Overview
This document describes how to configure User-ID Agent to get User-IP mapping from the Cisco Wireless controller.
Details
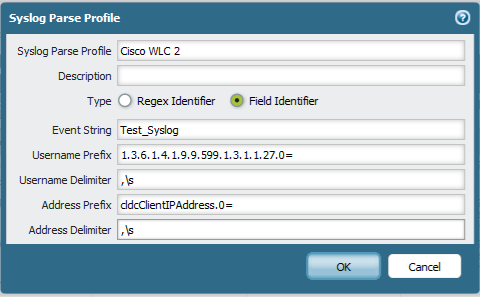
Shown below is a typical example of a syslog from the wireless controller. The bolded fields is the information that will be extracted from the syslog for a successful User-IP mapping when connecting from the Cisco Wireless controller.
9 28.211036 194.36.58.245 192.168.10.248 Syslog 425 LOCAL7.DEBUG: community=Test_Syslog, enterprise=1.3.6.1.4.1.9.9.599.0.4, uptime=384972600, agent_ip=194.36.58.245, version=Ver2, cldcClientMacAddress.0=+;\273t\260\313, cLApName.0=ap-gl-01, cldcApMacAddress.0="Hex String=40 F4 EC 12 3A 40", 1.3.6.1.4.1.9.9.513.1.2.1.1.1.0=1, cldcClientIPAddress.0=10.100.254.157, 1.3.6.1.4.1.9.9.599.1.3.1.1.27.0=rhillcoat, 1.3.6.1.4.1.9.9.599.1.3.1.1.28.0=Howco_Exec
The screenshot below explains how to parse this information and extract the needed details. A Field Identifier is being used instead of Regex
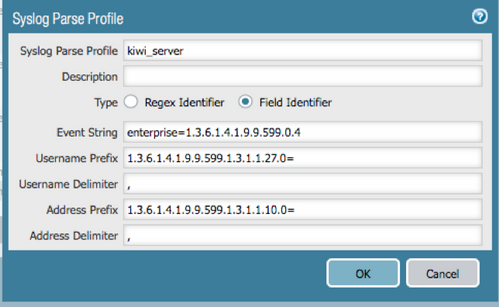
Some versions of Cisco WLC might be sending a slightly different syslog message than the one mentioned above. If your Cisco WLC syslog format looks like the one pasted below (specifically note the highlighted string that holds the IP address of the user) then a different string needs to be configured for the “Address Prefix” value.
07-29-2016 11:32:34 Local7.Debug 10.2.22.31 community=PA_TEST31, enterprise=1.3.6.1.4.1.9.9.599.0.4, uptime=1163840600, agent_ip=10.2.17.39, version=Ver2, 1.3.6.1.4.1.9.9.599.1.3.1.1.1.0="Hex String=44 00 10 2D CC 2D", 1.3.6.1.4.1.9.9.513.1.1.1.1.5.0=MUM04-CSAP11, 1.3.6.1.4.1.9.9.599.1.3.1.1.8.0=P???WP, 1.3.6.1.4.1.9.9.513.1.2.1.1.1.0=0, 1.3.6.1.4.1.9.9.599.1.3.1.1.10.0=10.2.60.62, 1.3.6.1.4.1.9.9.599.1.3.1.1.27.0=corp\user.name1, 1.3.6.1.4.1.9.9.599.1.3.1.1.28.0=CMSPL-11BG
Use the string 1.3.6.1.4.1.9.9.599.1.3.1.1.10.0= in the “Address Prefix” field. See below screenshot for details.
Note that trailing spaces can cause problems in parsing the syslog message. When pasting the text into the “Syslog Parse Profile” window, make sure to delete all spaces at the end of the string.
Note: Make sure the Syslog listener is on the interface that is expected to reach the device. Cisco WLC native Syslog messages do not contain authentication information, so User-ID mappings cannot be derived from them. Cisco WLC generates SNMP Traps that do contain this information. The SNMP Trap must be converted into a Syslog message. To achieve this, please follow document: Cisco WLC - Palo Alto Networks config guide.pdf
owner: smalayappan