How to Configure Captive Portal
161413
Created On 07/18/22 22:57 PM - Last Modified 12/02/22 17:58 PM
Objective
To Configure Captive Portal (Authentication Portal ) Using Redirect Mode And Local Authentication
Environment
- Palo Alto Firewalls.
- PAN-OS 9.1 and above.
- Captive Portal (Authentication Portal).
Procedure
Configuring Captive Portal is documented here . This article provides an example using the following Network Diagram.
- Enable user identification on the internal zone.
Go to Network > Zones > Select the zone > Enable User Identification.
- Configure an interface management profile with response pages enable and associate it to the internal interface.
Go to Network > Interface > Select the interface > Advanced Tab > Create Management Interface Profile.
- Create the users and user group.
Go to Device > Users > Add Users/User Group.
- Configure the certificates.
Go to Device > Certificates > Generate
- Create SSL Profile and attach the certificate.
Go to Device > SSL/TLS Service Profile > Add
- Configure an authentication profile and add the created group.
Go to Device > Authentication Profile > Add
- Enable captive portal (Authentication Portal)
Go to Device > User Identification > Captive Portal
- Create an authentication policy.
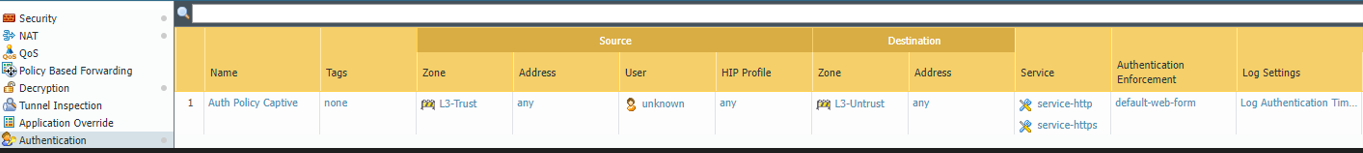
- Configure decryption policies.
Go to Policies > Decryption > Add
- Create a security policy to allow DNS and Captive portal traffic.
Go to Policies > Security > Add
- Import the certificates into the trusted root CA from the clients.
Go to Device > Certificates > Select the certificate > Export Certificate
Once the certificates were added to the trusted root CA on the clients, open a web browser. Trying to connect to web sites will display the captive portal box.
Additional Information
Configuring Captive Portal in 9.1
Configuring Captive Portal in 10.1
Configuring Captive Portal in 10.2
Configuring Captive Portal in 11.0