Overview
This document describes the CLI commands that can be used to verify a successful connection to the LDAP server for pulling groups.
Details
During LDAP server configuration, the device automatically pulls the Base DN if the connection is successful. The Base and Bind DN are configured under Device > Server Profiles > LDAP:
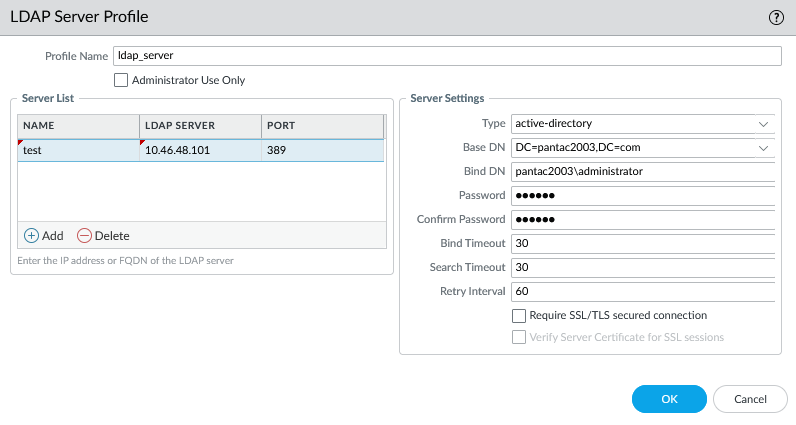
Use the show user group-mapping state all command to view the LDAP connectivity if using the server profile for group mapping.
For example:
> show user group-mapping state all
Group Mapping (vsys1, type: active-directory) : grp_mapping
Bind DN : pantac2003\adminatrator
Base : DC=pantac2003,DC=com
Group Filter: (None)
User Filter: (None)
Servers : configured 1 servers
10.46.48.101 (389)
Last Action Time: 2290 secs ago(took 71 secs)
Next Action Time: In 1310 secs
Number of Groups: 121
cn=administrators,cn=builtin,dc=pantac2003,dc=com
cn=ras and ias servers,cn=users,dc=pantac2003,dc=com
cn=s,cn=users,dc=pantac2003,dc=com
If the Bind DN entered on the Palo Alto Networks device under Device > Server Profiles > LDAP is incorrect, the output of the command will display "invalid credentials".
The example output below shows a scenario in which "cn=Administrator12" was entered, but the correct value was "cn=Administrator":
> show user group-mapping state all
Group Mapping (vsys1, type: active-directory) : grp_mapping
Bind DN : CN=Administrator12,CN=Users,DC=pantac2003,DC=com
Base : DC=pantac2003,DC=com
Group Filter: (None)
User Filter: (None)
Servers : configured 1 servers
10.46.48.101 (389)
Last Action Time: 0 secs ago(took 0 secs)
Next Action Time: In 60 secs
Last LDAP error: Invalid credentials
Number of Groups: 0
Errors can be pulled from the useridd log using the following command:
> less mp-log useridd.log
Dec 30 15:59:07 connecting to ldap://[10.46.48.101]:389 ...
Dec 30 15:59:07 Error: pan_ldap_bind_simple(pan_ldap.c:466): ldap_sasl_bind result return(49) : Invalid credentials
Dec 30 15:59:07 Error: pan_ldap_ctrl_connect(pan_ldap_ctrl.c:832): pan_ldap_bind() failed
Dec 30 15:59:07 Error: pan_gm_data_connect_ctrl(pan_group_mapping.c:994): pan_ldap_ctrl_connect(grp_mapping, 10.46.48.101:389) failed
Dec 30 15:59:07 Error: pan_gm_data_connect_ctrl(pan_group_mapping.c:1061): ldap cfg grp_mapping failed connecting to server 10.46.48.101 index 0
Dec 30 15:59:07 Error: pan_gm_data_ldap_proc(pan_group_mapping.c:1942): pan_gm_data_connect_ctrl() failed
Dec 30 15:59:14 Warning: pan_ldap_ctrl_construct_groups(pan_ldap_ctrl.c:546): search aborted
Dec 30 15:59:16 Error: pan_ldap_ctrl_query_group_membership(pan_ldap_ctrl.c:2384): pan_ldap_ctrl_construct_groups() failed
Dec 30 15:59:16 Error: pan_gm_data_update(pan_group_mapping.c:1431): pan_ldap_ctrl_query_group_membership() failed
Dec 30 15:59:16 Error: pan_gm_data_ldap_proc(pan_group_mapping.c:1976): pan_gm_data_update() failed
Dec 30 16:00:07 connecting to ldap://[10.46.48.101]:389 ...
Dec 30 16:00:07 Error: pan_ldap_bind_simple(pan_ldap.c:466): ldap_sasl_bind result return(49) : Invalid credentials
Dec 30 16:00:07 Error: pan_ldap_ctrl_connect(pan_ldap_ctrl.c:832): pan_ldap_bind() failed
Dec 30 16:00:07 Error: pan_gm_data_connect_ctrl(pan_group_mapping.c:994): pan_ldap_ctrl_connect(grp_mapping, 10.46.48.101:389) failed
Command to re-establish the link to the LDAP server
debug user-id reset group-mapping <grp_mapping_name>
Command to set LDAP to debug
debug user-id set ldap all
Command to turn on debug
debug user-id on debug
Command to turn off debug
debug user-id off
Command to capture LDAP traffic if using management port
tcpdump filter "port 389"
Command to capture LDAPS (SSL) traffic if using management port
tcpdump filter "port 636"
Command to view the pcap taken off the management port
view-pcap mgmt-pcap mgmt.pcap
Command to export the pcap to an external host by scp or tftp
scp export mgmt-pcap from mgmt.pcap to username@host:path
tftp export mgmt-pcap from mgmt.pcap to <tftp host>
owner: sdarapuneni