Details
This document is designed to help verify if the DNS Sinkhole function is working properly through a Palo Alto Networks firewall.
The following 2 scenarios are covered:
- Client Using External DNS Server
- Client Using Internal DNS Server
DNS Sinkhole Configuration
For information on How to Configure DNS Sinkhole, please see:
How to Configure DNS Sinkhole
Also, we have a Video Tutorial on How to Configure DNS Sinkhole:
Video Tutorial: How to Configure DNS Sinkhole
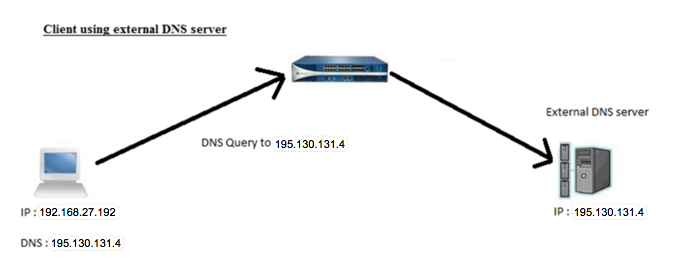
Client Using External DNS Server
Note: DNS Sinkhole IP must be in the path of the firewall and the client so you can see logs from it. For example, the Palo Alto Networks firewall sits between an infected client and the data center, but it does not see the internet. In this scenario, if DNS Sinkhole is configured with an internet IP, then the firewall will never see the infected client trying to reach its command & control server.
When the DNS sinkhole feature is configured on the Palo Alto Networks firewall and the client system is using an external DNS server, the DNS query from the client will go through the Palo Alto Networks firewall to the external DNS server (client and DNS server are in different subnets). As expected, the user should be able to see threat logs with the client IP address as a source.
- The user is trying to access a malicious website. The client system will send the DNS query to an external DNS server to get the IP address of the malicious website. The firewall will receive the DNS query directly from the client system.
- The firewall will hijack the DNS query and will give a DNS sinkhole IP address to the client and should be able to see the threat logs with client IP address as a source.
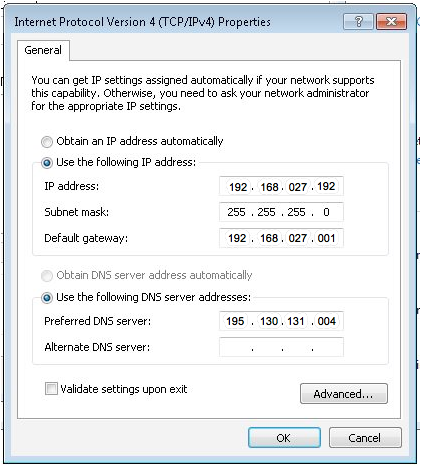
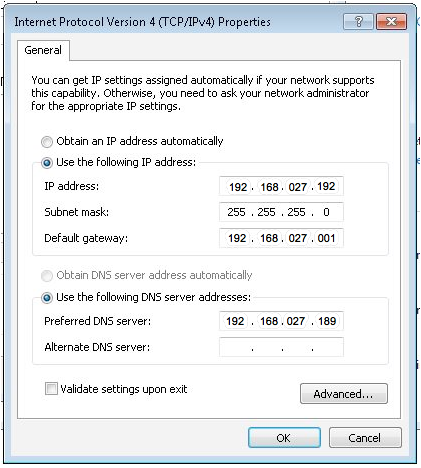
Client TCP/IP Properties Configuration
Review the following config example:
Threat Logs
When using an external DNS server, Threat logs show the Client IP address "192.168.27.192" as a source that is trying to access a malicious website: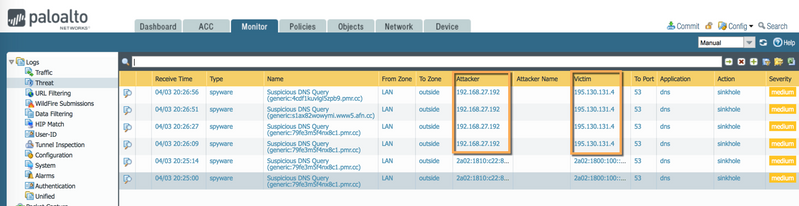
Client Output When Using External DNS Server
$ nslookup 79fe3m5f4nx8c1.pmr.cc
Server: 195.130.131.4
Address: 195.130.131.4#53
Non-authoritative answer:
Name: 79fe3m5f4nx8c1.pmr.cc
Address: 72.5.65.111
The screenshot above shows a host machine 192.168.27.192 performing a DNS request for "79fe3m5f4nx8c1.pmr.cc" (a suspicious URL) and the response being 72.5.65.111. Thus showing that the DNS Sinkhole is working as desired.
Client Using Internal DNS Server
If a client system is using an internal DNS server (client and DNS server are in the same subnet), the DNS query from the client will go to the internal DNS server. The internal DNS server will forward this query to an external DNS server, and threat logs with the internal DNS server IP address will be seen as a source.
Currently, the Palo Alto Networks firewall cannot identify which end client is trying to access a malicious website with the help of the threat logs, because all threat logs will have the internal DNS server IP address as a source. However, the firewall should be able to determine the end client IP address with the help of traffic logs.
Below is an example where the user is trying to access a malicious website. The client system will send the DNS query to an internal DNS server to acquire the IP address of the malicious website. Here, the internal DNS server will forward the DNS query to an external DNS server. The firewall will receive a DNS query from the internal DNS server.
The firewall will hijack the DNS query and give the DNS sinkhole IP address to the Internal DNS server. The internal DNS server will forward the response to the client system and the user should be able to see threat logs with Internal DNS server IP address as a source. However, Palo Alto Networks firewall should able to see client IP address in the traffic logs because client will try to access that website with DNS sinkhole IP address, as shown in the following screenshot: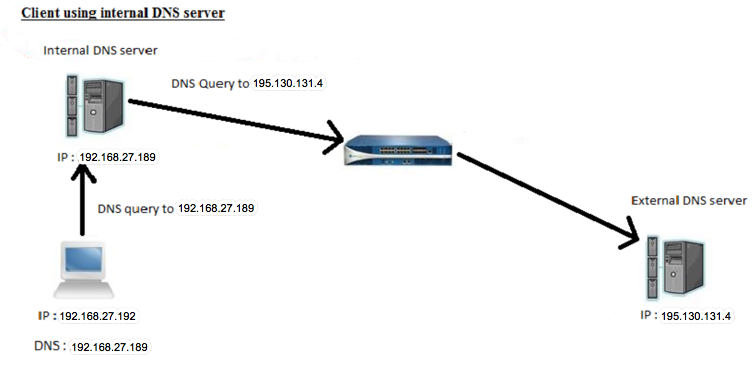
Client TCPIP properties configuration
Threat Logs
In threat logs, the firewall shows only the internal DNS server IP address "10.50.240.101" as a source, because the client system is using the internal DNS server IP. Here the firewall is not able to determine which end client is trying to access that website.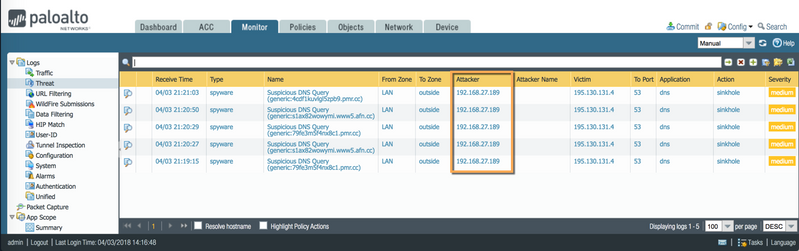
Traffic Logs
However, as soon as client get the IP address from DNS server, it will generate traffic towards the sinkhole IP address(72.5.65.111). Therefore, the firewall will show the end client IP address "192.168.27.192" in traffic logs, as shown below: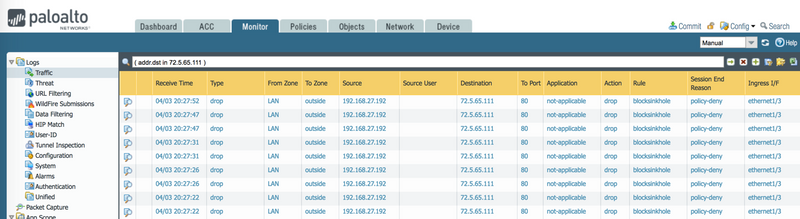
Client Output When Using Internal DNS Server
$ nslookup 4cdf1kuvlgl5zpb9.pmr.cc
Server: 192.168.27.189
Address: 192.168.27.189#53
Non-authoritative answer:
Name: 4cdf1kuvlgl5zpb9.pmr.cc
Address: 72.5.65.111
The screenshot above shows a host machine 192.168.27.192 performing a DNS request for 4cdf1kuvlgl5zpb9.pmr.cc (a suspicious URL) with the response of 72.5.65.111. This verifies that the DNS Sinkhole is working as desired.