Details
When translating proxy IDs over IPsec tunnels using NAT, pointing the routes of the NAT-translated IPs through the tunnel interfaces is required.
The diagram is a typical setup where customers hide private IP addresses on their sites by using public addresses and NAT. (For a larger image, see the attachment below.)
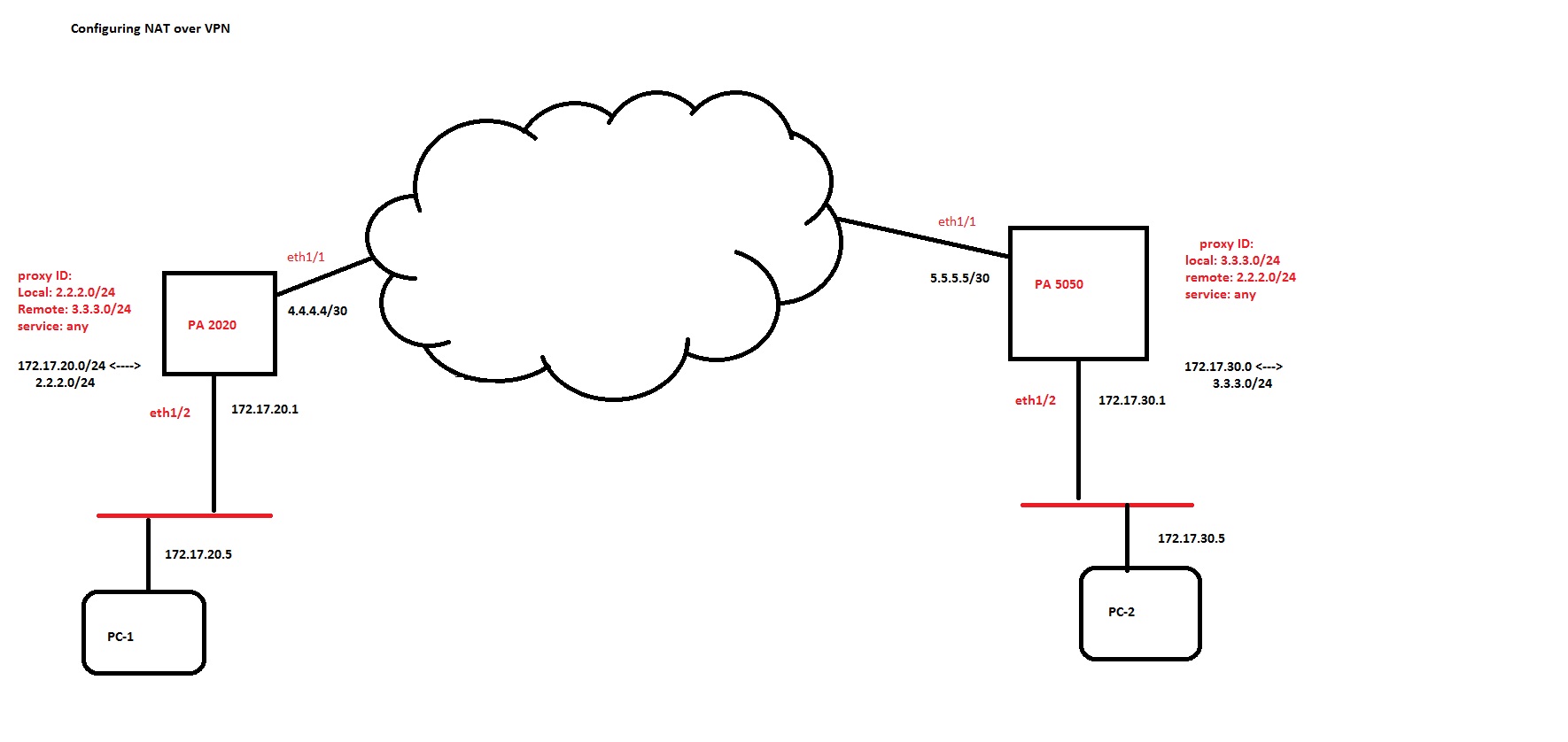
On the PA 2020:
172.17.20.0/24 is NATed out to the 2.2.2.0/24 network.
On the PA 5050:
172.17.30.0/24 is NATed out to the 3.3.3.0/24 network.
NAT need not always be a one-to-one mapping. Customers can also deploy port-based translation to single public IP addresses. These IP addresses are used as proxy IDs for the VPN. Per the PAN-OS session setup, the firewall decrypts the ESP packet, then performs the forwarding lookup for both the source IP and the destination IP, of the inside packet, to determine the interface and the zone for both IP addresses. If the route to these IP addresses is not pointed to the tunnel interface, the forwarding lookup points the addresses to the default gateway (assuming there is neither a static route configured for these IP addresses or that they're being learned dynamically). As both IP addresses have routes pointing to the untrust interface and the untrust zone, it doesn't match the policy permitting traffic from the zone that the tunnel interface belongs to, so the packets get dropped.
The route configurations required in addition to NAT and VPN settings are:
admin@PA-2020# set network virtual-router default routing-table ip static-route local-site-NAT destination 2.2.2.0/24 interface tunnel.1
admin@PA-2020# set network virtual-router default routing-table ip static-route local-site-NAT destination 3.3.3.0/24 interface tunnel.1
Similarly, the route configuration on the other firewall would look like:
admin@PA-5050# set network virtual-router default routing-table ip static-route local-site-NAT destination 3.3.3.0/24 interface tunnel.1
admin@PA-5050# set network virtual-router default routing-table ip static-route local-site-NAT destination 2.2.2.0/24 interface tunnel.1