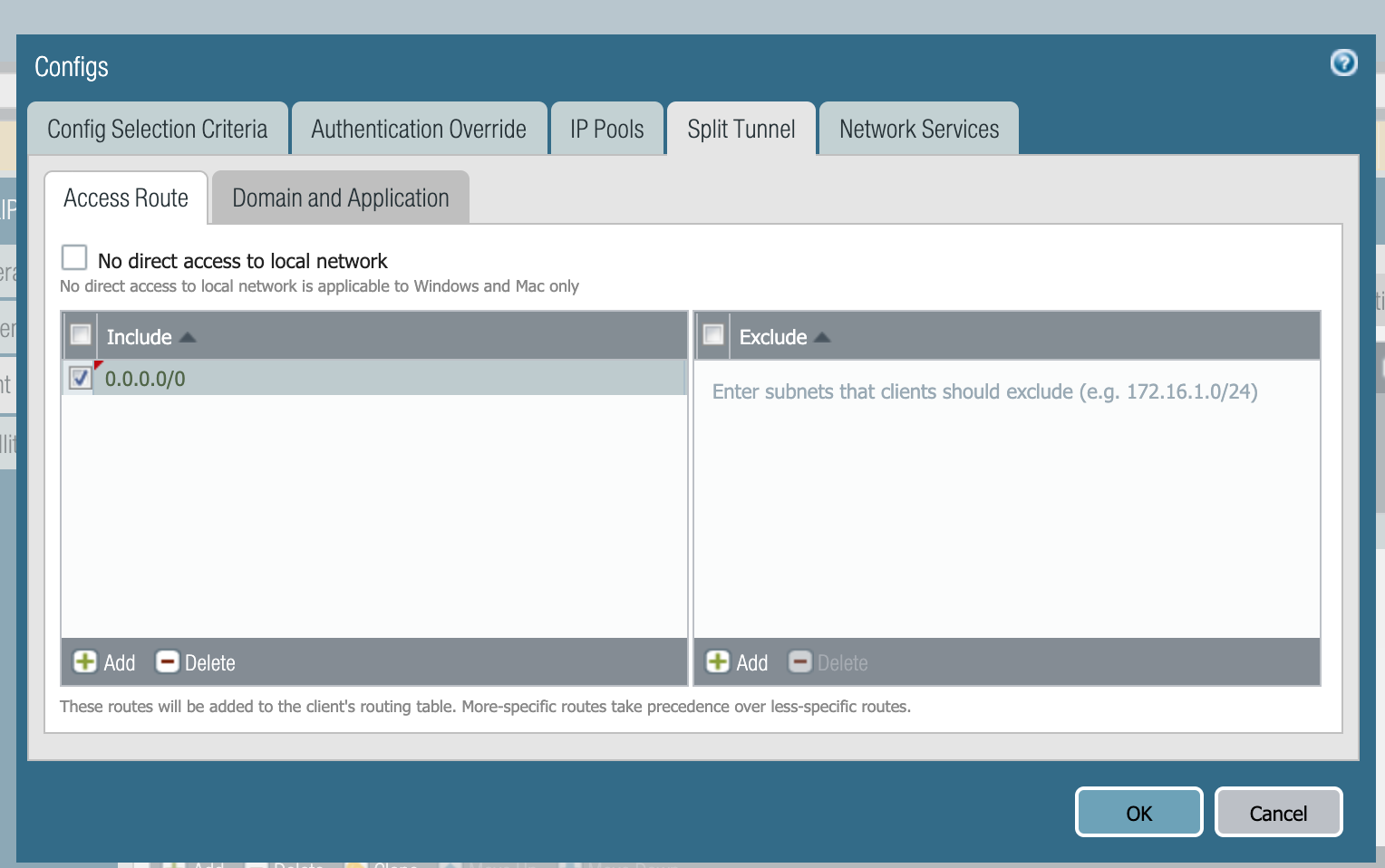
If 0.0.0.0/0 is configured, the security rule can then control what internal LAN resources the GlobalProtect clients can access. If a security policy does not permit traffic from the GlobalProtect clients zone to the Untrust the untrusted zone, then from the GlobalProtect clients connected to the Palo Alto Networks firewall through the SSL VPN, then those clients can access only local resources and are not be allowed on the internet:
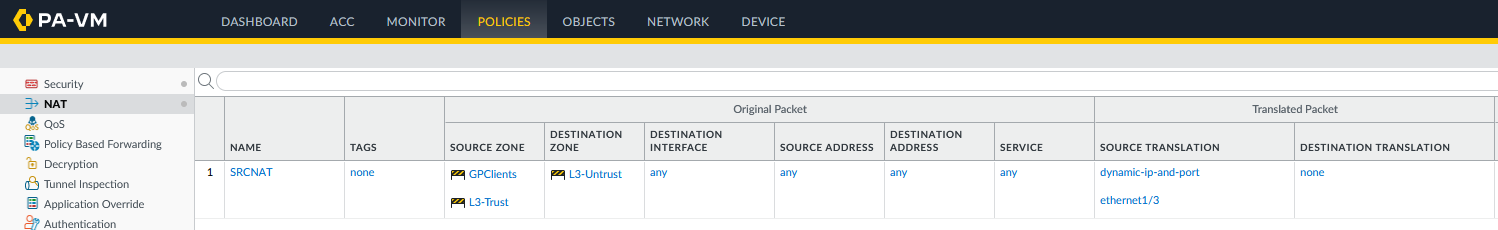
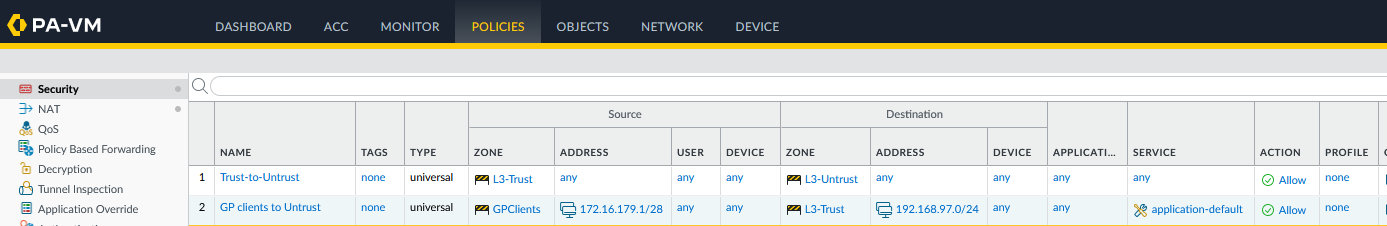
The GlobalProtect clients zones and tunnels must be included in the same virtual router as the other interfaces.