The objective of this configuration is to allow GlobalProtect connected users access to the network based on whether they have all patches installed on their Windows host. The hip-profile is associated to a security-policy to allow access, and any missing patches will result in deny of access.
Note: The example configuration creates 2 hip-objects, the first looks for patch severity level greater than zero. The second looks for severity level zero. The two hip-objects are associated to a single hip-profile with 'and' and 'not' condition for each hip-object.
- Example HIP configuration done via the CLI
> configure
# set vsys vsys1 rulebase security rules Trust-Intrust-PING-Allow hip-profiles hip-prof-1
# set vsys vsys1 rulebase security rules Trust-Intrust-PING-Deny hip-profiles any
# set vsys vsys1 profiles hip-objects hip-obj-sev-over-0 patch-management criteria missing-patches check has-none
# set vsys vsys1 profiles hip-objects hip-obj-sev-over-0 patch-management criteria missing-patches severity greater-than 0
# set vsys vsys1 profiles hip-objects hip-obj-sev-over-0 patch-management criteria is-installed yes
# set vsys vsys1 profiles hip-objects hip-obj-sev-over-0 patch-management exclude-vendor no
# set vsys vsys1 profiles hip-objects hip-obj-sev-0 patch-management criteria missing-patches check has-none
# set vsys vsys1 profiles hip-objects hip-obj-sev-0 patch-management criteria missing-patches severity is 0
# set vsys vsys1 profiles hip-objects hip-obj-sev-0 patch-management criteria is-installed yes
# set vsys vsys1 profiles hip-objects hip-obj-sev-0 patch-management exclude-vendor no
# set vsys vsys1 profiles hip-profiles hip-prof-1 match 'not "hip-obj-sev-over-0" and not "hip-obj-sev-0"'
- Example HIP configuration done via the GUI
- Create the first hip-object by navigating to Objects > GlobalProtect > HIP Objects > Select "Add"
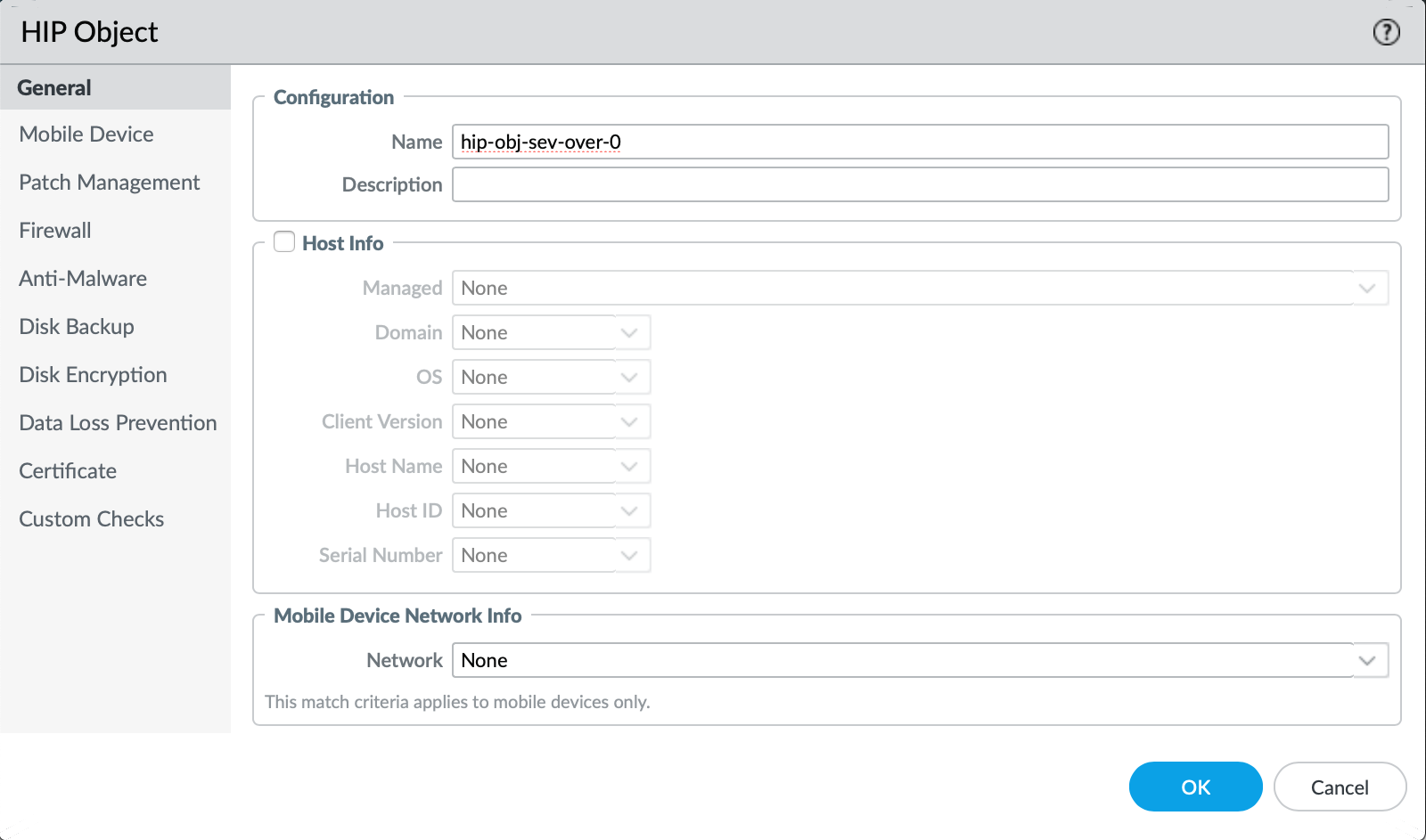
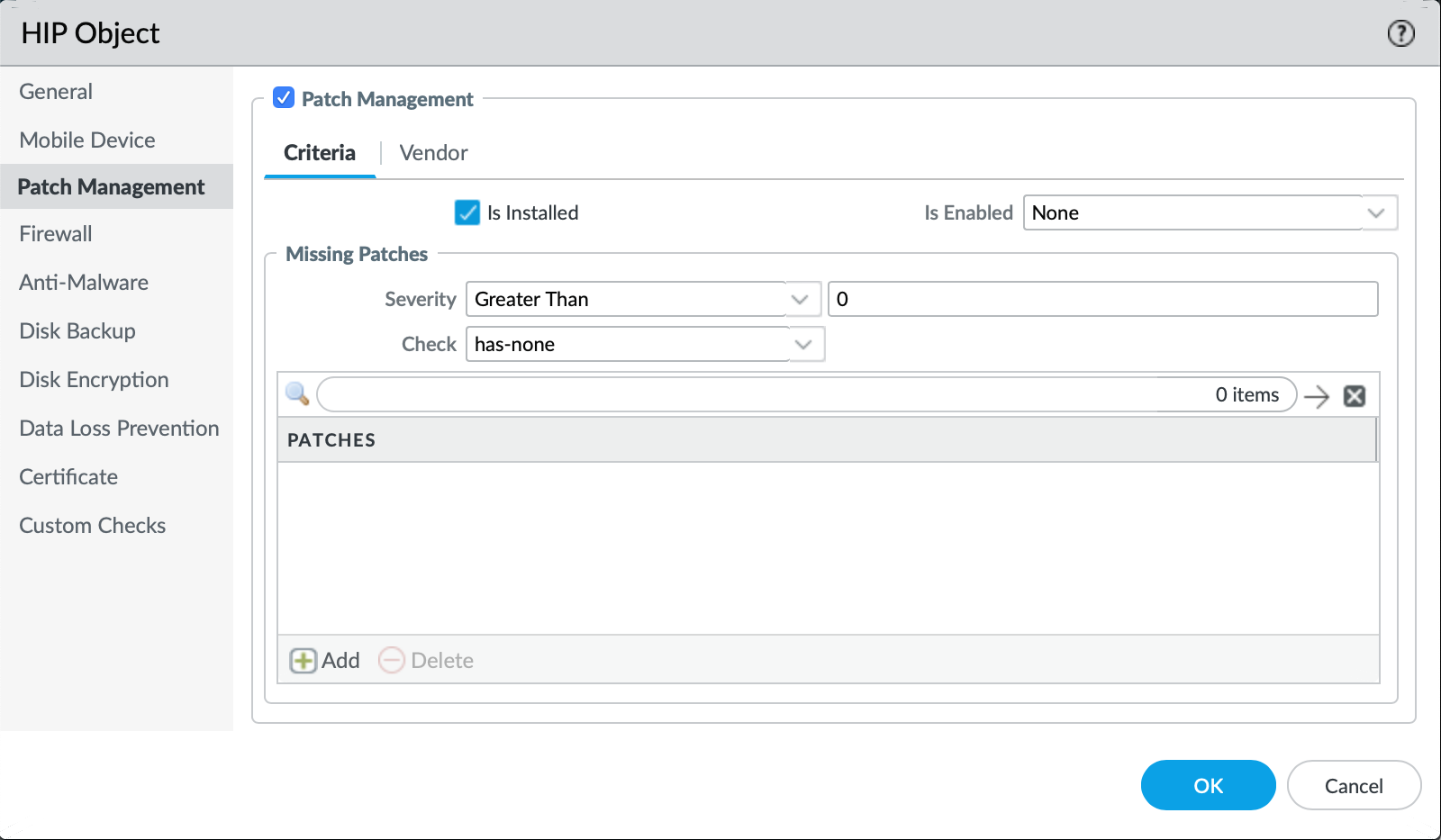
- Define the parameters for severity level greater than zero for the "Patch Management" tab and select OK once finished
- Create the second hip-object by selecting "Add"
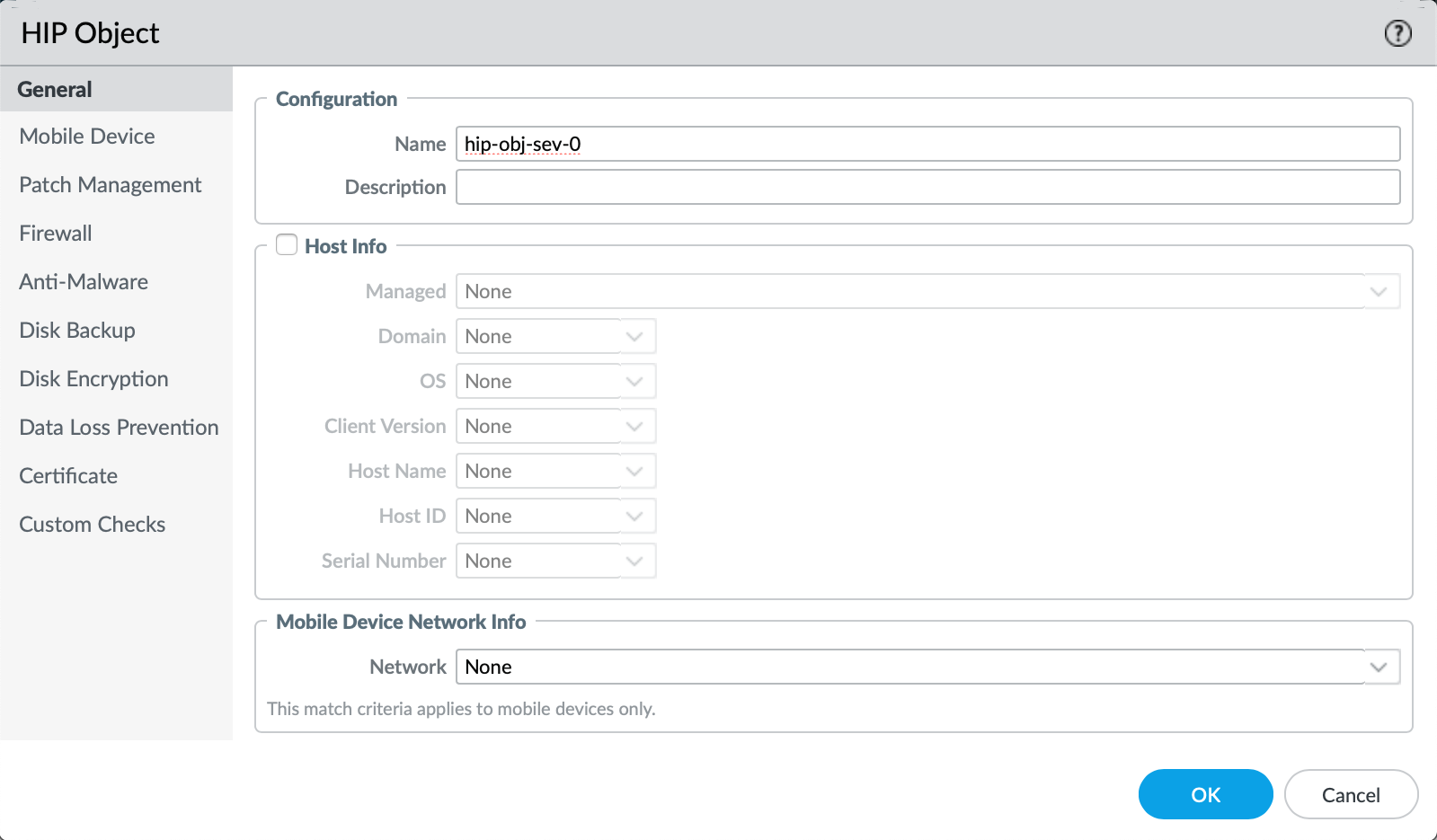
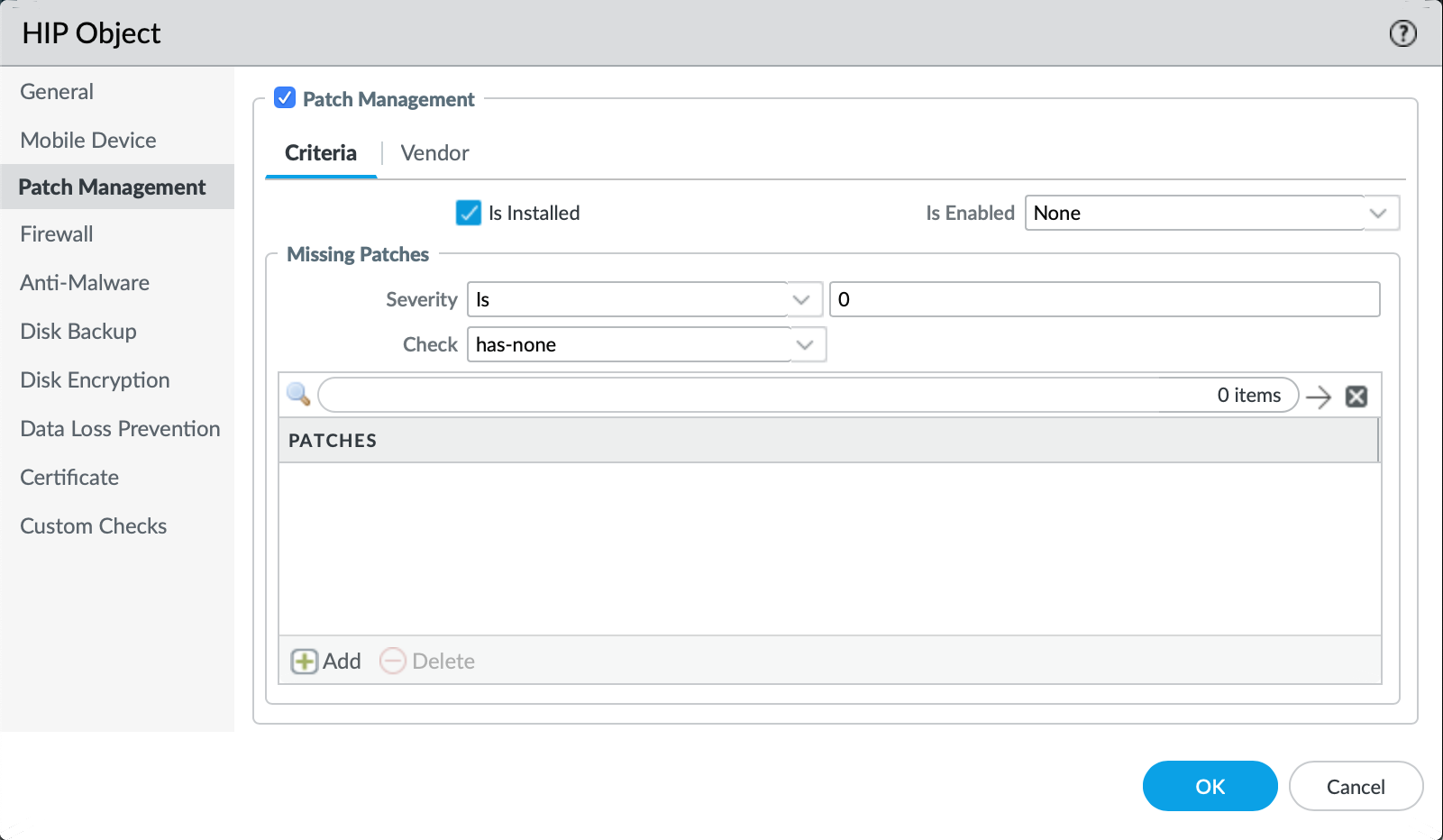
- Define the parameters for severity level equal to zero for the "Patch Management" tab
- Associate the 2 hip-objects to a single hip-profile with “AND NOT” conditions by navigating to Objects > GlobalProtect > HIP Profiles > Select “Add”
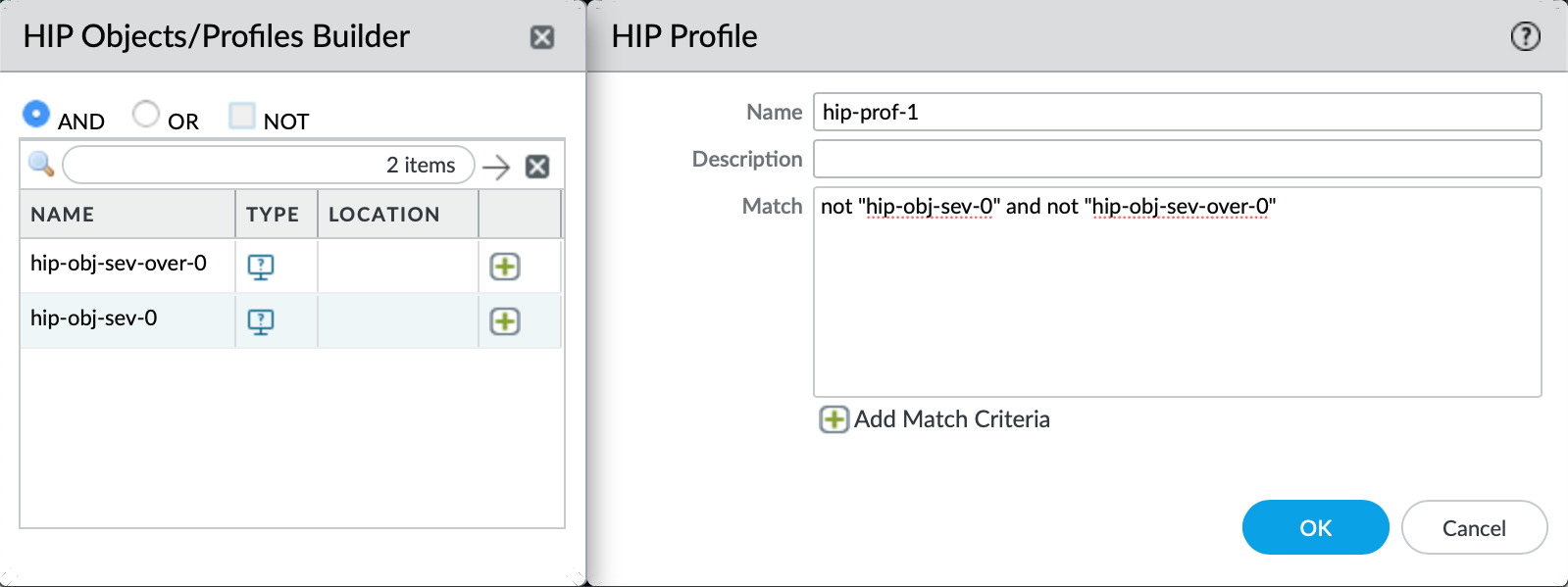
Note: If you wish to allow patches of severity level zero to be ignored, do not include the hip-object named “hip-obj-sev-0” in the hip-profile.
- Create a security-policy to allow access.
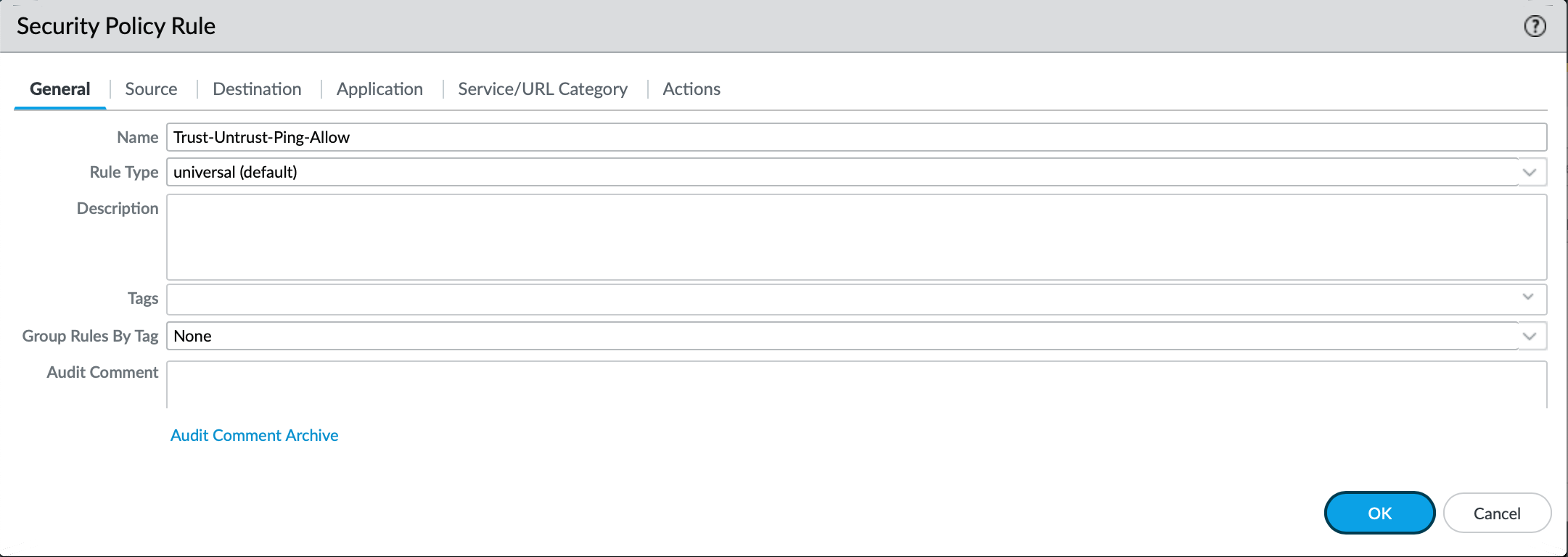
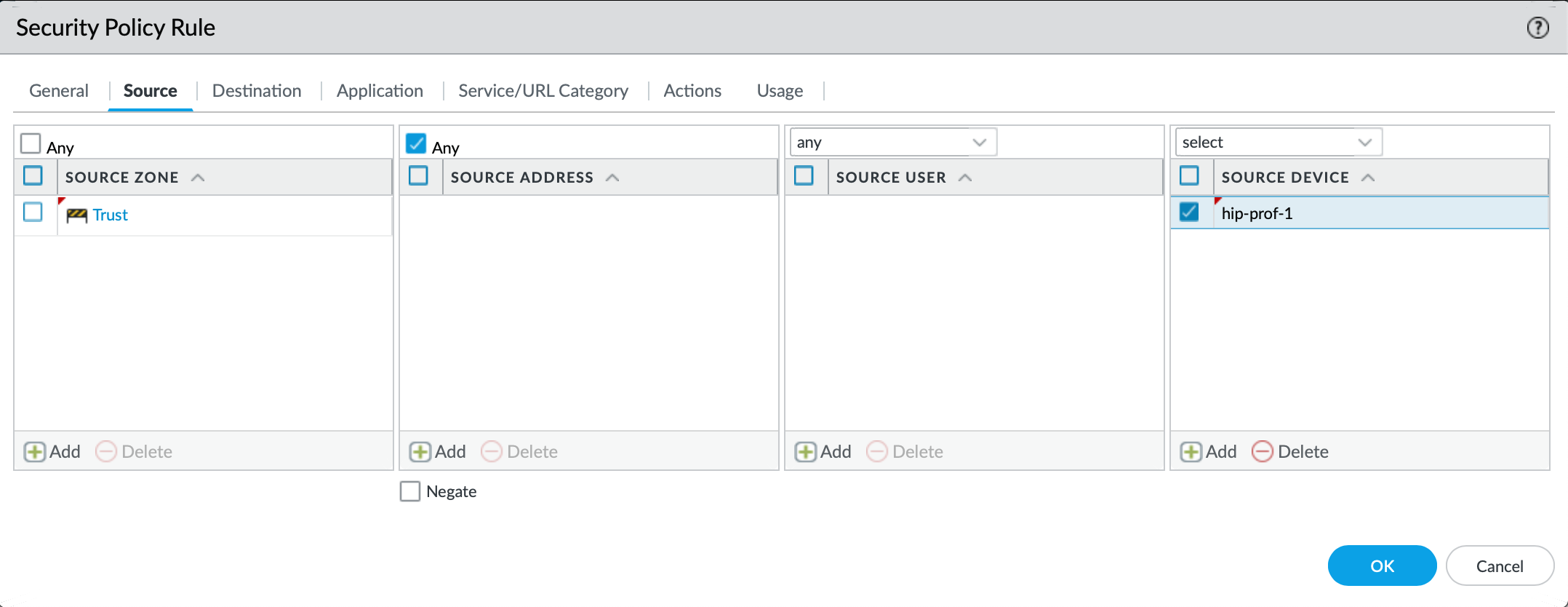
- Associate the single hip-profile to the security-policy.
- Possible Troubleshooting Ideas:
- Review the hipmatch log from the WebUI and identify which hip-objects are matched
- Review the attributes of each matched hip-object to determine accuracy.
- Moving on to debug commands:
> debug user-id dump hip-profile-database entry
> debug user-id dump hip-report computer <computer-name> ip <global-protect-assigned-ip> user <username>
- To gain greater visibility, the hip debugs can be enabled via the CLI commands below. The messages are printed to the 'useridd.log' file.
> debug user-id set hip all
> debug user-id on debug
> tail follow yes mp-log useridd.log
Note: The example below shows the hip-object evaluation in the useridd.log. After the initial evaluation, at 22:11:55.219 the <hip-notification> message is sent to the client, reflecting a match.
2016-03-01 22:11:55.219 -0800 debug: pan_hip_obj_evaluate_report(pan_hip_obj.c:3121): evaluating obj 'hip-obj-sev-over-0' for report 'TEMPLATE-PC'
2016-03-01 22:11:55.219 -0800 debug: pan_hip_obj_category_evaluate_report_xml(pan_hip_obj.c:2581): validating category 'patch-management' from report 'TEMPLATE-PC'
2016-03-01 22:11:55.219 -0800 debug: pan_hip_obj_category_evaluate_node(pan_hip_obj.c:2548): match 0 check is not passed
2016-03-01 22:11:55.219 -0800 debug: pan_hip_obj_simple_evaluate_report(pan_hip_obj.c:3095): category 'patch-management' evaluate failed for 'TEMPLATE-PC'
2016-03-01 22:11:55.219 -0800 debug: pan_hip_obj_evaluate_report(pan_hip_obj.c:3132): obj 'hip-obj-sev-over-0' for report 'TEMPLATE-PC' evaluated : 0
2016-03-01 22:11:55.219 -0800 debug: pan_hip_evaluate_report(pan_hip.c:1255): customer report evaluation : 0x2
2016-03-01 22:11:55.219 -0800 debug: pan_hip_evaluate_report(pan_hip.c:1276): for hip report 'TEMPLATE-PC', notification: <hip-notification>
<entry name="hip-prof-1"><value>1</value><message><b>HIP MATCHES !!!!!!</b></message><show-notification-as>pop-up-message</show-notification-as></entry>
2016-03-01 22:11:55.219 -0800 debug: pan_hip_evaluate_report(pan_hip.c:1291): for hip report 'TEMPLATE-PC', notification: <hip-notification>
<entry name="hip-prof-1"><value>1</value><message><b>HIP MATCHES !!!!!!</b></message><show-notification-as>pop-up-message</show-notification-as></entry>