Hosts behind the firewall in Alibaba Cloud are unable to reach the Internet
13830
Created On 03/23/20 18:01 PM - Last Modified 12/27/22 20:12 PM
Symptom
- PA-VM is deployed on Alibaba Cloud and traffic from hosts residing in a directly connected subnet is received on and forwarded out of the
firewall however no return traffic is seen.
- Setup the packet filters for the specific source/destination pair under Firewall WebUI: Monitor > Packet Capture
> Configure Filtering > Manager Filters and turn ON Filtering - Run the below CLI command on PA-VM to verify if any packets are received by the firewall:
> show counter global filter delta yes packet-filter yes
name value rate severity category aspect description
--------------------------------------------------------------------------------
pkt_recv 6979948287 46 info packet pktproc Packets received
pkt_sent 24087067 0 info packet pktproc Packets transmitted
session_allocated 21511291 0 info session resource Sessions allocated
session_installed 15969540 0 info session resource Sessions installed
--------------------------------------------------------------------------------
pkt_recv 6979948287 46 info packet pktproc Packets received
pkt_sent 24087067 0 info packet pktproc Packets transmitted
session_allocated 21511291 0 info session resource Sessions allocated
session_installed 15969540 0 info session resource Sessions installed
- Above CLI output shows packets being received on the firewall and forwarded out. If the packets were dropped on the firewall, adopt PAN-OS troubleshooting to isolate it further.
- Check the PAN-OS interface IP vs vNIC IP in Ali cloud
> show interface all
> Navigate to Elastic Compute Service → Click PA VM → Elastic Network Interface 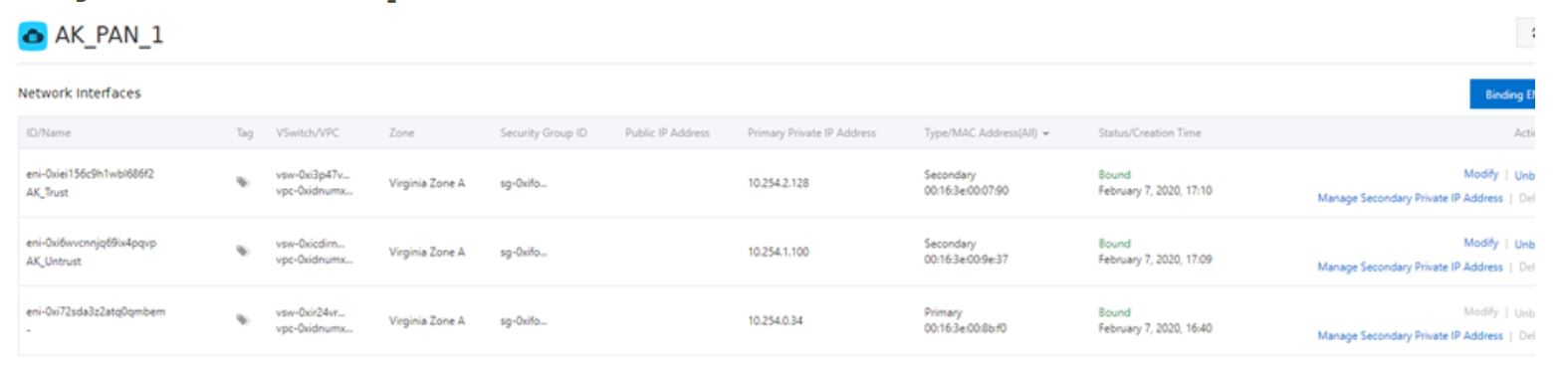
- Since no return traffic is seen under Traffic logs or Session details, the issue can be either on the firewall or on the
egress end, follow below steps to isolate it further:
o Verify if NAT is configured on Firewall
o Verify if default route is configured on Alibaba egress subnet pointing to Internet / NAT Gateway
o Verify if Elastic IP is associated with the Private IP configured on the egress interface
o Verify if Security Group configured for the egress interface is allowing
Environment
- Platform: PA-VM on Alibaba Cloud.
- PAN-OS / Plugin Version: Any
Cause
Egress interface of the firewall instance is not associated with a public IP on Ali Cloud
Resolution
- Create and assign a public IP to the egress interface of firewall instance.
2. Select the newly create IP and click “Bind”
3. Select the instance type as “Secondary ENI”, Mode as “NAT Mode” and under secondary ENI search for Untrust/Egress NIC ID
Note:
o The elastic IP address binds to the ENI as a NAT IP. The ENI supports both public IP address and private IP address.
o You cannot view the elastic IP address in PAN-OS. However, you can use Open API to retrieve the public IP address of a specified ENI.
o NAT mode does not support NAT ALG protocols such as H.323, SIP, DNS, RTSP, TFTP.
o No default route is required in Route Table towards IGW for public IPs to go out to the Internet
o The elastic IP address binds to the ENI as a NAT IP. The ENI supports both public IP address and private IP address.
o You cannot view the elastic IP address in PAN-OS. However, you can use Open API to retrieve the public IP address of a specified ENI.
o NAT mode does not support NAT ALG protocols such as H.323, SIP, DNS, RTSP, TFTP.
o No default route is required in Route Table towards IGW for public IPs to go out to the Internet