Authenticated User-ID with GlobalProtect for Internal Network Segmentation (PAN-OS 7.1 & GlobalProtect 3.1)
91959
Created On 09/26/18 19:12 PM - Last Modified 05/23/23 00:39 AM
Environment
PAN-OS 7.1
GlobalProtect 3.1
Resolution
This document was created based on PAN-OS 7.1 and GlobalProtect 3.1 and will not be updated for later versions.
Background
User-ID™ enables you to identify all users on your network and by doing that, it provides visibility into application usage based on users and gives you the ability to enforce security policies based on users and/or user-groups. Though User-ID™ could be obtained using a variety of techniques, GlobalProtect is one of the most reliable sources of User-ID. To obtain User-ID through GlobalProtect in an internal network, GlobalProtect must be deployed in user-logon or pre-logon mode and with internal gateways. GlobalProtect keeps the User-ID up to date by automatically re-authenticating the user every time there is a network status change on the endpoint.
Purpose
Network adapter status on the endpoint could change for several reasons such as the endpoint waking up from sleep, system reboots or users signing back in. All of these would trigger GlobalProtect to re-authenticate the user. Prompting the user for credentials on every such occasion would lead to poor user experience. So, it is recommended to always require some form of seamless authentication to internal gateways. This document describes different ways of achieving seamless and transparent authentication to GlobalProtect internal gateways.
Transparent Authentication to GlobalProtect
Transparent authentication to GlobalProtect can be achieved by using one of the following methods:
- Client Certificates (available on all supported platforms)
- Kerberos service tickets (supported on Windows (starting GlobalProtect 3.0) & on Mac (starting GlobalProtect 4.1))
- Windows Credential Providers and
- Saved User Credentials (available on all supported platforms)
- Authentication Override Cookies (available on all supported platforms)
Authenticate using Certificates
When GlobalProtect is configured to authenticate using client certificates, the endpoint must present a valid client certificate that matches the Certificate Profile. This client certificate must contain the user information either in the Subject or Subject Alt fields. Upon successful authentication, GlobalProtect would retrieve the Username from the client certificate and update the User-ID. It should be noted that certificate authentication would be transparent as long as there is only one client certificate that matches the Certificate Profile. The agent automatically uses that client certificate for authentication. However, when multiple client certificates meet the Certificate Profile requirements, GlobalProtect prompts the user to select one from a list of valid client certificates on the endpoint. While GlobalProtect requires users to select the client certificate only during the very first connection, users might not know which certificate to pick to complete the authentication. To make it seamless and not confuse the user, it is recommended that you narrow the list of available client certificates that matches the Certificate Profile by specifying the certificate purpose (as indicated by the OID).
Here is a short demo on sample configuration and end user experience with Certificate authentication:
To know how to configure Certificate Selection by OID and how that improves user experience, watch this video:
Authenticate using Kerberos
When GlobalProtect is configured with Kerberos authentication, GlobalProtect agent uses Kerberos service ticket obtained from the Key Distribution Center (KDC) to seamlessly authenticate the end user. Only if Kerberos Single Sign-On (SSO) fails, user will be prompted for credentials. The type of credentials user needs to provide (when prompted) depends on the Authentication Profile set on the portal / gateway. Kerberos authentication in GlobalProtect is available on Windows & Mac endpoints only. Here is an example on how to generate the Keytab file for internal gateways int-gw1.acme.com and int-gw2.acme.com In Windows PowerShell, use ktpass command to create the KeyTab file. These are three separate commands, to make 3 keytab files. Make sure to use uppercase ACME.COM as highlighted below.
ktpass -princ HTTP/portal.acme.com@ACME.COM -mapuser gpuser -ptype KRB5_NT_PRINCIPAL -pass mypassword -out C:\Users\Administrator\Desktop\portal.keytab ktpass -princ HTTP/int-gw1.acme.com@ACME.COM -mapuser gpuser -ptype KRB5_NT_PRINCIPAL -pass mypassword -out C:\Users\Administrator\Desktop\int-gw1.keytab ktpass -princ HTTP/int-gw2.acme.com@ACME.COM -mapuser gpuser -ptype KRB5_NT_PRINCIPAL -pass mypassword -out C:\Users\Administrator\Desktop\int-gw2.keytab
Here is a short demo on sample configuration and end user experience with Kerberos authentication:
Authenticate using Windows SSO
GlobalProtect SSO on Windows allows GlobalProtect agents to use Windows login credentials to authenticate with the GlobalProtect portal and gateway. GlobalProtect uses Microsoft's credential provider framework to collect the user's login credentials during the Windows login and transparently authenticate the user to the GlobalProtect portal and gateway.
Authenticate using Saved User Credentials
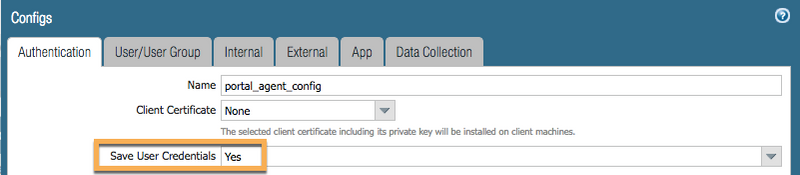
GlobalProtect can be configured to remember the username and password the user provides at the time of first connection. For subsequent connections, GlobalProtect uses the saved credentials to provide seamless authentication. If the user updates the password anytime, GlobalProtect authentication using saved credentials would fail and the user would get prompted for credentials. Upon successful authentication using the new password, GlobalProtect saves those credentials and uses the updated credentials for subsequent connections. GlobalProtect supports saving of user credentials on all supported endpoints.
Authenticate using Authentication Override Cookies
GlobalProtect (starting with PAN OS 7.1 and GlobalProtect 3.1) offers Authentication Override, a feature that minimizes the number of times a user gets prompted for authentication. This feature allows GlobalProtect to obtain an encrypted cookie from portal and/or gateway upon successful authentication and use this cookie for subsequent authentication Users can experience seamless authentication as long as this cookie is valid.