Firewall Decrypting Traffic Associated With A No-Decrypt Policy
14977
Created On 04/22/20 03:15 AM - Last Modified 11/13/20 17:24 PM
Symptom
- Traffic logs showing SSL decryption for traffic matching URL category in no-decrypt policy:
- Configured Decryption Policies (GUI: Policies > Decryption)
- Configured URL Category (GUI: Objects > Custom Objects > URL Category)
- The web browser is likely to report a certificate error. Chrome, for example, displays "Not Secure" next to the search bar
Environment
- PAN-OS 8.1 and above.
- Palo Alto Firewall.
- SSL forward proxy configured.
Cause
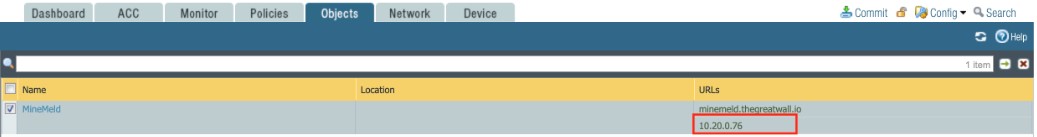
- The address object contains an FQDN (in this example: minemeld.thegreatwall.io)
- Neither the SNI (if present) nor the server's certificate CN presented in the SSL handshake references the FQDN in the Custom URL Object.
Resolution
- Include the server name or certificate CN (if SNI is not included in the handshake) to the Custom URL Object. In this example, 10.20.0.76 has been added to the "MineMeld" Object.
(GUI : Objects > Custom Objects > URL Category > (name of configured object) > Add > enter the IP address in under URL or sites column)
- Commit the changes. The decryption policy should work fine.
Additional Information
- The same principle can be applied for traffic that should be decrypted but isn't being decrypted.
- In certain cases where the SNI is not included in the SSL handshake, it may be necessary to take a packet capture without decryption in order to obtain the real server certificate CN.
- In production environments, a user/host may be temporarily excluded from decryption for this purpose.