Communication between two vsys via a transit vsys is not supported. Packet will be dropped by the firewall. Flow basic will show "packet dropped, from/to zone unavailable for policy lookup" Firewall will not be able to find the destination zone.
Workaround
Lets say vsys1 wants to communicate to vsys 2 via vsys3.
Move the traffic from vsys1 to vsys3 and then out of the firewall. Now bring back the traffic from outside of the firewall to vsys3 and then to vsys2.
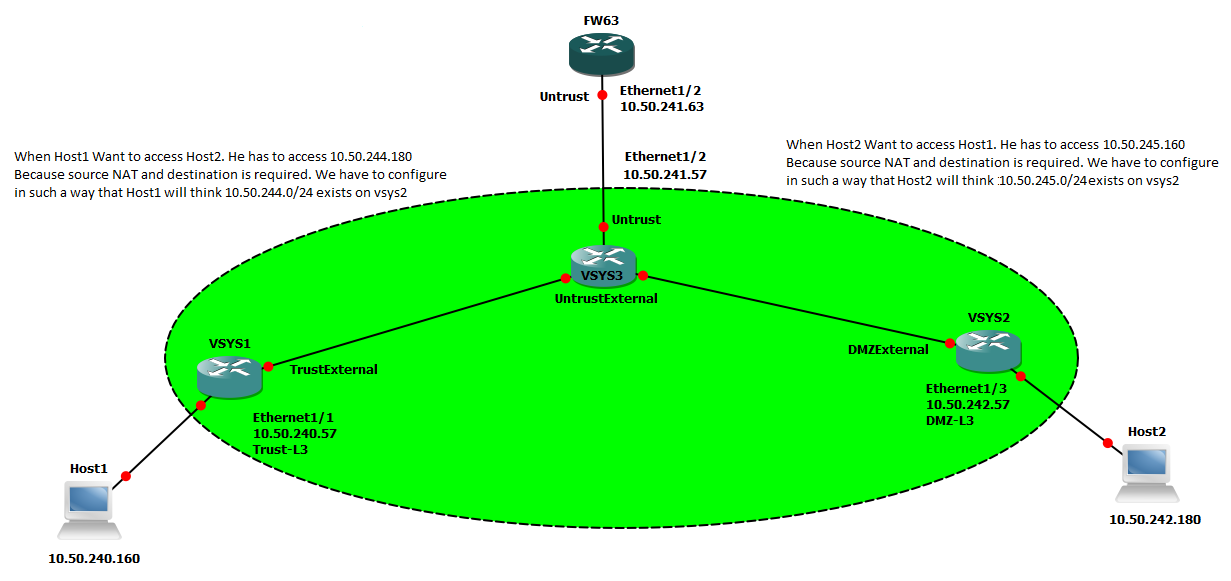
When Host1 tries to ping "ping 10.50.242.180" Host ping does not work. The traffic will be dropped by the firewall. In order to make this work we have to do source + destination NAT on FW63 (using the topology above) and Host1 should ping to 10.50.244.180.
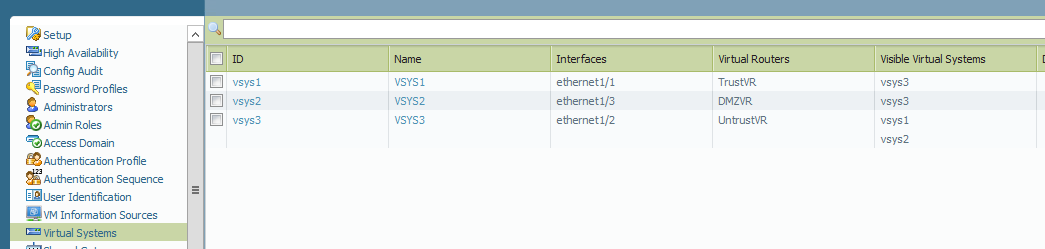
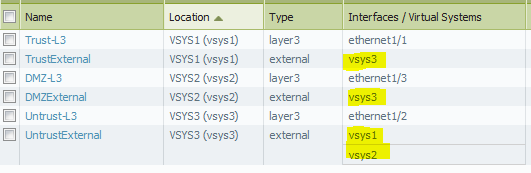
- VSYS1 has one external zone TrustExternal, one Trust-L3 zone, TrustVR. VSYS1 has visisbility to VSYS
- VSYS2 has one external zone DMZExternal, one DMZ-L3 zone, DMZVR. VSYS2 has visisbility to VSYS3
- VSYS3 has one external zone UntrustExternal one Untrust zone, UntrustVR. VSYS2 has visisbility to VSYS1, VSYS3
VSYS are configured as follows:
Zones are configured as follows:
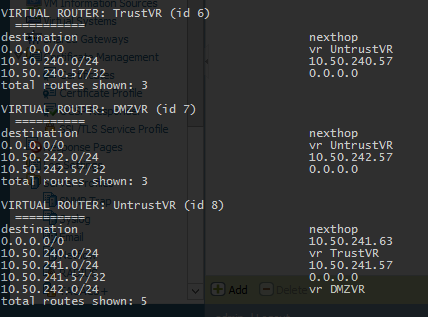
DMZVR, TrustVR have a default route pointing towards UntrustVR. UntrustVR has a return route for 10.50.240.0/24 pointing towards TrustVR. UntrustVR has a return route for 10.50.242.0/24 pointing towards DMZVR :
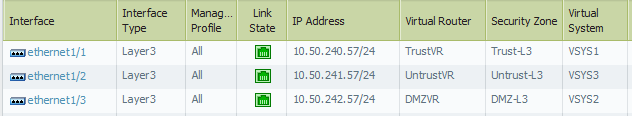
Interfaces are configured as follows:
Security polices
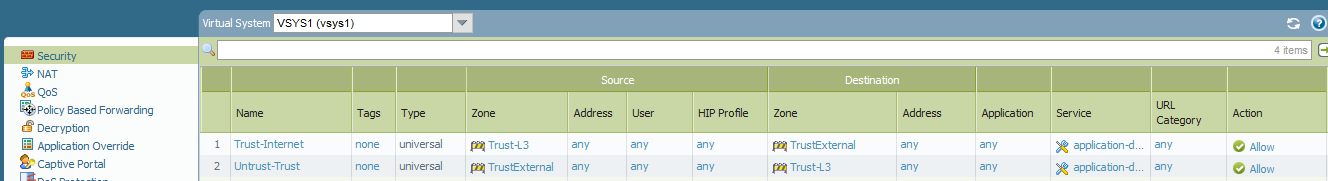
VSYS1 has the following security policy to allow inbound and outbound traffic:
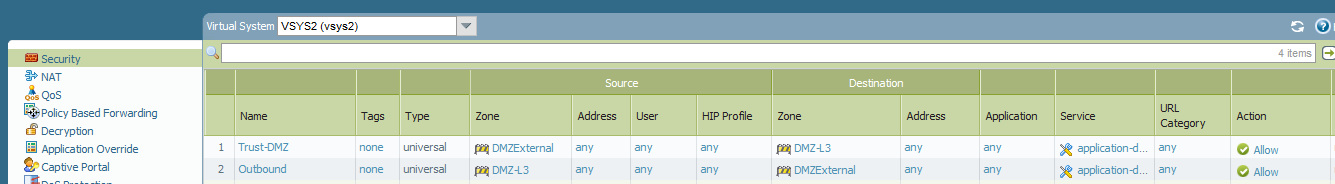
VSYS2 has the following security policy to allow inbound and outbound traffic:
VSYS3 has following security policy to allow inbound and outbound traffic:
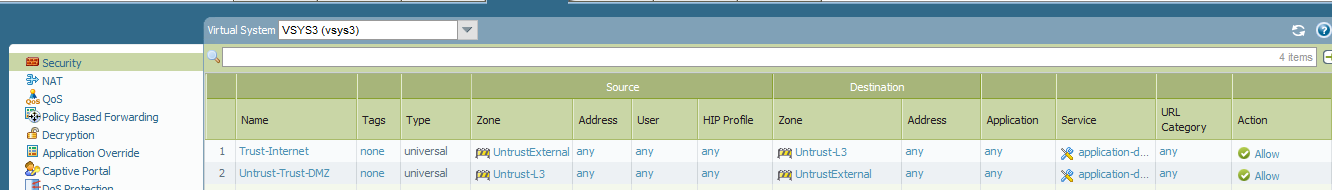
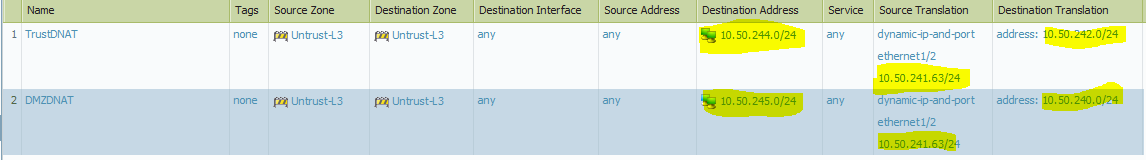
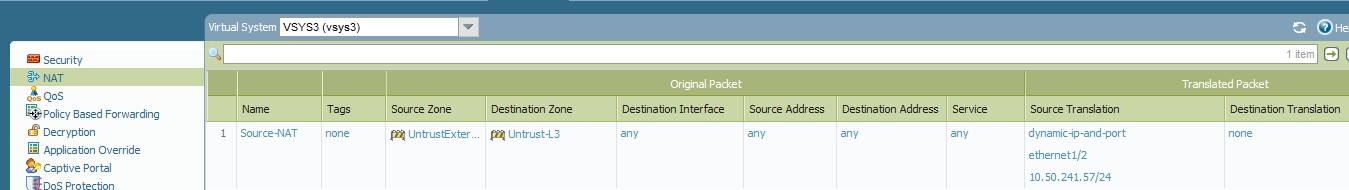
VSYS3 source NAT:
Now we have to add 4 routes on FW63 Original subnet 10.50.240.0/24, 10.50.242.0/24 and NATed subnet 10.50.244.0/24, 10.50.245.0/24 pointing back to VSYS3:
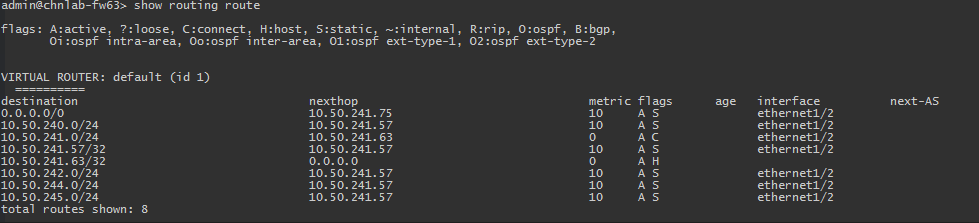
NAT rule on FW63
When FiW63 receives a ping initiated from Host1 the source of that traffic will be 10.50.241.57 and the destination will be 10.50.244.180. Now we have to change the destination to 10.50.242.180 so that VSYS3 send traffic to Host2. We have to source NAT to FW63's interface IP. If the source NAT is not done then the VSYS firewall will drop the traffic because the return traffic will have source 10.50.242.180 and destination will be 10.50.241.57.