Scenario
After deploying Agentless User-ID, the security logs on the Windows Domain Controller are heavily populated with Event ID 4776, causing the Windows security log to overwrite itself frequently.
Issue
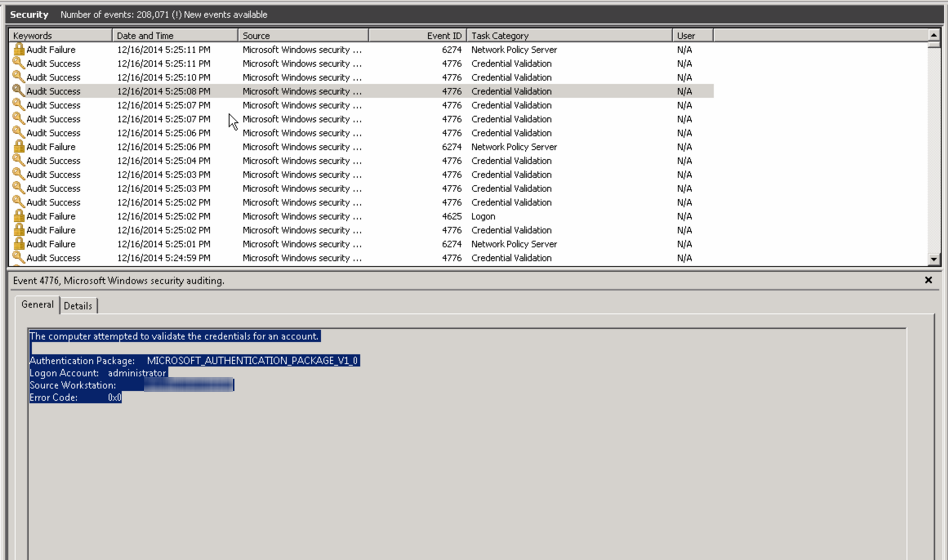
Event ID 4776 is the "Account Used for Logon" event in Windows 2008. When Agentless User-ID is configured the event logs can become heavily populated with Event ID 4776 because it logs each time the firewall checks in to the server. The default setting for the PAN-OS to check in is 2 seconds. This can cause the security logs to be overwritten more frequently thus causing more CPU utilization to keep up with the log rate.
Allowing this to perpetuate could cause CPU resources to elevate which could potentially degrade User-ID accuracy, and impact end user productivity as well. Although Event ID 4776 may be useful if your Agentless User-ID deployment is having issues communicating with AD, this event is not needed. In Windows 2008, the security log events needed for User-ID are:
- 4624 - Logon Success
- 4768 - Authentication Ticket Granted
- 4769 - Service Ticket Granted
- 4770 -Ticket Granted Renewed
Resolution
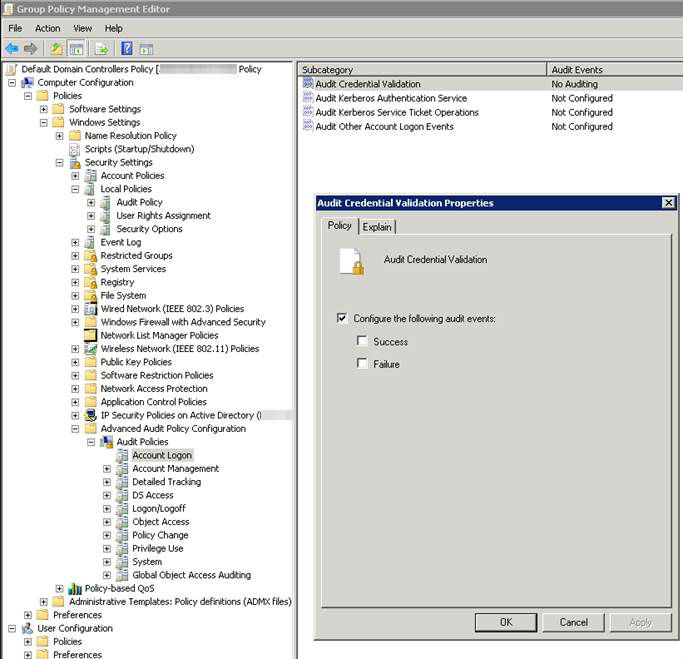
1. To resolve this issue, open the Group Policy Management Tool within Windows
2. Navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Account Logon\
3. In the "Account Logon" Subcategory select "Audit Credential Validation" and configure it for "No Auditing"