Traffic using the wrong route in HA Active/Active when Primary is session Owner and Secondary is session Setup
9027
Created On 02/24/21 23:21 PM - Last Modified 10/23/21 01:31 AM
Symptom
- Traffic is routed to the wrong zone and wrong interface whenever session setup is the Active-Secondary Firewall and session owner is Active-Primary.
- This causes packet drop and inability to access resources
Environment
- Platform: PA-3250
- Pan OS: 9.1.3-hx
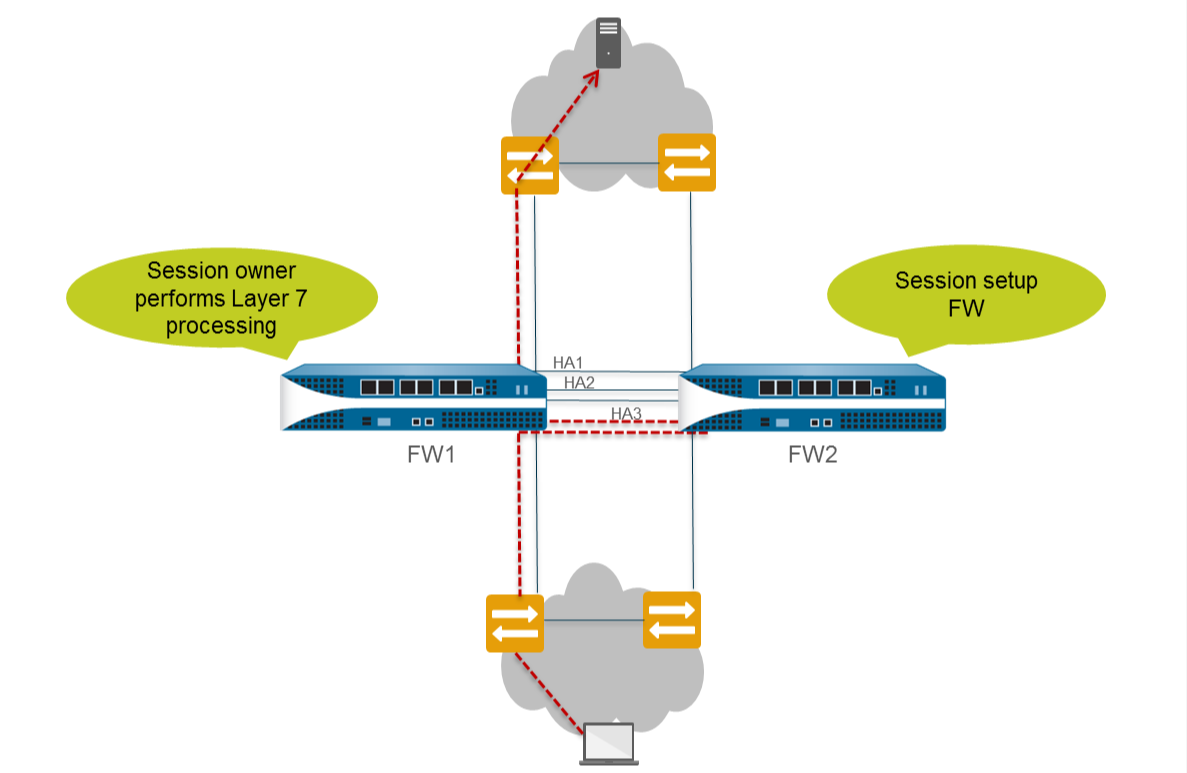
- High-Availability: Active/Active
- Session Owner: First Packet (Active-Primary)
- Session Setup: IP-Modulo (Active-Secondary)
- Active-Primary:
Source zone: DMZ
Destination Zone: GP
Source Subnet: 10.0.0.0/24
Destination Subnet: 10.0.1.0/24
Default Route: 0.0.0.0/0 Via Ethernet1/3(Untrust Zone)
Static Route: 10.0.1.0/24 Via Tunnel.10
Global Protect IP Pool: 10.0.1.0/24
Destination Zone: GP
Source Subnet: 10.0.0.0/24
Destination Subnet: 10.0.1.0/24
Default Route: 0.0.0.0/0 Via Ethernet1/3(Untrust Zone)
Static Route: 10.0.1.0/24 Via Tunnel.10
Global Protect IP Pool: 10.0.1.0/24
- Active-Secondary:
Source zone: DMZ
Destination Zone: GP
Source Subnet: 10.0.0.0/24
Destination Subnet: 10.0.2.0/24
Default Route: 0.0.0.0/0 Via Ethernet1/3 (Untrust Zone)
Static Route: 10.0.2.0/24 Via Tunnel.10
Global Protect IP Pool: 10.0.2.0/24
Destination Zone: GP
Source Subnet: 10.0.0.0/24
Destination Subnet: 10.0.2.0/24
Default Route: 0.0.0.0/0 Via Ethernet1/3 (Untrust Zone)
Static Route: 10.0.2.0/24 Via Tunnel.10
Global Protect IP Pool: 10.0.2.0/24
Cause
Both HA firewalls have different routing configuration
There is no route to 10.0.1.0/24 in Active-Secondary so Active-secondary will use it's default route which points to Untrust zone
NOTE: This is only necessary when both HA firewall in Active/Active deployment have different routing configuration. If both firewalls have the same routing configure, this will not be necessary.
Resolution
- Session setup firewall is responsible for route lookup and uses its route table to determine the route
- Configure Static route to 10.0.1.0/24 in the Active-Secondary firewall
Static Route: 10.0.1.0/24 Via Tunnel.10
Additional Information
Session setup: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/high-availability/ha-concepts/session-setup.html
Session Owner: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/high-availability/ha-concepts/session-owner.html