Anti-Spyware or Vulnerability Protection Exceptions
For example: Add an Anti-Spyware Exception for threat ID #30003 to an existing profile named "corp-vp"
- Go to Objects > Security Profiles > 'Anti-Spyware' or 'Vulnerability Protection'
- Select the existing profile
- Click the "Exceptions" tab.
- First, check the "Show all signatures" checkbox at the lower left-hand part of the profile window.
- In the search field, enter a string as "( ex. 'microsoft' )" or simply enter the threat ID number itself (ex. 30003). Press enter or click the green arrow to initiate the search.
Note: If the signature being searched for was just applied in the latest dynamic update operation and it is not being returned in the search results, log out of the Web UI and then log back in to clear the GUI cache. - The results will return "Microsoft Windows DCOM RPC Interface Buffer Overrun Vulnerability" (which is threat ID #30003).
Note: Threat IDs can be easily determined from the threat logs. - To enable this exception, check the 'Enable' box
- Change the default 'Action' value. To allow the traffic, select Allow, or to drop the traffic select Reset Both.
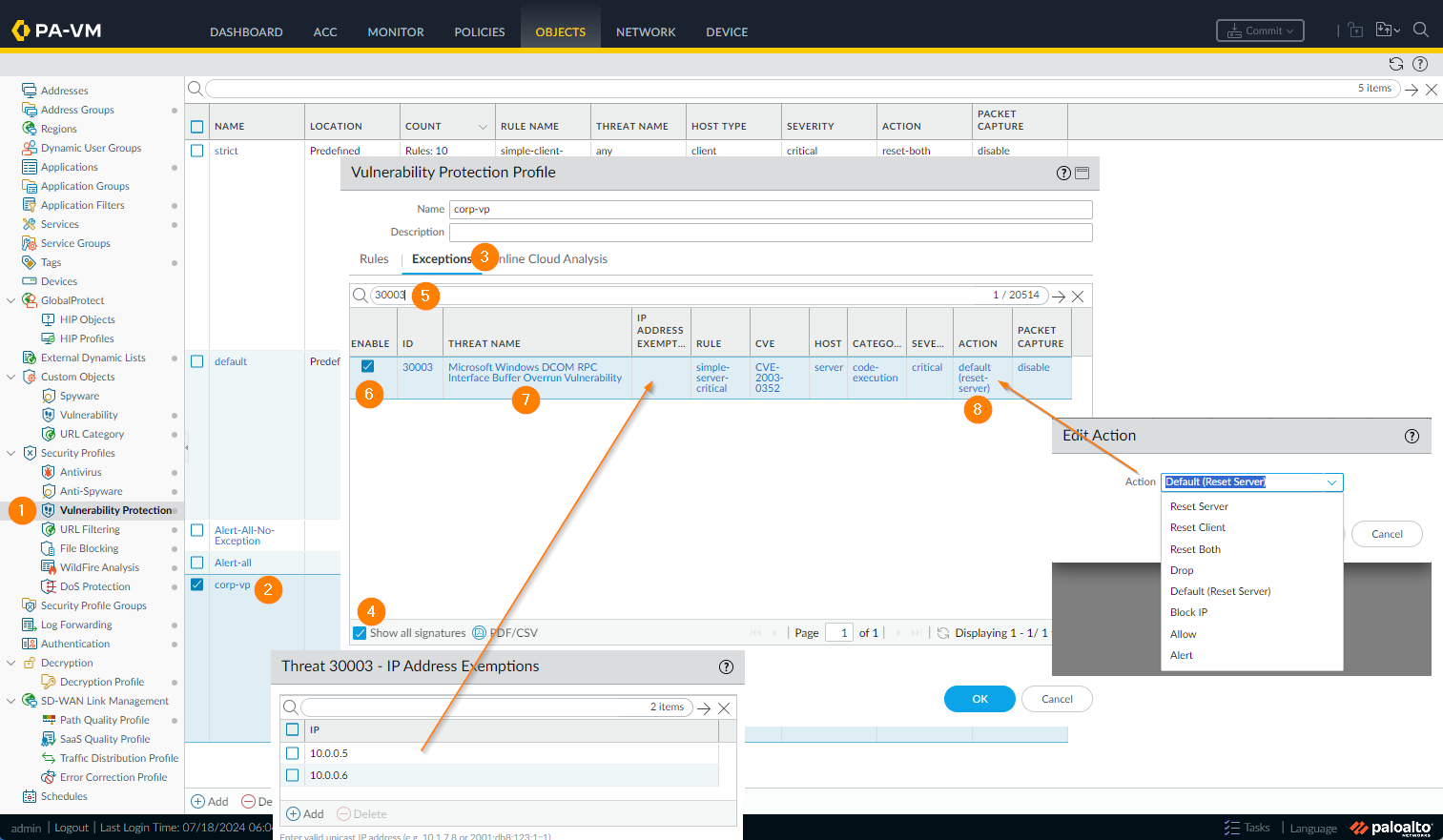
Threat Action detail - change default action.
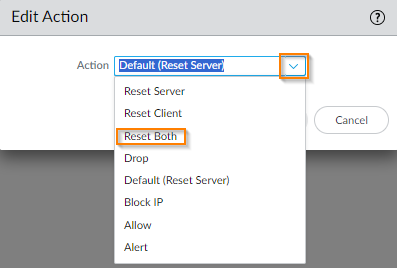
- Use the IP Address Exceptions column to add IP address filters to a threat exception. If IP addresses are added to a threat exception, the threat exception action for that signature will only be taken over the rule's action if the signature is triggered by a session having either the source or destination IP matching an IP in the exception. You can add up to 100 IP addresses per signature. With this option, one does not need to create a new policy rule and new vulnerability profile to create an exception for a specific IP address. To exclude certain IP addresses and not all traffic, click on the blank under "IP Address Exemptions" and click Add at the bottom. One can add up to 100 IP addresses to the list.
- For example, if you add an IP address to the "IP Address Exemptions" column with an action of "Reset-Both", all traffic matching this rule will be dropped except for the IP addresses listed in this column.
 IP Address Exemption detail.
IP Address Exemption detail.- Ensure that Anti-Spyware and/or Vulnerability Protection profiles are applied to the appropriate security policies.
- Commit changes to enable the Exception.
- Exceptions will apply to any new sessions installed after the Commit succeeds. If the exception is used to allow traffic that was previously blocked, make sure there are no existing DISCARD sessions in the session table. For example, in cases like DNS or DHCP traffic, the 6-tuple is rechecked with each new packet, which could perpetuate a DISCARD session and override the newly added exception.
- For detailed instructions on clearing existing sessions, please refer to How to View/Clear Sessions and/or How to View/Clear Sessions from the Session Monitor.
Antivirus Exceptions
For example, to add an antivirus exception for threat ID 398981154 to an existing profile named "Corp-AV":
(Note: Be aware that if you exclude a Virus from being checked against, this is all or nothing; you cannot exclude just an IP from this protection. It would be all that is allowed on that rule/antivirus policy.)
- Go to GUI: Objects > Security Profiles > Antivirus.
- In the existing profile, click on the Signature Exceptions tab.
- Enter the ID value (for this example, 398981154 ) into the Threat ID field at the bottom of the page, and click Add and then OK.
Note: The threat ID can be determined from the threat logs. - For this example, an exception for "Exploit/Win32.pidief.irr" is created.
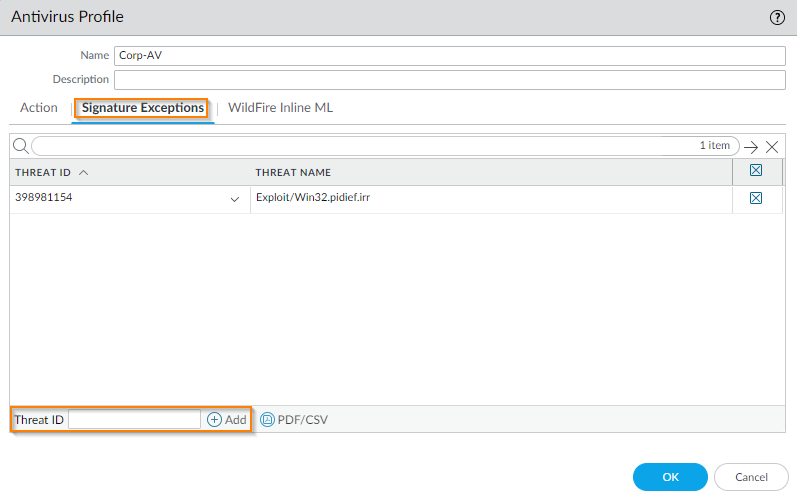 Antivirus - Virus Exception window detail.
Antivirus - Virus Exception window detail.
- Make sure that Antivirus profiles are applied to the appropriate security policies.
- There is no option to exclude just certain IP addresses with an Antivirus Exception.
- Commit the changes.









